TabNapping
In this article we’ll take a look at a form of Phishing attack called TabNapping a phrase coined by Aza Raskin a leading Security researcher in 2010. This type of attack, whilst not widely known is being more commonly used as an attack vector by threat actors. TabNapping is a variation of Phishing attacks which traditionally are delivered via email and exploited by clicking on malicious links.
Modern web browsers can rewrite tabs after a web page has loaded which can provide malicious attackers the threat vector to compromise the victim. The Same-Origin Policy is a security mechanism intended to limit the ability of a website to interact with resources outside the source domain. However, this can be too restrictive with various methods implemented to bypass the constraints. The TabNapping attack takes advantage of Cross Origin Resource Scripting which I recently wrote about here CORS.
As a controlled mitigation CORS is used by websites to allow subdomain access, and trusted third parties. Implementation must be done carefully as misconfiguration or configuration not sufficiently secured can result in exploitable vulnerabilities. Once such vulnerability is TabNapping which relies upon a simple JavaScript to detect if, or when the user focus has shifted to another browser tab, or remains inactive for some time.
What is TabNapping?
TabNapping is both a phishing attack and an exploit. This is quite a clever and devious technique in which unattended tabs (i.e., tabs that have been left open for some time) are hijacked. The tab is then redirected to a malicious website that may duplicate or seem very similar to the original. The objective is the same as a traditional phishing attack in which the attackers try to exploit their victims via links within emails or webpage. This form of attack is more difficult to educate or defend against because victims do not actively have to click a malicious link for the redirection, or to visit a malicious site.
The target URL is then redirected prompting the user to provide login details and passwords by imitating a known website which the victim would ordinarily trust. The attack takes advantage of modern browser pages to rewrite tabs after the page has loaded.
How does TabNapping happen?
Now that we understand what TabNapping is, and how it is exploited let’s look at the process, and mitigation. I’ll then demonstrate the attack emulation in a lab environment. Besides the obvious of verifying the URL in the browser address bar before logging into a website & also check that the site is using a valid digital certificate. Another effective control is to make use of Mobile Apps rather than a using mobile browser, which are notoriously made targets of by attackers. To fully understand what’s happening in the browser we need to understand the techniques used and provides some of the best practices to mitigate these:
Reverse TabNapping using links – when a victim clicks a link with target=“_blank” the browser can be redirected by the attacker to a malicious website under the attackers control. Once the malicious link is accessed the original page can be controlled using the window.opener object this is mitigated by using the rel=”noopener” attribute in your links which sets the window.opener to ‘null’
Reverse TabNapping using Frames – The same concept of viewing Ads within a website by loading another website into the host website using an iframe redirects can be made using the window.parent property. To mitigate this a best practice is to sandbox the frame using the attribute <iframe sandbox=”allow-scripts allow-same-origin” src=https//www.someRandomWebsiteURL.com”>>/iframe>
Isolation policy – although not a TabNapping technique – is when the recent browser feature fetch-metadata, which is essentially a HTTP request header, which provides the browser extra detail and context from where the request originated from.
Now that we are aware of the attack technique, how it impacts, the processes used and some of the controls we can implement let’s take a look at an attack emulation. For this I’m using a Kali Linux & CentOS box.
First, we need to install ngrok which is required to port forward
Download and install ngrok then extract the package.
[andy@centos~]$ sudo tar xvzf ~/Downloads/ngrok-v3-stable-linux-amd64.tgz -C /home/andy/
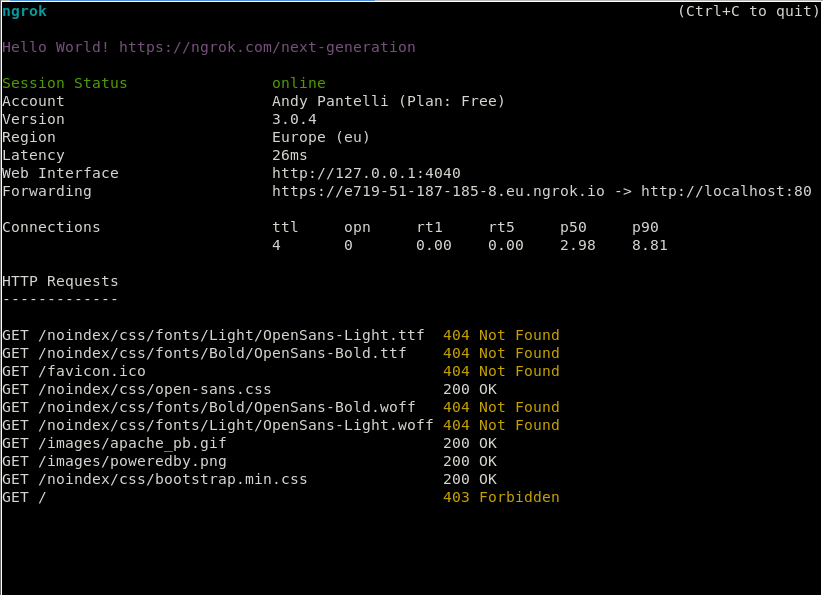
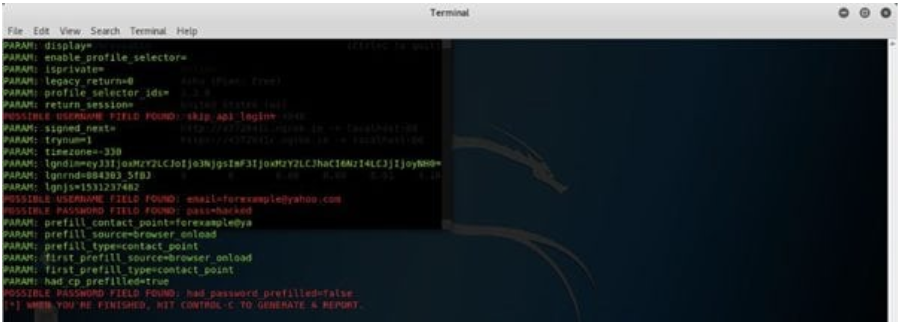
From the Kali box, locate Social Engineering Attack, then Website Attack Vectors and finally select option 3 or 4, then Site Cloner. Next copy the ngrok address shown on the CentOS box and enter the URL to clone, which in this case is facebook.com. You can use the same CentOS box to click the ngrok link shown in the example which should then load the Facebook login page, once the credentials are entered into the login prompt these will be captured on the Kali box as seen below which then gives our attacker
How much should we worry about TabNapping?
TabNapping is highly effective technique used by attackers, with users becoming more technically aware and cautious online this attack vector is relatively easy to implement, very effective and difficult to protect against from the victim perspective. Whilst I have demonstrated an attack emulation using a redirect, for obvious reasons I have not demonstrated a technique of using an idle tab to redirect. Numerous Proof of Concepts exist should you wish to learn more.








