ReconFTW – A swiss Army Knife for Recon and Web Pentesting
In the last few articles, I shared about different Burp suite tools and how you can use each tool to your advantage. If you are into pentesting you will know how overwhelming it gets at times with so many different tools and methods to do our everyday tasks be it bug bounty or penetration testing for clients.
Web penetration testing needs different tools to make things fast and easy. Right from the reconnaissance phase to finding a flaw people use a lot of tools. I often use tools like FUFF, httpx, nuclei, assetfinder, Burp suite, etc a lot. Often I use to think can we have one single tool which can do all these tasks for us?
Today, let me introduce to you the Swiss army knife for recon and web penetration testing. Why do I call it a Swiss army knife? That’s because it can do a lot of tasks and can use a lot of tools automatically and give us results. The name of the tool is ReconFTW.
ReconFTW is a tool that automates the entire process of reconnaissance. Along with subdomain enumeration, it does vulnerability checks and obtains maximum information about the target. It installs a ton of popular tools for you and runs them one by one to get the maximum results. It saves time as you don’t need to run tools one by one and everything comes in one place.
Some of the techniques that ReconFTW uses are:
- Subdomain enumeration
- Bruteforce
- Source code scraping
- DNS record
- Web vulnerability scanning, etc
Mind map of ReconFTW
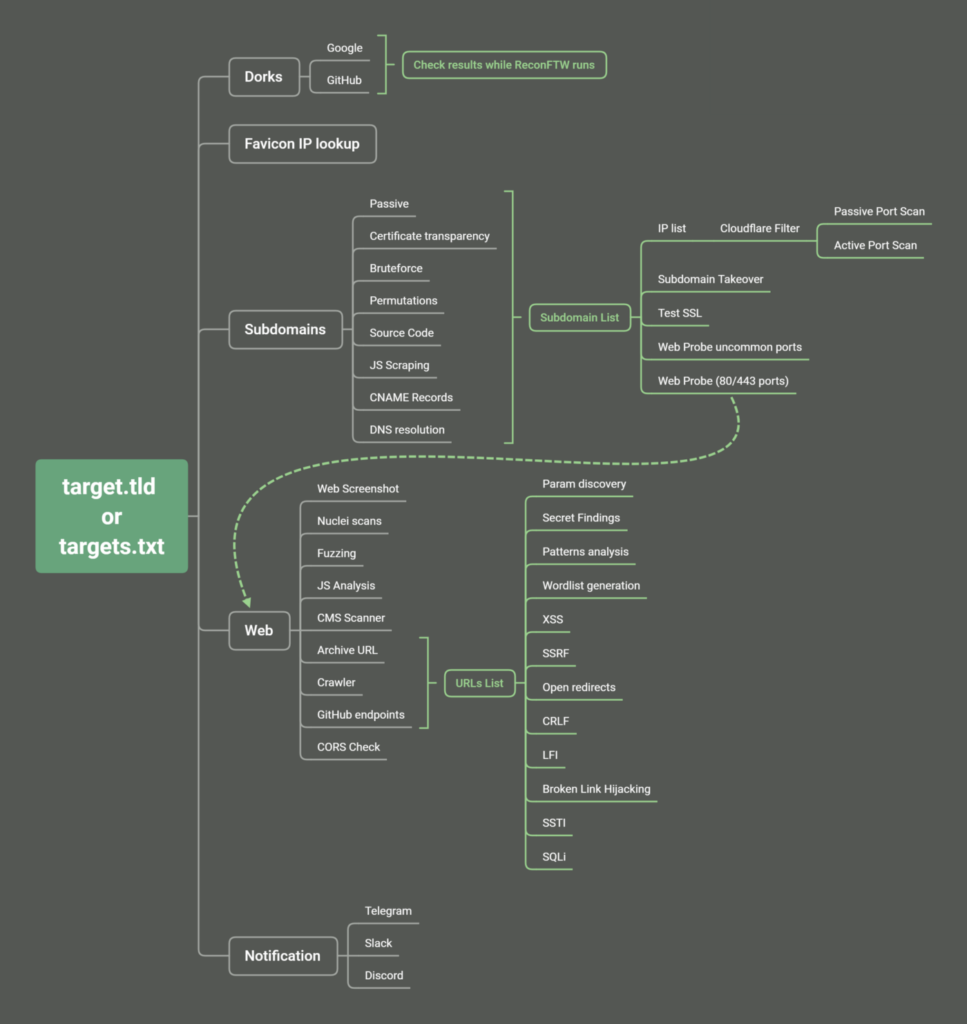
Here are some of the tools it uses for different phases of recon/web penetration testing:
- Subdomain enumeration:
In bug bounty, we have a saying that more attack surface means more bugs one can find. ReconFTW uses 5 techniques for generating a list of valid subdomains. It uses 5 top subdomain tools to find subdomains. The tools that it uses are : subfinder, assetfinder, amass, finddomain, crobat. Do note that we need to give API keys for some tools to run like Amass.
Sometimes subdomains are not indexed in search engines hence this tool uses shuffledns to brute force subdomains as well. ReconFTW uses JSFinder to scan JS files and source code for subdomains.
Apart from these tools it also uses a few other tools and techniques to find subdomains. Once the subdomains are found it uses the httpx tool to see which subdomains are valid and running.
- Web screenshots
Web screenshot comes in handy when there are a lot of subdomains to look through. ReconFTW uses webscreenshot tool to screenshot all the subdomains
- Subdomain takeover
A subdomain takeover attack is a type of attack in which an attacker successfully seizes control over the subdomain in a hijacked DNS. This often happens when organizations forget to remove the DNS entry hence attacker can take over the subdomain. ReconFTW uses a tool called subzy to perform automatic subdomain takeover detection. Subzy has a total of 21 fingerprints for service which are prone to subdomain takeover.
- Web probing
ReconFTW runs httpx to check if any web service is hosted in the subdomains in non-default ports. For this, it runs httpx on 80+ common web ports where web services might be hosted. These results increase the attack surface for the penetration tester.
- Nuclei Integration
In one of my recent article, I explained how powerful nuclei is. ReconFTW integrates nuclei into it to scan the domains for various vulnerabilities and saves the output in a folder called nuclei_output
- Github Dorking
Often developers create a public repo on Github and host source code in it. And sometimes these source codes leak sensitive information like API keys, hard-coded credentials, etc. ReconFTW uses the gitdorks_go tool to search for these secrets.
The tool can perform much more than what I mentioned above. You can download the tool from here: https://github.com/six2dez/reconftw
Here is to install ReconFTW
Requires Golang > 1.15.0+ installed and paths correctly set ($GOPATH, $GOROOT)
git clone https://github.com/six2dez/reconftw
cd reconftw/
./install.sh
./reconftw.sh -d target.com -r
For other ways of installing you can refer to the official documentation.
Example usage : ( Taken from official documentation )
To perform a full recon on single target
./reconftw.sh -d target.com -r
To perform a full recon on a list of targets
./reconftw.sh -l sites.txt -r -o /output/directory/
Perform full recon with more time intense tasks (VPS intended only)
./reconftw.sh -d target.com -r –deep -o /output/directory/
Perform recon in a multi domain target
./reconftw.sh -m company -l domains_list.txt -r
Perform recon with axiom integration
./reconftw.sh -d target.com -r -v
Perform all steps (whole recon + all attacks) a.k.a. YOLO mode
./reconftw.sh -d target.com -a
Show help section
./reconftw.sh -h
Is it worth using ReconFTW?
ReconFTW itself is not a different tool but it’s a collection of some of the most used tools. It makes the work easy as we don’t need to keep installing all the tools one by one and use them separately. With just one command it fires up all the tools and shows us the results relevant to us. Do try out this tool.


