Crypto Mixing – Laundering Cryptocurrency
Let’s take a look at crypto mixing, what it is and how it helping criminals conduct their illegal activities, be that buying or selling stolen property or goods, services, stolen data or facilitating the infrastructure to extort victims of ransomware.
Cryptocurrency has changed the landscape for cyber-criminals who have taken full advantage of the opportunity – it’s the gift that literally keeps giving! But blockchain technology can also provide a means for researchers and law enforcement to get information pertaining to illegal transactions.
Cyber Criminals have responded by making use of cryptomixers to obscure & complicate investigations. In simple terms, this enables Criminals to make it difficult or even almost impossible to trace the origin of their illegally gained proceeds. Just another step in the perpetual game of ‘cat & mouse’ between law enforcement, security professionals and the community against criminals and threat adversaries in the ‘virtual world’ of cyber space.
Crypto Mixing How it works
Crypto mixers are available to the general public using stand-alone services using the internet. Also known as Tumblers the service literally mixes streams of different identifiable cryptocurrency to help provide anonymity to transactions. Using these anonymous means for communication, and not keeping any logs of customer transactions, makes this a perfect tool for the Cyber Criminal to use. Whilst law enforcement agencies are making the push for crypto exchanges to incorporate financial compliance laws into their operations, we see how crypto mixers are an attractive option for criminals or criminal gangs.
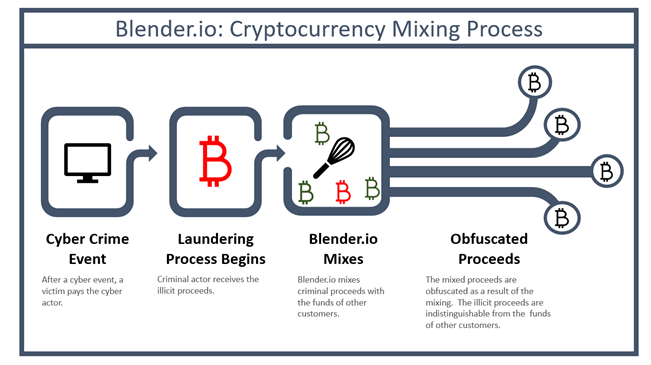
Drilling into the detail, criminals will send a sum of cryptocurrency – let’s say bitcoin to a Wallet address that the Crypto Mixer Service operator own. The sum joins a pool of the operators own bitcoins, or the service operator can mix the funds with that of other users. This ensures the connection between the original transaction and the address sending the funds is lost. Then cryptocurrency is put through a mixing process using a proprietary algorithm. The service owner provides a unique reference number also known as a mixing code which is then sent to the cybercriminal.
This is to ensure that the criminal does not receive the same set of bitcoin from the Service pool and ensure anonymity. The Service Owner can then send the cyber-criminal ‘clean’ funds from the pool after deducting the transaction fee. Transactions sent back can be broken down into several payments over a period of time to further obfuscate. For this, the Service owner will charge a fee usually around 0.25 – 3% of the amount to be mixed.
While crypto mixers in themselves are not illegal, the US Treasury has recently sanctioned Blender.io which it states “to support malicious cyber activities and money laundering of stolen virtual currency”. Blender was added to the SDN list of Specially Designated Nationals and Blocked Persons. In particular, the Treasury alleged that Blender was used to process over $20m of the illegal proceeds generated by the Lazarus Group which is said to be a Democratic People’s Republic of Korea (DPRK) cyber hacking group.
The US Treasury notes that whilst most virtual currency is licit, it can also be used for illicit activity including the evasion of sanctions through mixers, peer-to-peer exchanges & darknet market places.
MIXING PROCESS STEPS
A cyber criminal transfers bitcoin to the wallet address of a mixer service (e.g. Wallet ID 4Bf45PXY).
2. The criminal funds are received and pooled with the service to Wallet ID 3Ff35Pbu.
3. The mixer service uses a proprietary algorithm to mix with funds with the Service Owners Pool
4. The mixer service owner then sends ‘cleaned’ funds onto multiple Wallet ID owned by the cyber criminal (6TG35Pbn 7Ff65Pku 2Fhg95Lbb).
FIG 1 – Crypto Currency Mixing Process
POPULAR CRYPTO MIXERS
Some of the more popular mixers observed by the open source intelligence community who do not advertise their roles in money laundering. Rather that stating the obvious the Mixers prefer to suggest that their site Services are there to assist businesses using Cryptocurrencies or individuals that have privacy concerns.
- Absolutio
- AudiA6
- Blender (Sanctioned by the US Treasury on 06/05/2022)
- Mix-btc
This list, whilst in no way exhaustive were openly found on the clear internet, and also on the TOR Network. Interestingly, a number had Russian language version of their sites. Whilst this does not reflect the current situation in which Russian is involved in acts of aggression towards Ukraine, it does however correlate to the cyber intelligence open source communities widely held view that Russia facilitates many of the activities on the dark web, but is also seen as a ‘state sponsor’ or such crimes.
Whilst some RaaS groups seeking to keep a low profile as possible we have seen them incorporate crypto mixing services into their platform rather than relying on web based services to do the mixing. Groups including Avaddon, DarkSide 2.0 and the infamous REvil are thought to have integrated the BitMix cryptocurrency mixer to facilitate the laundering of Ransomware payments.
Crypto mixers are a crucial part of ransomware schemes. Using the mixers services, malicious actors can achieve their objectives of extorting money from the victim. It crucial that as security professionals we understand the operational workings of mixers which allows the money laundering from the proceeds of crimes.
ACKNOWLEDGEMENTS – any content linked or referenced is acknowledged to be the intellectual property of the respective author
- FIG 1 image link home.treasury.gov/system/files/136/Blender.io-flowchart.png








