Patch Tuesdays can be a nightmare for cybersecurity professionals and system administrators alike. But the _secpro team is on hand to lend some advice, showing you exactly what has been fixed this past week. A total of 79 issues were patched, but only a solitary zero-day has been found this time! That’s some progress over the last few months.
For our rundown this month, we’ll do a deep dive into CVE-2023-28252 as well as some shorter remarks on other vulnerabilities. Plenty to keep you busy while the systems update!
CVE-2023-28252
Here’s the big one – this month’s single zero-day vulnerability. In predictable style, there are already conflicting reports about whether this vulnerability has been exploited or not. But we’ll get to that in a minute.
Ranking at 7.8 on the CVSS, this vulnerability doesn’t seem to have been quite as dangerous as some that we’ve seen in the past. But the name should give us some clues about how the adversary could exploit this: Windows Common Log File System Driver Elevation of Privilege Vulnerability. A now-patched vulnerability in a CLFS driver leads to elevated privileges, which isn’t a good situation to be in. Let’s look at the scoring metrics that Microsoft have posted online:
| Metric | Value |
| Attack vector | Local |
| Attack complexity | Low |
| Privileges required | Low |
| User Interaction | None |
| Scope | Unchanged |
| Confidentiality | High |
| Integrity | High |
| Availability | High |
| Exploit Code Maturity | Functional |
| Remediation Leve | Official Fix |
| Report Confidence | Confirmed |
While some of these values aren’t too scary, the Confidentiality, Integrity, and Availability values are a real cause for concern:
- Complete loss of confidentiality
- Complete loss of integrity
- Complete denial of access
With that in mind, the CVSS 7.8 score might not be ringing alarm bells in our mind when it really should.
Understanding CVE-2023-28252
As previously stated, this is a privilege-elevation vulnerability. By manipulating a binary logging format (BLF) file, the adversary elevates privileges within a given system and can use that as a foot in the door to further attacks. This file will usually be delivered via a phishing attack or after using a known exploit – possibly obtained from an initial access broker (IAB).
Although Microsoft has officially stated that the vulnerability wasn’t exploited before patching, Kaspersky – the Russian antivirus and cybersecurity company – has stated that their Behavioral Detection Engine and Exploit Prevention components have found a known exploit in the wild.
What did Kaspersky find concerning CVE-2023-28252?
Kaspersky linked the vulnerability to the Nokoyawa ransomware. After having launched the malicious BLF file, they would then use Cobalt Strike Beacon and the modular backdoor Pipemagic to implant their ransomware and extort victims for payouts. Specific processes haven’t been released to the public due to fears of copycat attackers, but Kaspersky’s security team have uploaded the exploit to the SecureList website.
Thanks to considerable obfuscation (accounting for 80% of the code within the malicious file), the actual turnaround for remediation was fairly short. A full reverse-engineered creation was used to understand the problem and quickly report the findings back to Microsoft.
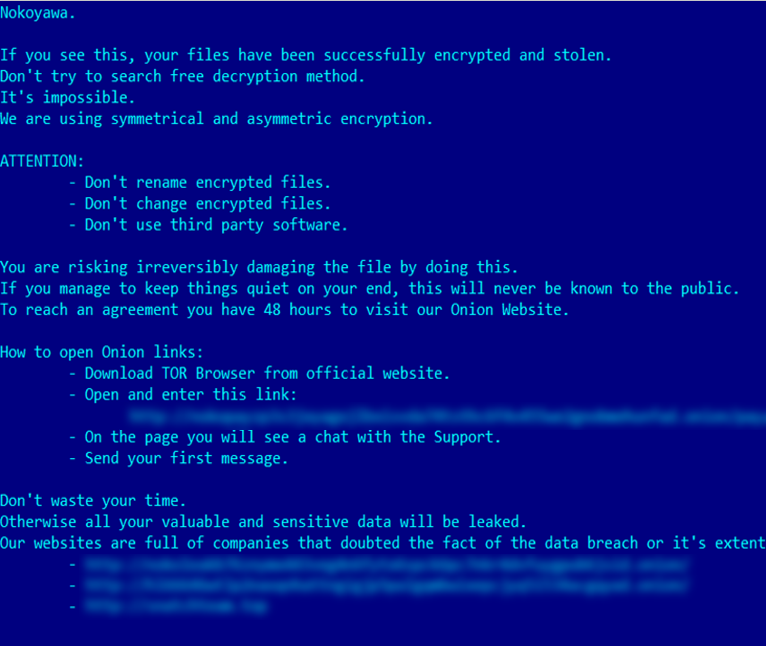
Is this the only example of CVE-2023-28252 in the wild?
It’s probably best to view this vulnerability as the latest example of a CLFS exploit that has stretched back to 2018. As Kaspersky noted, there has been multiple attacks by this particular threat group. By forcing an out-of-bounds write privilege (the most basic type of exploit that has been observed within the Nokoyawa ransomware family’s tactics), the gang launches its ransomware on the system. From that point, they are directed onto the Nokoyawa Onion page.
How do I protect myself against CVE-2023-28252 exploits?
As always, patch and update. Seeing as we are looking at the Windows April Patch Tuesday update, it makes sense that applying the patches as soon as possible should be the key takeaway. Although Microsoft’s security posture was a bit of a laughingstock back in the day (and we’re talking over a decade ago, at least), a properly configured and updated version of Microsoft is enough to fend off the majority of issues that most people will face.
For more general advice about avoiding the Nokoyawa ransomware, consult this short list:
- Keep all antivirus, antimalware, and all other applications up to date, including Windows itself
- Make staff awareness and training a key priority
- Implement phishing attack filters that stop inattentive and unwitting users from letting the adversary in
- Keep effective backups of all systems (and all key systems, if all infrastructure is not possible) off the main system – you don’t want to find out that your backups have also been locked down in the case of a breach!
To find out more, consult the Kaspersky SecureList report on the Nokoyawa exploit.







