Do you really know what your IoT devices are up to?
Written By: Austin Miller
While the world has become more and more unpredictable, I’ve continued to enjoy the steady stream of SharkFest seminars that unearth new and interesting ways to use Wireshark in an enterprise setting. This week, I’ve been catching up on How Smart Are My “Things”?, a talk given by Simone Mainardi, PhD who investigated the traffic that goes through IoT devices when they are idle.
As more companies are turning to IoT devices to fulfill their production needs, cybersecurity professionals need to have a full understanding of what exactly these devices are doing. If you are adding an IoT device or network to your organization’s repertoire, you should be running similar tests to show exactly what leaves your network, when, and how you can manage that potential security risk.
Why should I run these tests?
Everyone knows that IoT devices raise a lot of questions that still need to be answered. Despite this, the growing adoption of these devices is directly pushing these security issues into the workplace. For cybersecurity professionals, it is now a duty to “vet” all IoT devices in a way that shows that they are secure (or that they aren’t)!
Dr. Mainardi gives two reasons for suspicion of IoT devices:
- These devices are directly connected to the network and can be used as a jumping off point for infiltrating business and personal systems.
- IoT devices are generally cheaply made with little attention paid to security in their manufacture.
Taken together, this creates a potentially dangerous situation for data infiltration and other adversary actions through the IoT weak link in the chain.
The aims of this experiment
By monitoring network behavior over a period of time, you can gather important information concerning the safety of using certain IoT devices. To know that, however, we need something to measure.
- Which hosts are contacted?
- Which protocols are used?
- Are the protocols secure/encrypted?
- How are Over-the-Air (OTA) firmware updates handled?
When we can answer these questions, we can begin to understand if idle actually means idle. Although this article will not deal with each of these questions, you can find out Simone Mainardi’s findings here.
The experiment
Dr. Mainardi experimented with the following IoT devices:
- Two EzVIZ C6C (ez360) cameras, neither of which is set to record or upload
- Two TP-Link HS100 Smart Plugs
- Two Sonoff S26 Smart Plugs
- Sonoff DW2 Door Sensor
- Xiaomi Mi LED Desk Lamp 1S Smart Lamp
Obviously, a production environment will have different kinds of IoT devices, but a basic experiment can give us an insight into the types of information that leave the network through these weak links. From that point, you can build up an experiment to test your own devices.
The equipment
You will need the following equipment to run a similar test:
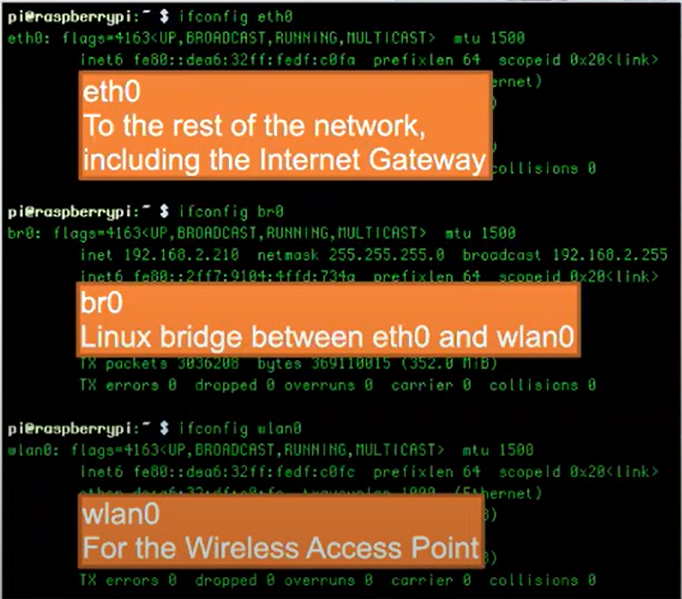
- A bridged wireless access point (AP) — Mainardi used a Raspberry Pi version 4
- A Linux bridge installed on the AP
- Capinfos, a Wireshark CLI tool
What do we find?
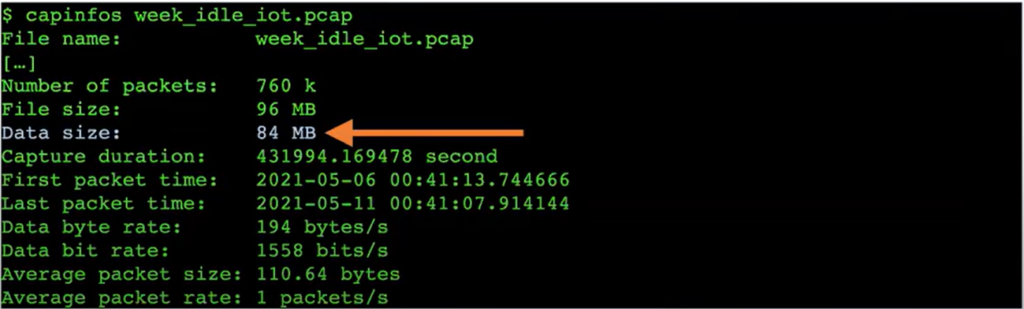
When I was watching the presentation for the first time, I was surprised to find out that the overall amount of data leaving the supposedly inactive devices amounted to 84MB. On its own, that doesn’t seem a lot, but why is anything leaving the network at all?
Let’s look at which devices are chatting while they are idle.

As can be seen from the results, a large amount of information leaves the network through the Xiaomi Mi Lamp and the EzVIZ cameras. It should be reiterated that neither camera is set to record or upload any data throughout the experiment – this is just basic data transmission. Although there is very much a concern about Chinese devices and their data harvesting capabilities, it seems that American devices (such as those sold by EzVIZ) are also worth consideration.
Let’s dig a little deeper…
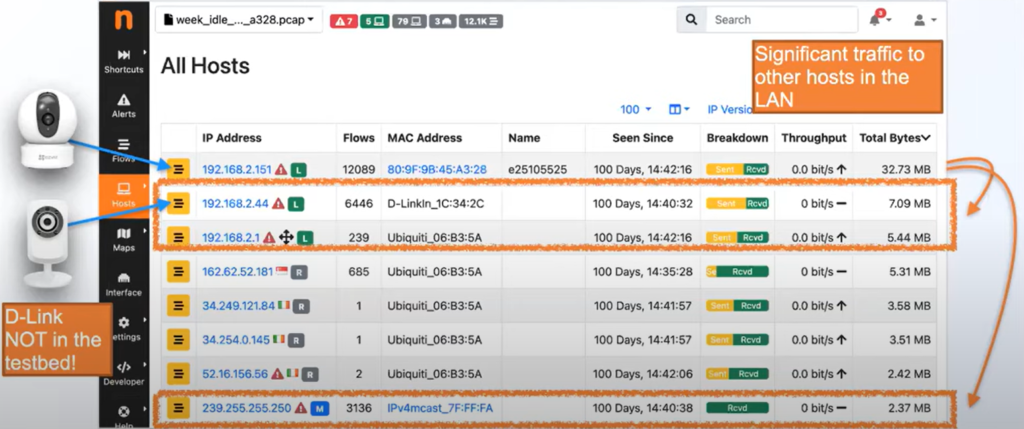
From this image, we can see that the EzVIZ cameras are openly communicating with other devices that were not in Dr. Mainardi’s testbed. When using Wireshark to analyze the packets being sent to the D-Link security camera, the EzVIZ uses SSDP to discover services on the LAN and then uses HTTP to fetch information about said service.
In a way, we are effectively inviting lateral movement into our networks!
Without proper security precautions, these EzVIZ cameras could become a hotbed of information for the adversary that is trying to investigate what is on the network and find exploitable hardware or software. Alternatively, an attacker may respond to the SSDP request and use fake services to connect to the EzVIZ camera with HTTP request.
Do you know your network well?
Although this is just one investigation into a small number of IoT devices, a serious issue has been unearthed. The adversary could easily circumvent the perimeter of the network by attacking these cybersecurity light devices, rendering the expensive and complex defenses that you have put in place worthless.
As always, IoT cybersecurity best practices comes down to a small number of easily implemented actions:
- Only use IoT devices that are necessary for the functioning of your network.
- Keep firmware up to date to ensure that security is maintained.
- Stop IoT devices from facing the internet wherever possible.
- Use industry-standard anti-virus/anti-malware, intrusion detection, and scanning solutions.


