Engineering Trust – Cybersecurity Mesh
Written By Austin Miller
This one should be pretty clearly useful to security professionals – the cybersecurity mesh. Mesh technologies aren’t new, but the COVID pandemic and the increase in distributed workplaces meant that cybersecurity professionals had to go back to the drawing board. How do we protect the organization perimeter when it is so poorly defined?
The cybersecurity mesh is an innovative way to approach defense by shifting to an identity-focused approach to spotting the adversary. Thanks to ambitious plans to share these structures across organizations and a need for greater inter-corporation cooperation, some are even estimating that the cybersecurity mesh could reduce the impact of cyberattacks by up to 90%.
Understanding the cybersecurity mesh
As with data fabric, we’re not talking about a purely technological advancement here. For people wanting an easy advancement to the “next generation of cyber defense”, I’m sorry but it’s not going to be as easy as installing a new piece of software. A cybersecurity mesh is an architectural approach to computer security that relies on the following traits:
- A zero-trust architecture,
- Complex webs of secure connectivity between applications,
- The extension of all cybersecurity services to remote workers.
Of course, these things don’t happen overnight. As technology develops, the people using the technology have to be ready to adopt it. But what is absolutely necessary for developing a cybersecurity mesh that protects your organization?
How do you implement that type of technology?
Although “cybersecurity mesh” might be a new term to some, a lot of the words around the technology are known to many in the industry. In particular, there are three key parts which allow an organization to build a cybermesh:
- 5G technology
- Secure Access Services Edge (SASE)
- Extended detection and response (XDR)
5G
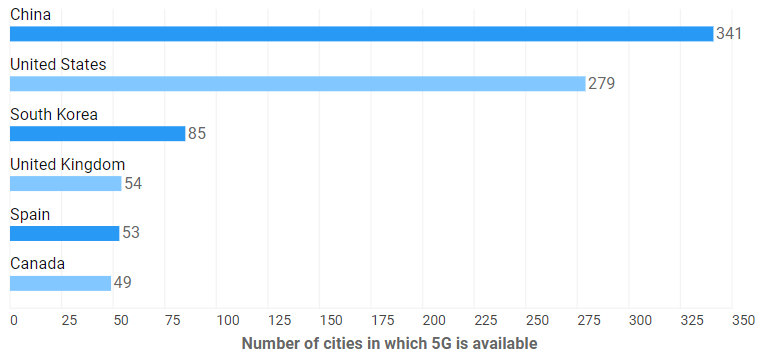
As the next stage of cellular technology, 5G offers a number of advantages to the average cybersecurity worker which help move to the next security paradigm. Because the technology offers high capacity data transfer with greater security, availability, and reliability, enterprise organizations will have to make use of the next stage of cellular technology.
Unlike 4G, 5G was designed not only with people scrolling Instagram on their phones in mind – as businesses needs demand better performance from both regular endpoints and Internet of Things (IoT) devices, the developers of 5G answered the call. The question now is whether countries with access to 5G can capitalize on this opportunity.
SASE
Created in 2019, digitalization, work-from-anywhere (WFA), and cloud-based computing are the three pillars of moving to a software-defined and cloud-delivered way of working. The overarching goal is to create an opportunity for enterprise employees to log in anywhere and still have all the secured assurance as if you were in an on-premises environment.
As more and more IT professionals work in WFA positions, this becomes a necessary part of the cybersecurity structure. Really, this is the cornerstone of the cybersecurity mesh approach – without effective, secure cloud-based computing, it cannot exist. There is no opportunity to build a mesh, no opportunity to create a web of security services, and no opportunity to build 5G capabilities and XDR security products into your network.
XDR
If you have been following our Community Wisdom series, you will have noticed a distinct uptick in the people interested in this type of technology!
As Advanced Persistent Threat (APT)/nation-state attacks and other cybercriminals become more sophisticated in their approach to cybercrime, the legacy tools – the ones that many organizations are still using – are growing inadequate to deal with the existing threats. The adversarial use of AI to automatically identify and attack weakened areas of a network needs to be answered with an AI-empowered tool that stops them in their tracks.
Extended detection and response (sometimes referred to as cross-layed detection and response; XDR) is the answer to that problem. Multiple data sources must be consulted to deliver intelligent, effective cybersecurity actions across a cloud platform.
How can I use a cybersecurity mesh?
As you can see, taking the plunge to become a cybersecurity mesh organization is a large undertaking. As more and more areas are opening up to 5G and cloud-based computing opportunities present themselves to organizations, the conditions for an expansive mesh solution are developing.
The benefits – if they are not already clear – will be massive. Gartner predicts that up to 90% of all common cybersecurity issues could be stopped if organizations started to work together against cybercriminals and used their SASE and XDR capabilities to create a kind of “Popular Front” against the ever-advancing threat of the adversary. Could such a thing exist in reality? Well, the realpolitik of business and international politics means that goal probably far off. But as an aspirational goal for the people who are on the frontline against cyberthreats? It’s something that is very interesting indeed.








