News Bytes
All systems down in Costa Rica
A massive attack has completely disrupted Costa Rica this week, including medical services which have been forced to turn to paper management. This has not come out of anywhere either – in May, a national emergency was declared by the Costa Rican government (which at the time people were already referring to as a belated response) and things have only gone from bad to worse for the Central American nation.
With suspected Conti attacks targeting industry and government infrastructure a month ago, the nation’s cybersecurity was in a dangerous position. Now that a new attack has been launched against the public health services, the social security funds, and other key elements of the national infrastructure.
As previously mentioned, the Conti ransomware gang has played a part in the attack, but there seems to have also been a secondary attack using the Hive ransomware. This multi-pronged attack has ground over 30 institutions to a halt and is expected to already have caused over $15 million worth of damage to the economy. Right now, the weakness of Costa Rica’s defensive posture (bearing in mind that they already had to pay out $10 million in April to a separate adversary) paints an ugly picture of the weakness of some Global South nations and the growing gap between the adversary and those who are being left behind the technological boom.
At some point, people working in the cybersecurity organizations of the Global North have to ask themselves, “is it right to charge so much that the people who need these services can no longer afford them?”
Forescout shows the newest way ransomware will get you
For the conspiracy theorists of the world, you no longer have to worry about your IoT devices always watching you. Instead, you need to worry about them demanding that you pay $10 million or you’ll be facing some pretty dire consequences.
Security researchers Forescout have created the “Ransomware for IoT” (known a bit more snappily as R4IoT) that has shown that ransomware which exploits an IoT device before moving laterally is possible. While many of us may have assumed this was always on the horizon, seeing the proof-of-concept should certainly put the impetus on some security teams to look into how secure all their network devices are.
If you followed the WireShark Sharkfest series, you will have seen this analysis of IoT devices from popular technology companies and how they are operating even when we think they’re not. If there truly is no idle mode for these devices, what should we believe about the real risk of ransomware becoming an easy to vector for adversary to exploit? Hopefully, we’ll see more IoT companies taking their security responsibilities a bit more seriously now.
International global takedown works!
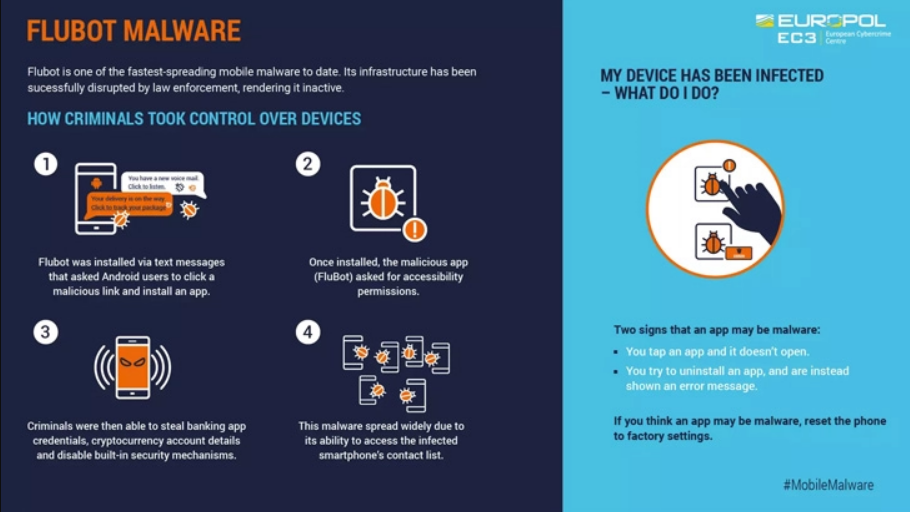
If you’ve been worrying about FluBot – a mobile malware – or have been working to protect your organization’s phones against the threat, we’ve got some good news for you. An international law enforcement operation of 11 different nations has convened to take down the threat of the malware and give us the peace of mind.
Europol said “[t]his Android malware has been spreading aggressively through SMS, stealing passwords, online banking details and other sensitive information from infected smartphones across the world”. American, Australian, Belgian, Dutch, Finnish, Hungarian, Irish, Romanian, Spainish, Swedish, and Swiss forces united to take down the virus which mainly operated through smishing to steal banking details and steal money from unwitting victims.
Here is an infographic from Europol that explains how the malware was taken offline:
The Department of Justice seizes data theft and DDoS domains
In a recent announcement from the US Department of Justice, three domains used to get DDoS attacks-as-a-service or buy and sell personal information have been taken down. For the threat intelligence specialists reading this, you may recognize these names: weleakinfo[.]to, ipstress[.]in, and ovh-booter[.]com.
Although three domains are only the very tip of the iceberg, it’s clear that there is a concerted effort to keep pushing back against the adversary. In a week which also saw global agencies convene to take down the FluBot malware, it’s clear that the defensive side of the cyberwar is still fighting back against the numerous hidden lairs of the adversary.
If you want to find out more about the weleakinfo websites, see the links below:
As for ipstress and ovh-booter, these services offer DDoS services at a for-hire price. Although ransomware-as-a-service (RaaS) operators are well known to many in the industry, the growing number of other malware types which are being exploited by the adversary should be on the radar of everyone involved.








