BloodHound: Mapping Active Directory Relationships
Written By: Andy Pantelli
Modern Networks are becoming ever more increasingly complex. The workplace has evolved and not just due to the global Pandemic. Users are now expecting to connect any device, from any location, to access any resource. The cloud has obvious benefits with SaaS applications facilitating this transition from the legacy working model and static infrastructure.
This shift in practices and architecture also brings with it increased security concerns with an ever-changing landscape and growing attack vector. Increasing overhead & management can often leave gaps where adversaries will look to find, and then to exploit. The role of a Security Professional is becoming increasingly more difficult as malicious actors develop new tactics and procedures. Active Directory has many known exploits and attack vectors, such as the Kerberoasting attack we wrote about in a recent article.
Today we’re looking at a tool that can be used by security professionals to assist them in mapping and visualise the Active Directory paths within the organisation.
What is Bloodhound?
BloodHound is a tool that is used by both blue and red teams and is a Web application written in JavaScript. It uses a front-end of electron with a back end Neo4j database. The power of this app is in its use of a graph database that can quickly discover relationships whilst calculating the path between links. BloodHound uses graph theory to discover hidden relationships, and with the capability of discovering unintended paths inside an Active Directory environment.
The app collects data using an ingester called SharpHound which can be used in either command line, or PowerShell script. SharpHound is the data collector which is written in C# and makes use of native Windows APIs functions along with LDAP namespaces to collect data from Domain Controllers and Domain joined Windows systems. It will collect information about AD, the users, computers and groups, even having the capability of collecting active sessions & AD permissions whilst being run from a standard user account. BloodHound can be installed on Windows, Linux or even macOs.
Adversaries can use BloodHound to quickly map complex paths that may otherwise be extremely difficult, if not impossible, to identify. Conversely, defenders can use BloodHound to identify and eliminate the attack path. Whilst primarily seen as an Offensive Security tool it should equally be considered to be a tool that can assist Security Professionals in their work. With that being said complementing this is PlumbHound which is a Proof of Concept purposely for Blue & Purple teams to be more effective by producing operation reports. Providing these in a graphical representation specifically aligned for Defensive Security Operational teams. For the use of internal scanning BloodHound offers Security Teams an insight into what attackers may achieve or even what an insider threat actor may accomplish.
To use BloodHound the following prerequisites are needed and can be found at the following GitHub repo at https://github.com/BloodHoundAD/BloodHound:
1. Install neo4j
2. Install BloodHound & Web UI
3. Data Collection Using SharpHound
As we’ve previously stated BloodHound can be installed on a variety of Operating Systems with each fully documented on the official site;
1. Windows: https://bloodhound.readthedocs.io/en/latest/installation/windows.html
2. macOs: https://bloodhound.readthedocs.io/en/latest/installation/osx.html
3. Linux: https://bloodhound.readthedocs.io/en/latest/installation/linux.html
Reported by some users, and as is the case within my test environment the Linux install process is far from smooth which has prompted users to go with a Windows install.
Once the prereqs are complete (neo4j, Bloodhound & SharpHound) the next step is to run the neo4j database using the sudo neo4j start command for Linux or for Windows C:\neo4j.bat install service then start the service with net start neo4j
Bloodhound Installation
If you want, follow along and run BloodHound in a lab environment then a sample database is available using the hosted Databases:
- DBurl: bolt://206.189.85.93:7687
- DBusername: neo4j
- DBpassword: BloodHound
The “Database URL” is the IP address and port where your neo4j database is running, and should be formatted as bolt://ip:7687/
Open up a web browser and navigate to https://localhost:7474/. You will see the neo4j web console.
Authenticate to neo4j in the web console with username neo4j, password neo4j. You will be prompted to change this password.
Run BloodHound – if using Linux with the following command, or if using Windows using the application that you have downloaded and installed in previous steps
./BloodHound.bin –no-sandbox
BloodHound GUI
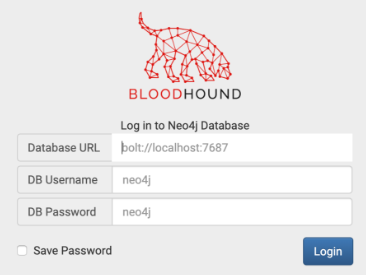
Login using the credentials you set up for the neo4j database
Now we’re ready to add some data, with the default installation the database will be empty. This is done with SharpHound and using the Windows install as a reference run the following PowerShell command C:\> runas /netonly /user:domainname\username powershell then import
the module by using Import-Module .\SharpHound.ps1 and Invoke-BloodHound –CollectionMethod all –Domain domainname.local
Collection of data is by using the C:\SharpHound[.]exe command or SharpHound can be run from a non-Domain joined machine using C:\> runas /netonly /user:example\username cmd[.]exe command
From here BloodHound has an impressive array of features and functionality, if you’ve followed along and connected to the hosted Database this will give you a great insight into the tool. If not the official documentation provides sample screenshots available here at the url below
https://bloodhound.readthedocs.io/en/latest/data-analysis/bloodhound-gui.html
Summing up BloodHound this is a hugely powerful, feature reach tool for Security Professionals to examine, learn & understand the paths that an adversary may use against their Active Directory Domain. With the additional PlumbHound visualisations this makes a great addition to Blue or Purple Teams
ACKNOWLEDGEMENTS
Any software, documentation or GitHub resources are acknowledged to be owned by the respective content provider.








