As promised last week, here is a deep dive into polyglot and JAR file attacks that have been noticed around the world. If you’re concerned about your professional systems, check out the links in this roundup to shore up your defences against these strange attack types.
If you missed last week’s issue, we were discussing polyglot file attacks and the recent trend of JAR file attacks. These attack types rely on messages that use two or more programming languages to obfuscate malware. Due to the sheer variation in programming languages, these attack types become a never-ending game of whack-a-mole – we see one combination type appears as quickly as another is dealt with.
With that in mind, here are the four types of polyglot attack types – including two pseudo-ployglot attacks – that we have seen over the last year.
MSI obfuscation
First of all, here’s a sample:
5e288df18d5f3797079c4962a447509fd4a60e9b76041d0b888bcf32f8197991
Opening it up to inspect the file, it appears that this is an MSI file (that is, a tool for installing Microsoft software). But the problem for the unwitting and impulsive file installer is that there is also a JAR in this file – one that links straight out to Ratty.
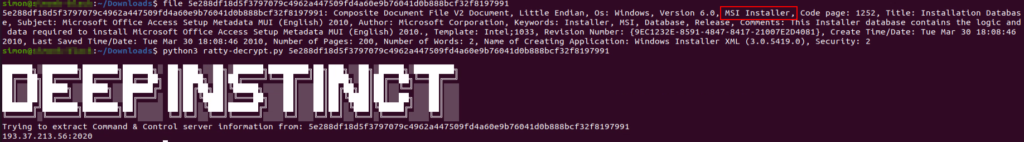
If successfully launched, the file links the victim computer up to the C2 server. After that point, it’s bad news to say the very least.
The attack type for these attacks seems to have been over Sendgrid, through link shortening technology, and as samples hosted over Discord.
CAB obfuscation
This time, two samples:
Ratty: f620c4f59db31c7f63e8fde3016a33b3bfb3934c17874dcfae52ca01e23f14de
StrRAT: 2f4c6eb0a307657fb46f4a8f6850842d75c1535a0ed807cd3da6b6678102e571
This time, CAB files have been used to hide these polyglot and JAR files. Why are CAB files perfect for this? Because CAB files have a “unique magic header” and Windows interprets them from beginning to finish. This means that they are perfect for sticking junk code in.
Linking out to the same C2 server (donutz[.]ddns[.]net), this is definitive proof that there seems to be one group behind both attack types. As they have shown four attack types overall, we can presume that this isn’t the end of their ingenuity.
HEX Trash/Fake PE
Here’s one of my favourite attack types – sticking junk content in HEX files. According to the report by Deep Instinct, they’re not entirely sure if this was done intentionally or accidentally, however. If you have experience using malware analysis tools, you can access this file through this sample:
19154b831614211de667c2aedd6a4b5b89d4bfc1e129eb402a6300ad2e156dcf
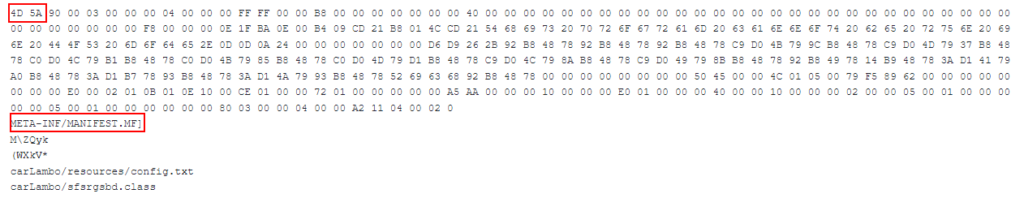
As you can see from the highlighted values above, there is an executable attached to this HEX. This is the perfect way for a threat actor to sneak an attack in undetected because many security systems are incapable of dealing with this kind of “junk content in HEX” attack and it’s practically impossible to recognize manually.
As a small aside, the Deep Instinct team noted that these files aren’t technically polyglot files. They’re just junk text thrown in at the end of a legitimate file type; this gives us some evidence that these attacks weren’t intentional, and they were sent out as an oversight by the team behind this.
Binary junk files
And here’s our final attack type. Firstly, have a sample:
8d801f58d10dbcd52739fa35aa862286c3fe9606411f0e5f7b8b3fd71f678cad
Again, this isn’t a proper polyglot file attack. This is (as the subtitle suggests) some junk that is found in the binary. Have a look below:
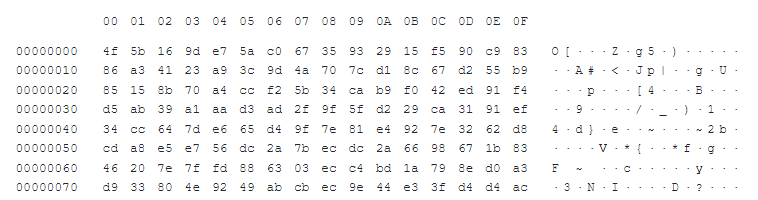
As another attack type that is completely impenetrable to the untrained eye, there is another amusing possibility here:
- These threat actors have a highly developed understanding of what they are doing and are sneaking these files into victim systems with real ingenuity and skill, or
- These threat actors have no idea what they’re doing and they’ve been sending out accidental links to their C2 server unbeknownst to them!
I’ll let you decide which one it is. Regardless of the dilemma above, the JAR file that is shared over the malicious link attack. If you end up on the wrong end of one of these, it’s not going to be a good day.
What can I do?
Great question. Sadly, there’s no real answer at this moment. Because the threat actors have evidently (either through skill or through coincidence) struck a methodology which allows them extreme flexibility. The best defense is always proactive, so keeping up to date with VirusTotal and looking for industry advice around these RATs as it becomes available.


