noPac Vulnerability: A Microsoft AD Flaw
Late December 2021 Microsoft revealed two exploits when collectively combined by a malicious actor could lead to privilege escalation leading to a complete Domain compromise. The two, named CVE-2021-42278 & CVE-2021-42287 respectively came to be known as ‘noPac’. When chained together they come to form the ‘noPac’ attack. First disclosed by GitHub user Ridter and then later confirmed by multiple researchers, this is a low-effort exploit which has a critical impact: allowing a regular user the elevated privileges of a Domain Controller. Researchers have even demonstrated that the flaws exposed in Active Directory could be exploited in just 16 seconds with the adversary then able to perform Ransomware attacks, exfiltrate data, damage or even destroy assets and more. The vulnerability impacts any systems that have Microsoft Windows Active Directory installed.
The two vulnerabilities used to chain the attack make use of privilege escalation associated with the Kerberos Privilege Attribute Certificate within Active Directory Domain Services. The second is a Security Account Manager spoofing bypass vulnerability. Looking at what makes up the noPac attack a little closer let’s understand what the two CVEs are all about.
CVE-2021-42278
Disclosed publicly on 09th November 2021 by Microsoft this CVE results from invalid formatting of a computer name. If not enforced correctly as expected computer names will not end with the required character $ that the Active Directory Service would require. Part of the noPac chain an adversary may rename a user account to that of a Domain Controller account omitting the $ symbol at the end.
CVE-2021-42287
Also announced by Microsoft on the same day, 09th November 2021 this CVE is documented as being an elevation of privilege flaw within Active Directory Domain Services. This is given a CVSS score of 8.8 The vulnerability sits within the Kerberos Key Distribution Center (KDC) which is required to process Kerberos Ticket requests. By leveraging the Ticket-Granting Ticket, the flaw allows the access to other tickets as well as access token requests if the system cannot find. The KDC will default search for a best possible match name for the requested ticket ending in the $ symbol.
noPac Attack
Let’s now look at how it works together to exploit the vulnerabilities. Breaking this down into stages;
1. User Account Creation
2. Adversary clears the Service Principal Names
3. sAMAccountName is renamed to a Domain Account name excluding the $ symbol
4. Ticket-granting Ticket is requested
5. sAMAccountName is renamed
6. Service ticket is requested with a S4U2self extension
STEP 1
The initial stage of the attack is to create the new machine account. The default settings give the user SeMachineAccountPrivilege & MS-DS-Machine-Account-Quota permissions. The SeMachineAccountPrivilege is granted by default to Authenticated Users. The MAQ is set to a value of 10 which permits authenticated users the capability to add ten computer objects in the Active Directory Domain.
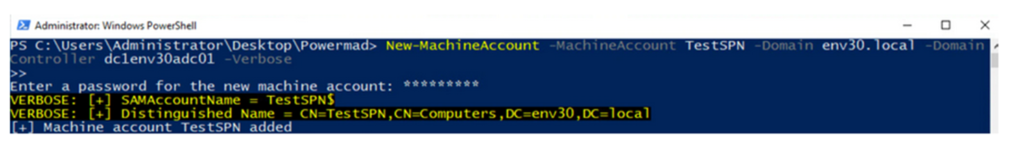
STEP 2
The SPN must now be cleared before the sAMAccountName is renamed. SPNs are linked to the name of the account and if the renaming is done before clearing then an error will occur.
STEP 3
Next the adversary renames the sAMAccountName attribute without the trailing $ symbol. As shown in the illustration the Domain Controller that is the target has the sAMAccountName DC1ENV30ADC01$ and is subsequently renamed without the $ to DC1ENV30ADC01. This behaviour is not validated and is documented in CVE-2021-42278 vulnerability.
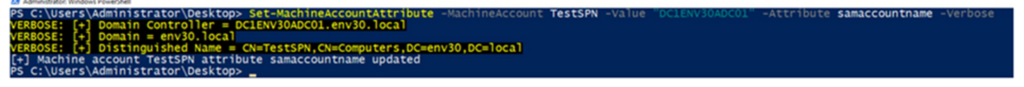
STEP 4
Next the adversary makes a request for a Kerberos TGT for the account ,
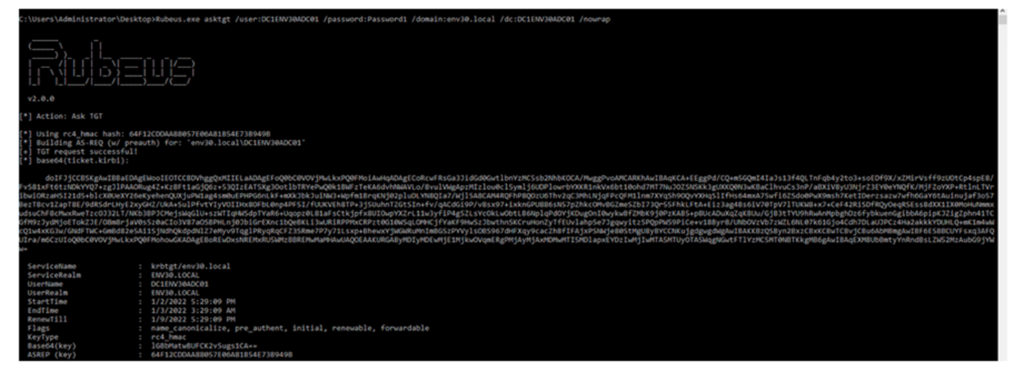
once this is done the adversary then resets the sAMAccountName back to the original value
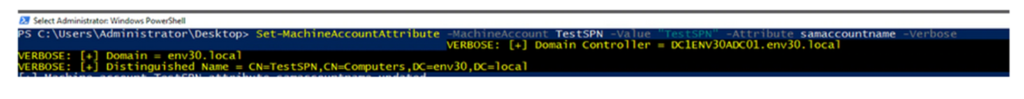
At this point in the attack CVE-2021-42287 comes into play. With the TGT previously granted, the adversary will then request a ticket for the service using the S4Uself extension. Due to the sAMAccountName DC1ENV30ADC01 no longer existing the KDC will look up with the trailing symbol $. The KDC now finds the Domain Controller account and encrypts the ticket with its key.
The attacker has successfully obtained a ticket for the Domain Controller account DC1ENV30ADC01$ as a standard user. From here doing a DCSync using this ticket it is possible to gain access to the Domain Controller.
TGS Request using Rubeus
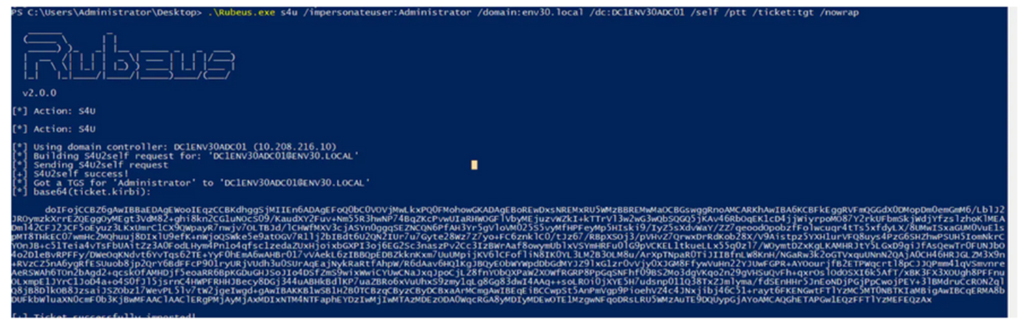
Various Proof of Concept exploits exist accomplishing this automating the attack. In order to mitigate the risk organisations should apply the latest patches to Domain Controllers following the Security Policies defined by the business. Patches include the November 09th releases for CVE-2021-42278 & CVE-2021-42287 and the 14th November ‘out-of-band’ update. Ensure that no Domain Controllers are omitted otherwise the entire Domain remains vulnerable.
Microsoft Response
“Make sure all of the domain controllers (DCs) are patched. If even one of them remains unpatched, it will mean the whole domain is still vulnerable — and practically patching a domain controller is not trivial given the critical operational nature it serves for IT infrastructure.
Perform a manual search for suspicious events and then use those events as a starting point for further manual investigation. Not only is the search manual, but it also requires manually specifying all of the domain controllers by name. Again, any manual mistake here might lead to missed hunting leads”.
REFERENCES & ACKNOWLEDMENTS
Powermad – https://github.com/Kevin-Robertson/Powermad
Rubeus – https://github.com/GhostPack/Rubeus
DISCLAIMER
Software or processes illustrated are acknowledged to be owned by the respective authors








