SecPro #05: Bruteforcing SSH with Metasploit; Resources Abound!
Hey,
Bruteforcing SSH with Metasploit & Resources abound in this week’s issue of SecPro! From new malware to bruteforcing SSH with Metasploit, and from zero trust to observability, there’s some meaty content to dig in!
As always, I’d love to hear your thoughts and feedback on this issue.
If you find this newsletter useful and know other people who would too, I’d really appreciate if you’d forward it to them. Thanks for reading!
In this Issue:
This Week in Security
- Large-Scale Crpytomining Attacks Hit Kubeflow: Microsoft has spotted a new, widespread, ongoing attack targeting Kubernetes clusters running Kubeflow instances, in order to plant malicious TensorFlow pods that are used to mine for cryptocurrency.
- Look out for SteamHide! An emerging malware that disguises itself inside profile images on the gaming platform Steam, is presumably being developed for a wide-scale campaign.
- Siloscape Malware Targets Windows Containers: Siloscape is a heavily obfuscated malware targeting Kubernetes clusters through Windows containers. It uses the Tor proxy and an .onion domain to anonymously connect to its command and control (C2) server.
Zero Trust
Lessons from Cisco’s Zero Trust Deployment
TL;DR: How Cisco was able to deploy a company-wide zero trust model in less than six months.
During the 2021 RSA Conference, Cisco’s chief security and trust officer Brad Arkin said that over a five-month period, Cisco managed to transition many of its own employees into a zero-trust setup.
Under the setup, passwords are no longer used; instead, each user and device is issued a digital certificate, along with an MFA request. Once that is verified, the certificate is checked each time the user tries to access a specific resource, such as a database or an internal application. Read the case study on Cisco’s own journey to zero trust with the help of Duo.
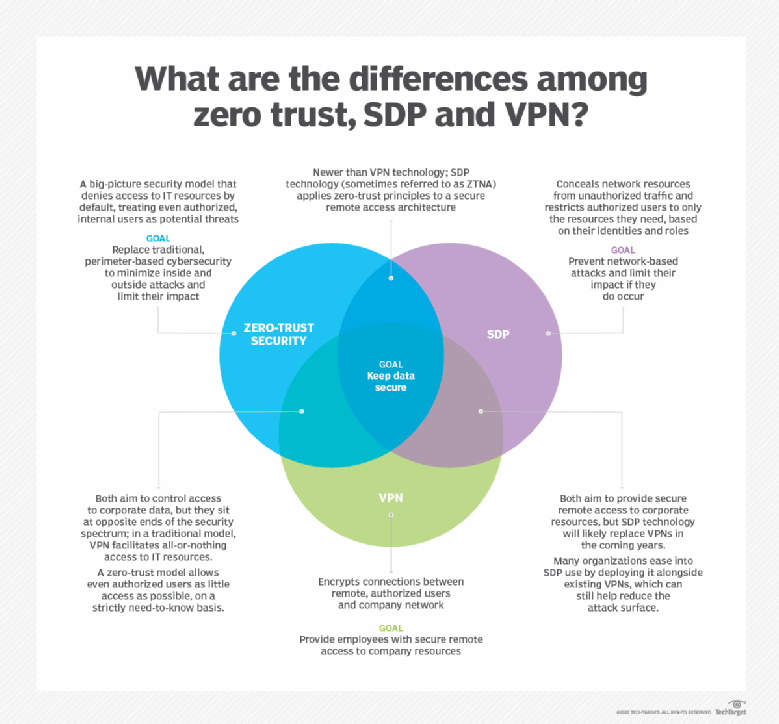
Zero Trust vs. SDP vs. VPNs
These three approaches might seem to oppose one another, but they can work in concert for a more comprehensive security strategy.
Organizations can pair SDP, which can use zero-trust concepts — such as no implicit trust — and VPNs to delineate a clear network perimeter and then to create secure zones within the network with microsegmentation.
- What is Zero Trust? Ultimate Guide to the Network Security Model
- VPNs and Zero Trust: Thoughts on the Evolving Nature of Remote Access
Extra Read: A Useful Mental Model for Zero Trust
Phil Venables draws a parallel of military tank alignment to segmentation of technologies with an example of zero trust architectures.

More on this..
Offensive Security
Bruteforcing SSH with Metasploit
TL;DR: How to target “low-hanging fruits” on a network and automate vulnerability discovery and exploitation with Metasploit.
When performing a penetration test within an organization, one common technique that pentesters employ is to target the low-hanging fruits on the network. The low-hanging fruits are easy-to-hack things, such as common services running on target systems. Since the IT teams usually configure remote access for management on systems and devices on their network, there will be common remote access protocols and services that can be found on critical systems.
One such common remote access service is Secure Shell (SSH). SSH allows a user to securely access a system across an unsecured network using a terminal emulator application. SSH is useful because it encrypts the data between devices and user either a username and password combination or a public and private key pairs for authentication.
So let’s get started with brute-forcing SSH on a target system using Metasploit! We will be using Kali Linux 2021.1 as the attacker system and Metasploitable 2 as our target (victim) system. Use the following steps:
Bruteforcing SSH with Metasploit
- Open the Terminal within Kali Linux and use the msfconsole command to start the Metasploit framework.

As shown in the snippet above, Metasploit will load a random banner and provide details about the number of modules per category available. These modules are categorized into auxiliary, exploits, payloads, post-exploitation, encoders, no operations (NoOps), and evasion modules. - With Metasploit, we don’t need to open a new Terminal to perform Nmap scanning, we can do it right within the Metasploit command-line interface. Next, use Nmap to perform a port scan on the target to determine whether port 22 is open for SSH:
- It’s now time to search for a suitable module within Metasploit that will allow us to perform brute force actions against the target system. Use the search ssh login command to quickly perform a search of the suitable SSH modules as shown below. Notice how Metasploit returned a few modules which are related to our keywords:
- Next, use the auxiliary/scanner/ssh/ssh_login module as shown below:
This module not only checks whether a system allows SSH connections but also enables a penetration tester to perform both credential stuffing and password spraying techniques to determine which user credentials will be accepted on the target system. We also used the show options command to view what options are required to successfully launch this module. - Now, set the RHOSTS (target IP address), USER_File (list of common user names), and PASS_FILE (list of common passwords):
Once everything is set, use the run command to execute the module. The module will check each password with each username found within the wordlists and this can take some time.Now is the moment we’ve been waiting for! Check out how Metasploit was able to successfully find a username and password combination that works on the target as shown below:
Notice how Metasploit was also able to create a session (shell) between the attacker system (192.168.138.5:46043) and the target system (192.168.138.3:22). This means we have gained access to the target system. - Next, use the sessions command to view a list of all active sessions within Metasploit:
Note there is currently one session with an ID of 1. - Let’s use the sessions –i 1 command to create and access an interactive shell on the target system:
Note the response for the command whoami. However, if you’d want to get a more interactive shell, you can use the python –c ‘import pty; pty.spawn (“/bin/bash”)’ command in Python.
You just learned how to use Metasploit to bruteforce SSH against a target system! I hope you found this tutorial useful. Special thanks to bestselling security author Glen D. Singh for helping collaborate on this tutorial.
[Disclaimer: You shouldn’t perform penetration testing or any type of intrusive actions on systems which you do not own or have legal permission to do so.]
More on Bruteforcing SSH with Metasploit..
Attacks and Vulnerabilities
Cloud Security Scenarios: Table Top Exercises
An amazing collection of attacks and monitoring scenarios focused on AWS. The idea is that security teams meet often to create response procedures for the unknowns — situations when suspicious activity is detected or a compromise is known but that don’t have predefined SOPs for responding teams.
The table top exercises are designed to start a conversation. Not all will be applicable to every environment. A few that I enjoyed:
- Injected CloudFormation Templates
- Broken CloudTrail Logs
- Malware on a Public API
- Rapidly Escalating DDoS
Bottom line: Before rushing to implement specific tools or buy third-party products to address these scenarios, it is critical to implement a well-defined security strategy. Many of the scenarios could either be prevented, or quickly remediated, with proper adherence to controls, frequent training of security and engineering teams, and careful monitoring of cloud activity.
What is SSI Injection and How to Test?
Web servers usually give developers the ability to add small pieces of dynamic code inside static HTML pages, without having to deal with full-fledged server-side or client-side languages. This feature is provided by Server-Side Includes(SSI), which are directives that the webserver parses before serving the page to the user.
To test for exploitable SSI, inject SSI directives as user input. If SSI are enabled and user input validation has not been properly implemented, the server will execute the directive. This is very similar to a classical scripting language injection vulnerability in that it occurs when user input is not properly validated and sanitized.
Follow the steps on the OWASP blog here to identify SSI injection points and find out how to assess the severity of an injection.
Bottom line: SSI can lead to a Remote Command Execution (RCE). SSI injection vulnerabilities are often simpler to exploit, at the same time, quite powerful as they can output the content of files and execute system commands.
Resources and Tools
IaC Security Resources
iacsecurity/tool-compare
This repository helps compare the different options in infrastructure-as-code security so that users can choose the tool that best fits their own needs.
Confectionery
A library of rules for Conftest used to detect misconfigurations within Terraform configuration files.
kics
Find security vulnerabilities, compliance issues, and infrastructure misconfigurations early in the development cycle of your infrastructure-as-code.
Cloud Security Resources
PurpleCloud
Multi-use Hybrid + Identity Cyber Range implementing a small Active Directory Domain in Azure alongside Azure AD and Azure Domain Services.
Hacking the Cloud
Hacking the cloud is an encyclopedia of the attacks/tactics/techniques that offensive security professionals can use on their next cloud exploitation adventure. The goal is to share this knowledge with the security community to better defend cloud environments.
Observability Resources
opstrace
Opstrace deploys secure, horizontally-scalable open source observability in your own cloud account, combining open APIs with the simple user experience of a large service provider.
Building a Cloud Security Observability Strategy
Dave Shackleford describes how companies can architect a security observability strategy that improves visibility into cloud-native infrastructures. Download the complete paper here: How to Build a Security Observability Strategy in AWS (requires SANS community login).
Podcasts
Tune in to:
- Hands-on Security: ProxyLogon Vulnerability
- FireEye Podcast: Pandemic Impacts to the Cyber Threat Landscape
- Snyk Podcast: Open Source Security
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes.


