SecPro 19: Ransomware-as-a-Service, GitOps Tools for K8s
Hey there!
In today’s issue, I am joined by a special contributor Joe Anich, Senior CE, Cybersecurity Incident Response at Microsoft. Joe is co-authoring the upcoming Packt title Microsoft Security Operations Analyst Exam Prep Guide with author Trevor Stuart scheduled for publication in mid-2022. You might be able to sense a theme in today’s SecPro which is an explainer edition that deep dives into Ransomware-as-a-Service. In the process, we’ll also show how you can mitigate RaaS with Microsoft Defender 365. We aim to give a high-level view of how Ransomware-as-a-Service works, as well as many of the things you can implement to start protecting yourself and reducing the attack vectors in your environments. In the end, we demonstrate a quick simulation of a ransomware attack to help you get an idea of what it looks like and how Defender for Endpoint and Defender AV steps in.
Let’s get to it.
SecPro Explainer: Ransomware-as-a-Service
By Joe Anich
Over the last few decades, ransomware has evolved to a level where it’s seemingly the sole attack type that keeps security teams up at night, or at least CISO’s. Some would say the silver lining to the rise in ransomware has led to the C level listening to their teams, opening the checkbooks, and implementing what their perpetually understaffed teams have complained about for years.
For some companies, it’s led to hiring and developing a security team as a whole. I have worked with numerous companies in my career, small, big, and gargantuan, where this has been the case. The skill shortage is a real issue in security, or cybersecurity, whatever you like to refer to it as (that’s a sensitive conversation all on its own). If you find yourself scrolling Cyber Twitter, you’ll find yourself reading more arguments about what people call this or that, when they’re all talking about the same thing. Moving on…
One of the scariest things about ransomware nowadays is its remarkably efficient, to the point where we now have to consider it’s a full-blown Ransomware-as-a-Service or RaaS.
With it getting easier to rollout, the financial damage it’s creating is on the rise and it’s not focused on any one industry anymore. Private, public, nothing is off-limits. Another scary thing is that we’re starting to see public infrastructures being attacked more frequently, hospitals, power companies, public transportation, and water treatment facilities. The security researchers at Microsoft have reported a 130% increase in the number of companies that have had to deal with some level of ransomware in the last year alone. One of the more disturbing facts being that the ransoms have climbed into the millions, and that’s common!
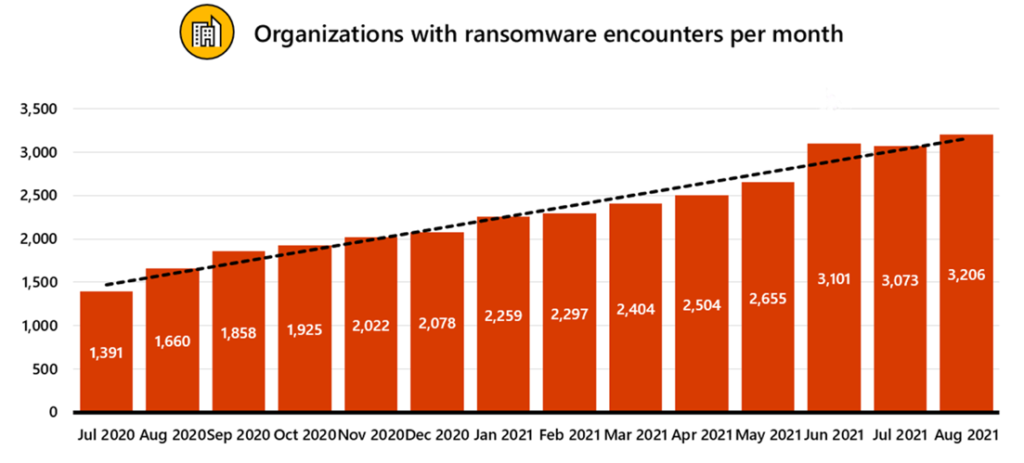
Graphic source – https://docs.microsoft.com/en-us/security/compass/human-operated-ransomware#additional-resources
The most gut-wrenching part of Ransomware-as-a-Service attacks is the damage it can cause beyond just the cost of either paying the ransom or paying to have it removed from the environment with the help from 3rd party incident response teams. When we look at public infrastructure outages, we’re having to now consider those damages, for instance, power grids. Whole towns or cities can be without power, proper water treatment, etc. Now start extrapolating out the repercussions of that, homes without power, grocery stores without power, the impact starts growing in a hurry. Looking at other industries that get impacted we see damages that extend to intellectual property being stolen, which can affect just about everything with a business’s growth or advantage against competitors. Lastly, something far more damaging and costly can be the loss of customer trust, especially when the ransomware attack includes a release of sensitive customer information.
What I’m looking to do for those who leverage the M365 Defender suite of tools, is helping bring to light the different things you can do to start reducing the attack surface for these types of attacks. We’ll cover a ransomware attack at a high level then discuss some mitigations you likely already have at your disposal with a Microsoft subscription.
What is Ransomware-as-a-Service (RaaS)?
So, what is Ransomware-as-a-Service? Well just like most “as a service” business models, you can probably assume how this one works. You sign up for the service, paying whatever monthly or yearly fee, and then get access to a host of ransomware bundles of various types depending on the type you’re looking to deploy. You can even get access to support, community forums, and other features of a subscription. The worst part about it is that you hardly need any technical skills, which makes this extremely dangerous. Two of the more popular groups out there now operating with this model would be BlackMatter (formerly DarkSide) and REvil. We’ll focus a little more on BlackMatter in this article as it’s been one of the more recently talked about, which I guess we could say that about a few groups, but I digress.
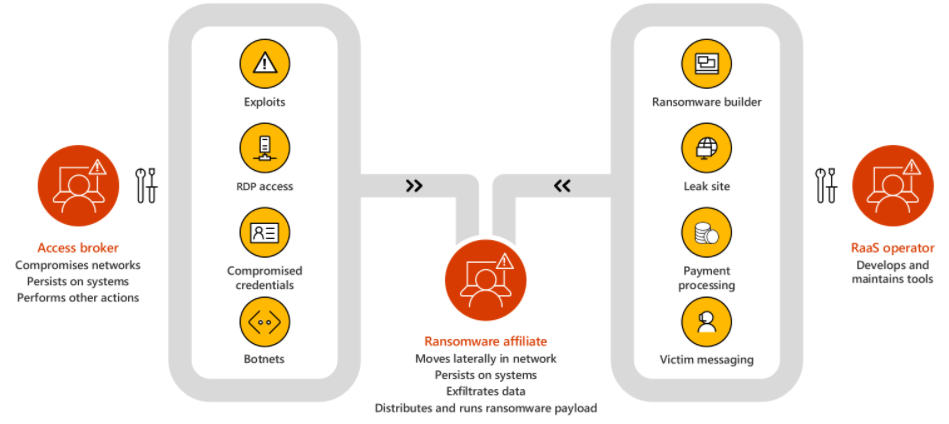
Ransomware-as-a-Service: BlackMatter
One such example of RaaS operators is the group called BlackMatter, formally called DarkSide before going offline for a while after their attack against a major US oil pipeline. If you care to read more about it there are numerous articles about it online. What was interesting about that attack as it seemed to be the first-time part of the group’s infrastructure was taken down. After that attack, the group lost access to several of their public-facing servers. One interesting thing that came to light when they came back online was that they specifically note on their site that they do not attack sectors like the Oil and Gas industry. This is ironic given the headlines they made, however, it’s something to note that they don’t have any control over what affiliates do with their ransomware.
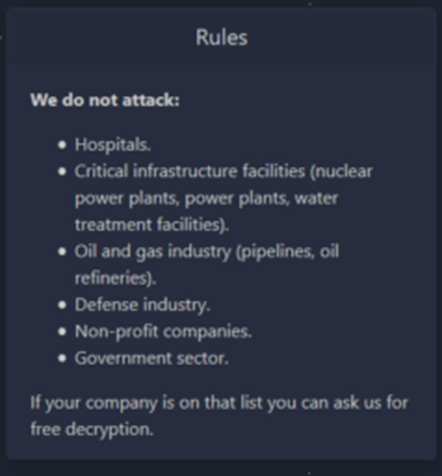
The BlackMatter group has made comments about not being affiliated with the previous DarkSide ransomware, but this has mostly seemed like just an effort to hide its re-brand, as its distribution model, operations and methodologies are all too familiar.
Let’s dig into their tactics and techniques at a high level for a moment so we can address them later when discussing the M365 Defender suite. Their two most common methods for entry into environments are phishing and existing access that can be purchased on the dark web.
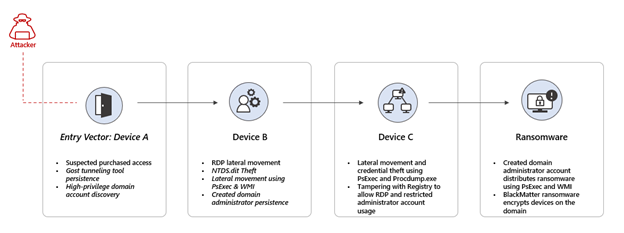
The below diagram is an example of purchased access, where the attacker used an account already compromised to log into a device over RDP. From there persistence is created, reconnaissance to gather information on high privileged accounts, and further lateral movement towards a domain controller where they dump the NTDS.DIT file after making a backup of the Active Directory database.
Next, the attacker created an account and added it to the local administrator’s group as well as domain admins, then proceeded to modify the registry entries for DisableRestrictedAdmin and DenyTSConnections. These two changes basically allow for logging into insecure devices that would otherwise not be allowed or blocked. From there, firewall rules were created to allow RDP connections.
Lastly, the attack used Device C for the distribution of ransomware across the domain over SMB, leveraging PSExec to execute remotely over WMI.
How to Mitigate Ransomware-as-a-Service with Microsoft Defender 365
Looking at attack techniques gives you an idea of what you need to be looking at in your environment to start reducing that attack surface. We’ll break this down into a few different areas such as:
- General security posture
- Device protection
- Identity protection
- Information protection
- Email protection
General Security Posture
One of the most underrated things you can implement is security baselining. I have seen 100’s of environments and a very low percentage of administrators use them, couldn’t tell you why. Security baselines is a set of tools that allow you to analyze and test Microsoft-recommended security configurations for Windows operating systems and other Microsoft products and how to harden them.
- Check out the following blog to learn more – Microsoft Security Baselines – Microsoft Tech Community
Another easy win would be applying Attack Surface Reduction rules. These help to block suspicious activity and content that can lead to attacks. See below for an extensive list of the rules you can implement. Also, be sure to check out this blog for the full descriptions – Attack surface reduction rules | Microsoft Docs
- Block all Office applications from creating child processes
- Block executable content from email client and webmail
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
- Block execution of potentially obfuscated scripts
- Block JavaScript or VBScript from launching downloaded executable content
- Block Office applications from creating executable content
- Block Office applications from injecting code into other processes
- Block Office communication application from creating child processes
- Block untrusted and unsigned processes that run from USB
- Block persistence through WMI event subscription (Persistence)
- Block credential stealing from the Windows local security authority subsystem (lsass.exe) (Privilege escalation)
- Block process creations originating from PSExec and WMI commands (Lateral movement)
Lastly, within the Microsoft ecosystem, you’ll come across Microsoft Secure Score. This is a great way to track the progress you make as you enhance your security posture. With it you get a more complete picture of your current security controls as it relates to things like Exchange, Azure Active Directory, Defender for Endpoint, Defender for Identity, Team, etc. Of course, not all of these applications may be applicable to you, but you get the point. Also, recommendations are coming for other security products that will hopefully provide a good baseline. Overall being able to get recommendations for what features to configure and the impact it will have is such a convenience, often times taking the homework out of it for your admins as it gives you the how, why, and supporting documentation.
Another great feature is being able to see your trends, and how you’ve improved over time so that the work you and your team are putting in shows, not to mention how you compare in the industry.
Device Protection
When looking at device protection in a Windows ecosystem, there are some no-brainers you should be enabling, but we see time and time again it goes unnoticed. Some basics to ensure you have set up in your environment are:
- If Defender AV is primary, turn on cloud protection to ensure you’re getting real-time protection. This is a part of Defender AV that works with Microsoft’s AI and ML backend to give you real-time intelligent protection on emerging threats. This does not include your AV definitions, those need to be updated as well. That can be managed a number of ways, see here – Manage Microsoft Defender Antivirus updates and apply baselines | Microsoft Docs.
- Tamper protection is a must, even if Defender AV is not primary but you’re using Defender for Endpoint (EDR). This ensures the default values and settings for Defender AV remain how they were configured and prevents them from being changed. This includes trying to make changes via the registry editor, PowerShell, or change group policy.
- Turn on Microsoft Defender SmartScreen, site and download checking, and set to Warn or Block. Turning this on prevents your employees from continuing to unsafe sits or downloading unsafe files that can be malicious.
- Turn on Microsoft Defender SmartScreen, app, and file checking. This helps warn employees that they’re downloading executable content that is not common.
- Disable unsigned macros.
- Set RDP security level to TLS.
Identity Protection
- If applicable, enable Sign-in risk policy and User risk policy in Azure Identity Protection. This can help remediate risky behavior on the fly by requiring the users to get flagged to verify a sign-in or prove their identity again. See more here – Risk policies – Azure Active Directory Identity Protection | Microsoft Docs.
- Enable and enforce on-premises Azure AD Password Protection for Active Directory Domain Services. This detects and blocks known bad passwords and variants of them so you can block people from changing them by a single letter or number. See more here – Azure AD Password Protection – Azure Active Directory | Microsoft Docs.
- Enable and enforce MFA.
- Leverage conditional access to validate users and computers.
- Practice good credential hygiene and remove the ability for highly privileged accounts to log on to workstations.
Information Protection
- Implement controlled folder access, this dictates what folders trusted apps can access. This helps greatly against ransomware.
- Backup files regularly. Use OneDrive for as much as possible for employees, as it can snapshot data for restoration if needed.
Email Protection
Enable the following in exchange online if they apply to you and your mail system. These should be stapled items as they can help prevent some of the most common attack vectors, the employees.
- Anti-malware protection – Anti-malware protection – Office 365 | Microsoft Docs
- Anti-spam protection – Anti-spam protection – Office 365 | Microsoft Docs
- Anti-phishing protection – Anti-phishing protection – Office 365 | Microsoft Docs
- Anti-spoofing protection – Anti-spoofing protection – Office 365 | Microsoft Docs
- Safe Attachments in Defender for Office 365 – Safe Attachments – Office 365 | Microsoft Docs
- Safe Links in Defender for Office 365 – Safe Links overview for Microsoft Defender for Office 365 – Office 365 | Microsoft Docs
The more attractive the phishing campaign, the more likely you’ll get them clicking and potentially compromising themselves. These tools also give you the ability to do your own campaigns that helps train your employees. You can learn more about that here – Attack Simulator in the Security & Compliance Center – Office 365 | Microsoft Docs.
Detection and Response – Real Threat Simulations!
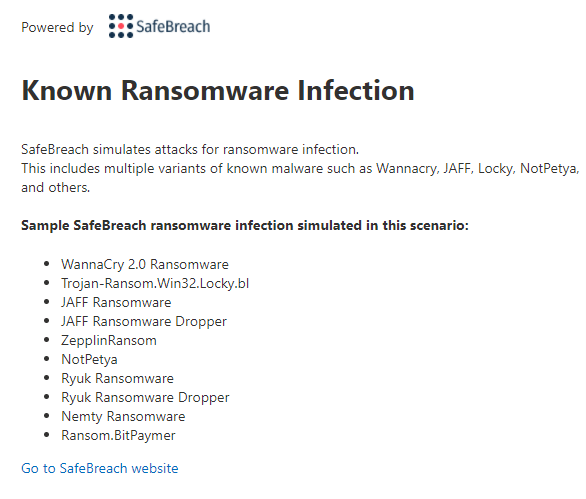
Let’s do a quick simulation of a ransomware attack to get an idea of what it looks like and how Defender for Endpoint and Defender AV steps in. We’re going to start with a built-in “Known Ransomware infection” simulation. This tests a whole suite of ransomware detections as you can see from the list below.
Once we kick off the simulation, we’ll move over to the portal to see some alerts came in and they’re all on one machine. Let’s go look!
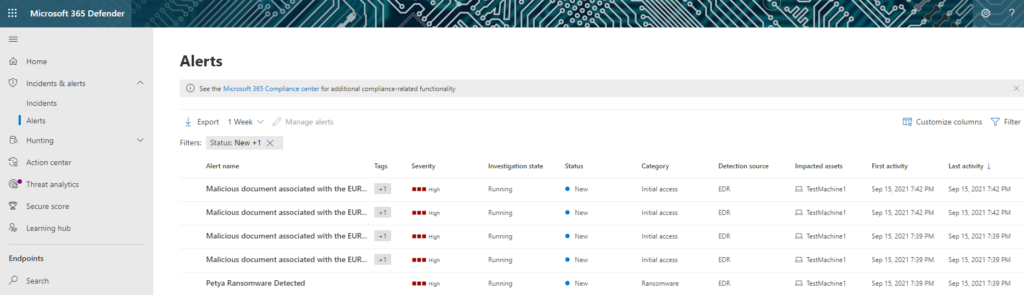
Wow, so we see several alerts for one device, let’s see if they’re related. From here will go to incidents to find that it’s a multi-stage incident. From looking at the Investigation state, I can already see my automated remediation is already in action and working to remove the threats. Let’s look at the Petya Ransomware detection investigation quickly. Check out the Doc to learn more about automated remediation – Use automated investigations to investigate and remediate threats | Microsoft Docs.
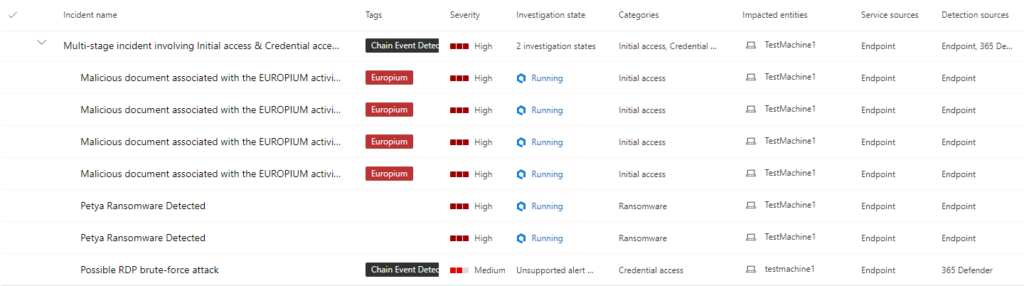
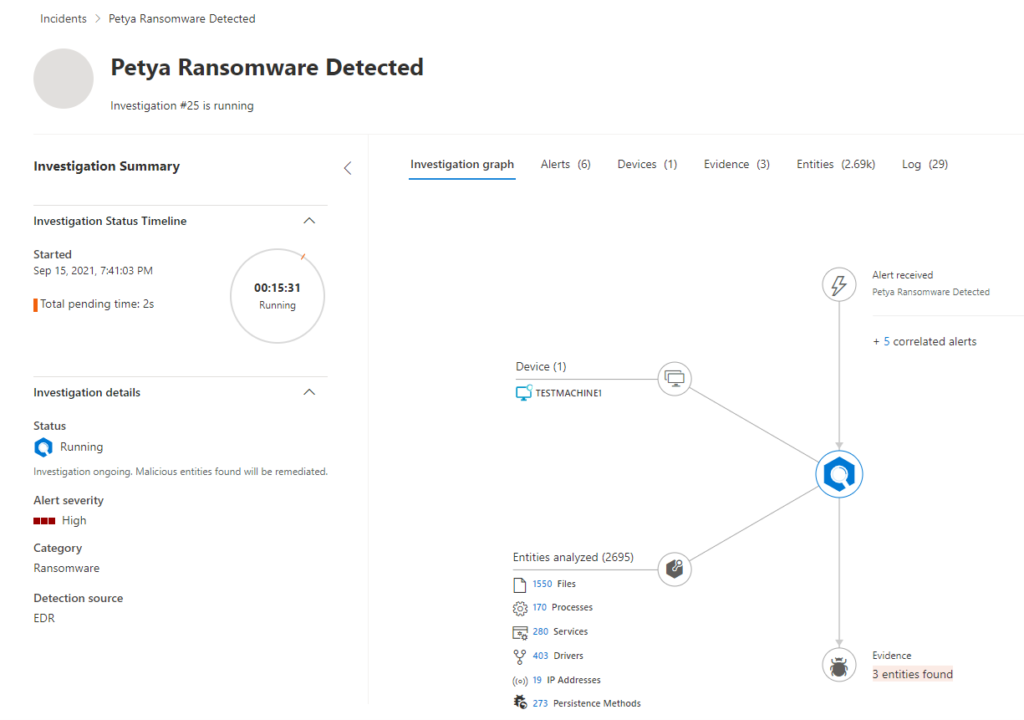
As we can see from the investigation graph, I’m able to see everything Defender for Endpoint has scanned as well as the evidence it’s found that it deemed as malicious. This is a great page to get the full picture of what’s currently in the works.
From the endpoint perspective, we see the Windows security center lighting up with alerts as they are detected and remediated.
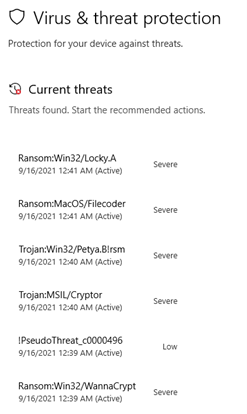
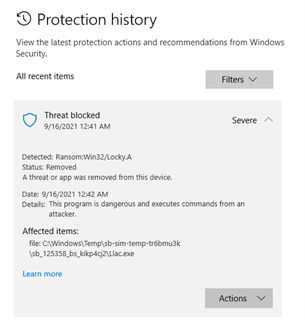
After just a few short moments, we see they’ve all been removed from the device and back to a safe state.
You can also see the protection history:
Wrap Up
With this, I’m hoping you understand at a high level how Ransomware-as-a-Service works, as well as many of the things you can implement to start protecting yourself and reducing the attack vectors in your environments. It’s hard for anyone to say you can prevent these things in their entirety, but you can surely make it difficult and at a minimum help with containment and recovery should it happen. There’s nothing worse when both happen, the attack and you being unable to reasonably recover. Losing time and money can wipe a business out.
Often times during IR engagements, customers realize the entry point was something easily avoided with something that could have been rolled out with very little impact, but we’re not here to shame anyone, we’re here to learn together and help protect ourselves. I know for a lot of large environments it’s hard to figure out where to start, but with the help of things like Secure Score, you can start to get a picture of what you have going on. With the tools that come with Windows security baselines, you can start hardening your operating systems with guidance.
In closing, take it seriously, because it can happen at a moment’s notice. Take the stance that there will be bumps along the way and there will be moans and groans as you flip on new protections to start shoring up your environment but stick with it. The more you can relay the changes being made and the impact they will have, the more support you’re going to have at all levels.
Recent Security Issues
- Does your organization have a Security.txt file? Some companies have adopted a proposed Internet standard that provides researchers with information about vulnerability disclosure. A Security.txt file will usually list links to vulnerability disclosure policies and a contact email address. Some also include bug bounty program information and public encryption keys.
- TikTok, GitHub, Facebook join open-source bug bounty to uncover dangerous code repository bugs that end up going viral across the application supply chain. Following a spate of spectacular software supply-chain breaches, market leaders have decided to throw in some cash to fund the IBB to incentivize bug hunters to take a closer look at open-source code.
- Researchers have begun compiling a list of vulnerabilities commonly exploited by different strains of ransomware to gain initial access to systems. The vulnerabilities are broken down by vendors and enumerated by their CVE IDs. The list comes in the form of a diagram providing defenders with a starting point for shielding their network infrastructure from incoming ransomware attacks.
- Time to update all your devices! Recent updates from Apple, Google, and Microsoft include patches for vulnerabilities that are being actively exploited. Among the vulnerabilities Apple has fixed is a chain of exploits known as ForcedEntry, which has been used to install spyware without user interaction. Microsoft’s updates include a fix for the MSHTML rendering engine that can be exploited to execute arbitrary code. And Google’s update for Chrome includes fixes for two vulnerabilities that are being actively exploited.
Secret Knowledge
Discover useful security resources, cheatsheets, hacks, one-liners, and open-source CLI/web tools.
Blue Team & Red Team
- SteveD3/kit_hunter: A basic phishing kit scanner that will search directories and locate phishing kits based on established markers.
- magoo/ato-checklist: A checklist of practices for organizations dealing with account takeover (ATO).
- Pentesting Bible – Hacking, penetration testing, red team, and cyber security resources.
- Red-Teaming-Toolkit – A collection of open source and commercial tools that aid in red team operations.
Mobile Security
- ImmuniWeb® Mobile App Scanner – test security and privacy of mobile apps (iOS & Android).
- Quixxi – free Mobile App Vulnerability Scanner for Android & iOS.
- Ostorlab – analyzes mobile applications to identify vulnerabilities and potential weaknesses.
- apkeep – new APK Downloader from EFF Threat Lab.
Other Resources
Top 10 API Testing Tools – According to Gartner, by 2022, vulnerabilities involving APIs will become the most frequently attacked vector across all cybersecurity categories. This article features some of the top commercial API testing tools on the market followed by some open-source tools.
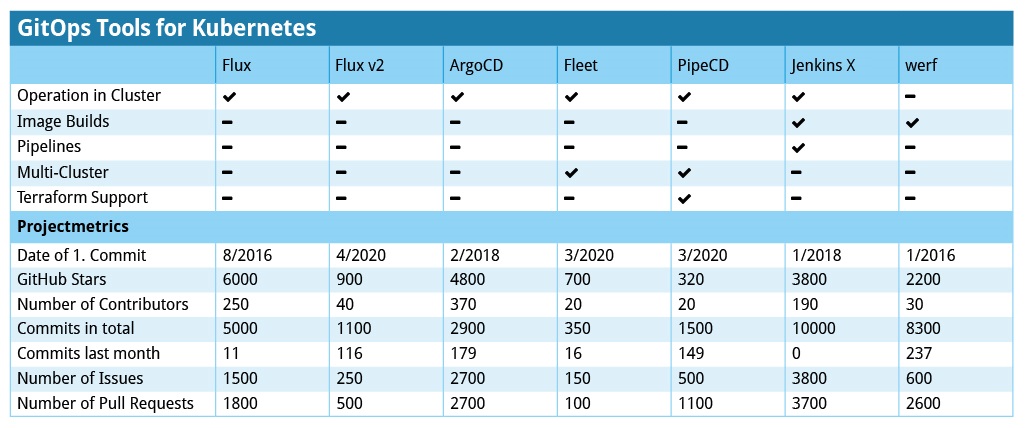
GitOps Tools for Kubernetes – It is no wonder that there is a growing number of GitOps tools to choose from. But what range of features do they offer? Is a single one sufficient, and can it automate “everything”? This article by Cloudogu answers these questions on the basis of specific examples and compares a number of GitOps tools for Kubernetes, secrets management, and more.