Fuzzing faster with FFUF
Content discovery or fuzzing is an important aspect of black-box testing or bug bounty. The more endpoints we discover, the more content we discover the more is the attack surface. What exactly fuzzing you might ask. Fuzzing is an automatic process of giving random input to an application to look for any change in its behavior or to see if it gives any errors. Finding hidden files and directories also falls in the category of fuzzing.
Here in this article, I would like to introduce you to a tool that does fuzzing at a lightning speed. The tool is called FFUF (Fuzz Faster U Fool). Before using FFUF, I mostly used dirbuster but now I have fully shifted to FFUF and I’m sure after reading this article you too will do the same.
FFUF is an open-source web fuzzing tool made to discover elements and content within web applications. Why is this important? Often when we visit a website, we only see the things which the owner of the site wants us to see. We often miss out on juicy things which can be of great help to us as a penetration tester. For example, imagine getting a /backup directory that contains the backup of all the files of the website. FFUF can be used for uncovering these juicy things in speed.
Installation
Installing FFUF is very easy and simple. If you have a recent go compiler installed then do the following: go install github.com/ffuf/ffuf@latest or
git clone https://github.com/ffuf/ffuf ; cd ffuf ; go get ; go build
If you are using Kali Linux you will find FFUF in the apt repositories which allows you to install it by running sudo apt-get install ffuf
After installing, you can verify the version by this command: ffuf -V
Usage
The main function that people use the tool is for directory brute-forcing. But before brute force, we will need to give FFUF a wordlist. A wordlist is a list of items in a text file that are tailored around a purpose.
There are many word lists to choose from but I often use Seclists as they have a huge collection of wordlists for different purposes. As anyone can contribute to these lists, they are frequently updated.
Seclists wordlist can be found here: https://github.com/danielmiessler/SecLists/
Seclists have many wordlists but for directory listing, we can use these wordlists :
- https://github.com/danielmiessler/SecLists/blob/master/Discovery/Web-Content/directory-list-2.3-small.txt
- https://github.com/danielmiessler/SecLists/blob/master/Discovery/Web-Content/directory-list-2.3-medium.txt
- https://github.com/danielmiessler/SecLists/blob/master/Discovery/Web-Content/directory-list-2.3-big.txt
Once you have selected the wordlist save it in your local drive. Let’s call it list.txt
FFUF have two basic arguments which we need to fill in.
1. -u : Here we need to enter the target URL
2. -w : Here we need to enter the path of the wordlist
We also need to enter the word FUZZ where we want our wordlist items to be placed. For example, if we want to brute force example.com here is how the command will be :
ffuf -u https://example.com/FUZZ -w /home/list.txt
Using this basic command, the tool will find files and directories which match the response status 200, 204, 301, 302, 307, 401, 403, 405, 500.

Sometimes we might need files with only a specific response status. For example 301 response status. In this case, we can run the following command :
ffuf -u https://example.com/FUZZ -w /home/list.txt -mc 301
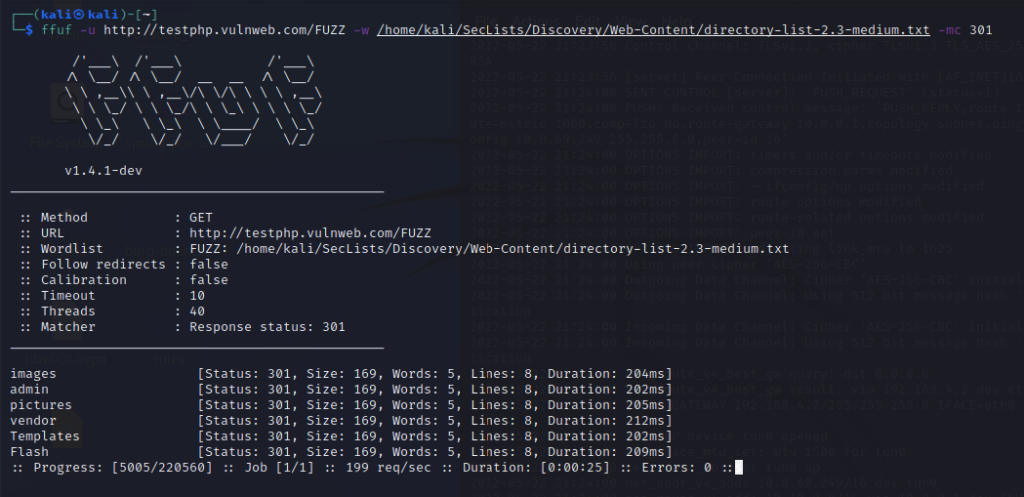
FFUF is highly customizable. We can customize it to search for specific files based on size, extension, and a lot more filters. Explaining all the features of this awesome tool will not be possible in this article. I would like to ask you to have a look at the tool and explore its features.
Conclusion
FFUF is a great tool for fuzzing and content discovery. What makes it stand out from other similar tools is its speed and flexibility. It can be used with other tools easily. FFUF is a must-have tool on your list.
There are a lot of other tools which can do the same thing. What sets FFUF apart is its speed and flexibility. FFUF is a command-line-driven tool. It provides a high level of flexibility as we can pipe into and out of FFUF with other command-line tools and this makes it very powerful.