SIM SWAPPING – What you should Know & Why you should care
SIM SWAPPING – just what the scam is, and just how this fraud can cause massive financial impact for victims is the focus of this article. With the rise of online fraud, the general public are increasingly becoming more vigilant and aware of scams using social engineering & phishing as attacks vectors. Equally Ransomware attacks are often reported in the media and these attacks are widely known.
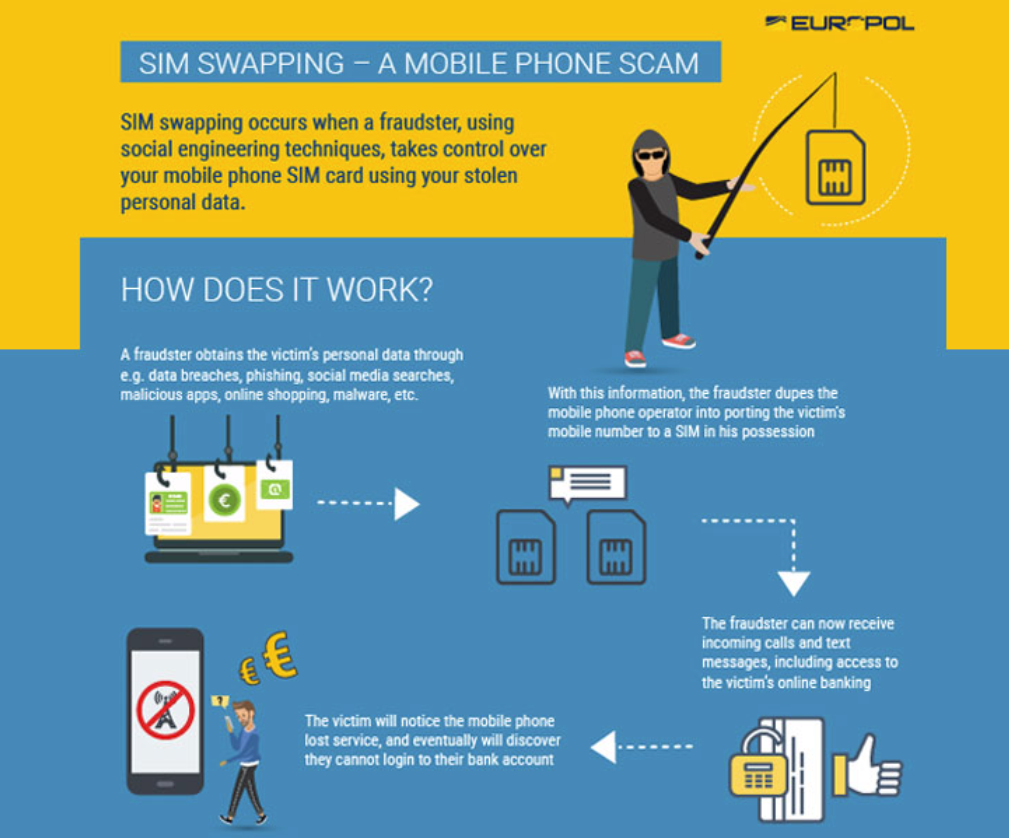
What is little known though but having the potential to one of the most damaging of all online fraud scams is SIM SWAPPING. Known by many different terms including SIMJACKING, SIM Splitting or port-out scam can lead to severe consequences for those that fall victim to the scam. The scam itself takes advantage of a weakness in 2FA combined with the use of a One-Time password. SIM SWAPPING allows fraudsters to take over your mobile phone number which exposes a weakness in 2FA. Enabling Multi Factor authentication adds a layer of security which gives us a little more reassurance that our accounts, be that financial or other cannot be accessed by fraudsters.
Usually, 2FA comes in the form of an SMS message sent to our mobile device using our registered mobile phone number. Unfortunately, if we apply a little logic, we come to understand that if a scammer can get access to our number then we have effectively lost any form of security that we thought we had and we then become totally compromised.
Is SIM swapping difficult?
Apparently not difficult at all if the attacker is determined enough. As Twitter CEO Jack Dorsey was to discover on 6th September 2019 when a number associated with his account was compromised. In this incident the attackers used the account to post messages of hate and not for financial gain. If the victim of SIM SWAPPING were the target of financial fraud then by taking control of the targets mobile phone number any SMS message sent to the number would be received by the scammers thus allowing access to the victim’s accounts.
This is simply done by requesting a password reset which is then sent using a one-time password recovery code sent via SMS. With ownership of the compromised mobile number the fraudster is able to control over the victim’s entire finances or digital accounts. Take the case of Michael Terpin, a US based Cryptocurrency investor who was the victim of a $24 million SIM swap fraud in 2018. Terpin went on to sue AT&T for $200m claiming that the Telecommunications giant was partly responsible for his loss. Although this was dismissed in 2020 the court ruled that he was able to follow this up under two other claims.
The two cases, although high profile illustrate the financial, and the reputational damage that can be inflicted upon victims by fraudsters. Usually, the crime is targeted with scammers finding it easy to gather the necessary personal information required to convince a service provider of a person’s identity. With so many social media platforms being used, it’s not really hard to learn the details that are usually asked for to confirm identity, place of birth, favourite holiday destination, mother’s maiden name.
All of which are some of the standard questions to validate an identity and not difficult to obtain with some social engineering or phishing attacks. In some instances, it is claimed that the service provider’s employees have taken bribes to sell customer details. Take the example of a system admin working for the Russian based search engine Yandex. The admin was caught selling access to almost 5000 email inbox accounts in early 2021.
There is a widely held view that ‘trading’ of accounts by a number of Telecommunications providers is more common than thought. Although, I am not suggesting in any way that this is done in reality, merely that this is a thought process often found online. Whilst SIM swapping may seem a remote risk, and you may consider this to be an unlikely occurrence it is worth considering that in January 2018 through to December 2018 the FBI received just 320 SIM swap complaints. Contrast that to a year later and the FBI were to receive reports of 1,611 SIM swap attacks.
Here’s how it works;
- Scammer uses a number of techniques including Open-Source Intelligence, phishing or buying stolen credentials to learn the victim mobile number service provider
- Provider is contacted by the Scammer to request phone number ‘port’ to a new SIM by claiming any number of reasons; new number because of crazy ex, lost or new phone
- Number is ‘ported’ to a SIM that the scammers provided in step 2
- Once the number is ‘ported’ over the scammer will receive 2FA authentication requests, SMS message
How to protect against SIM swap scams
There are ways in which you can try to protect yourself from SIM SWAP attacks
Be Careful with your online behaviour: Beware of phishing emails Do not click on links in email messages from people you don’t know or verify links from those that you do. Remember that your bank, Credit card Company, or other service providers won’t ask for your personal or financial information through an email message.
Ensure that you use strong passwords for authentication
IDs: Do not rely on your security and identity authentication solely around your phone number. This includes text messaging (SMS), which is not encrypted.
Authentication apps: You should always make use of these rather than resetting of passwords by SMS
For the latest information or advise review your Services Providers FAQs or contact them directly.


