5 Steps for Installing Maldet (Linux Malware Detect)
By Nazifa Alam
Linux Malware Detect (LMD), commonly abbreviated as Maldet, is a malware scanner for Linux released under the GNU GPLv2 license. What sets Maldet apart from other malware scanners is its design around threats faced in shared hosted environments. Maldet functions by using gathered threat data from network edge intrusion detection systems to remove malware being used in real time. For each detection, a signature is generated.
In addition to this, threat data is also collected from user submissions with the LMD checkout feature and from malware community resources. The signatures by LMD include MD5 file hashes and HEX pattern matches which can be exported to any number of detection tools without too much difficulty.
How to Install Maldet
Before you can use Maldet, you will need to first download it, unpack and install it onto your server. By following the five steps laid out below, you will be running Maldet soon after.
- You will first need to login to your server with root user.
- The only place you can find the Maldet installation pack from the project’s official website in the form of combined multiple files. The tarball contains the source code needed to download the latest version.
The following command can be used to download the Maldet:
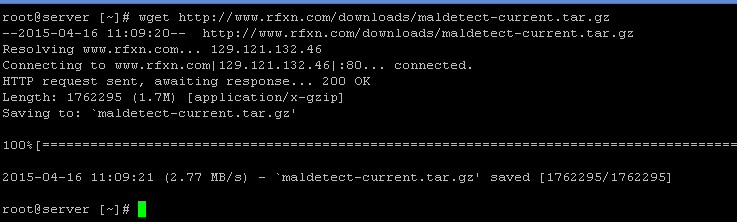
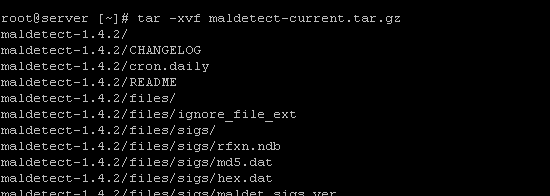
3. After the tarball is downloaded, you will then need to unpack it and input the directory where it’its contents were extracted. The following command tar -xvf maldetect-current.tar.gz can be used to extract the file.
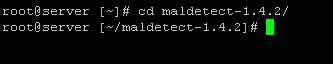
4. You can then use the command Cd maldetect-1.4.2 to move to the Maldet directory:
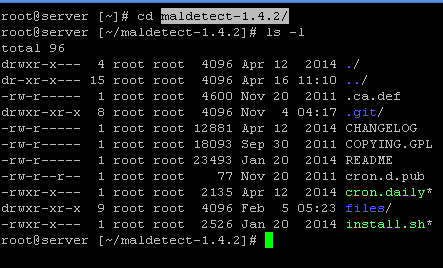
5. Once you have moved to the Maldet directory, you will then need to use the command ./install sh to perform the installation script.
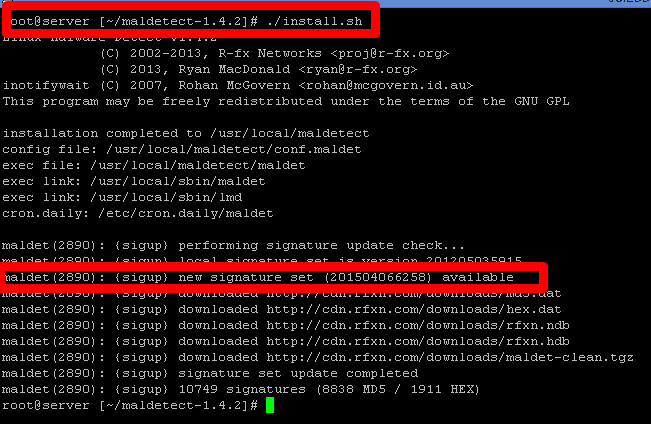
You can also download Maldet using wget as followed:
- Going to the path cd /usr/local/src
- Downloading the tar file from wget http://www.rfxn.com/downloads/maldetect-current.tar.gz
- Extracting the file using the command tar -xzf maldetect-current.tar.gz
- Going to the Maldet folder cd maldetect-*
- Then running the following command sh ./install.sh or sudo sh /install.sh
How to run a Scan using Maldet
Once Maldet has been installed, you can execute a scan upon your server to detect for corrupted files. To perform the scan on your server, you will need to enter the command maldet -a which should then give you the following display:
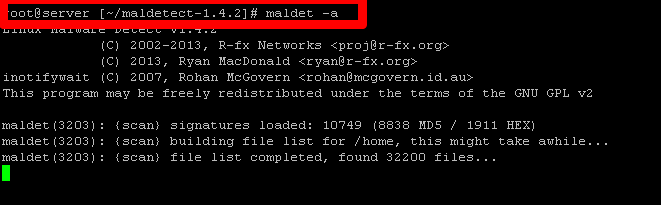
In order to run the process in the background, you enter b as the directory contains thousands of files which will take a while to complete. For example, a Maldet scan for a newly set up 5.7 version of WordPress which contains 2189 files will tale 3 minutes to complete.
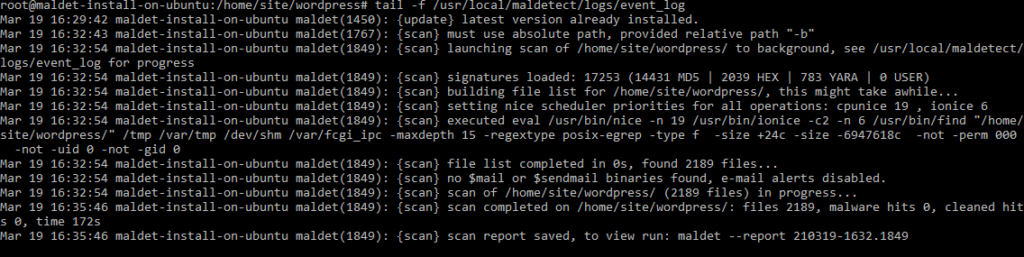
To oversee a scan in real time, you can use tail. Furthermore, to monitor the event log, the command tail -f /usr/local/maldetect/logs/event_log can be used.
You will then be presented with the following display:
Configuring the Maldet program
By default, all options are provided in the configuration file and therefore, users simply need to configure the program according to their needs. However, prior to making any changes, the following options should be reviewed.
- email_alert: If you wish to receive email alerts, it should be set to 1.
- email_subj: Where you need to set your email subject.
- email_addr: Where you need to ass your email address to receive malware alerts.
- quar_hits: This is the default quarantine process for malware hits which needs to be set as 1.
- quar_clean: This cleans the detected malware intrusions and needs to be set as 1.
- quar_susp: This is to be set depending on your requirements as it is the default suspect action for users with hits.
- quar_susp_minuid: Minimum user ID which can be suspended.
You can enter nano /usr/local/maldetect/conf.maldet to make changes depending on your needs. The commands maldet -u or maldet -d can be used to carry out updates and to scan files for a particular user, maldet -a /home/username/ can be used.
To examine all users a part of public_html paths, the command root@server [~] # maldet –scan-all /home?/?/public_html and root@server [~] -maldet –scan-all /home can be used.
To scan for modified content part of the same path, root@server [~] # maldet –scan-recent /home?/?/public_html 5 can be used. Changes from 5 days ago can be traced using this command.
If you forgot to turn on the quarantine scan whilst conducting a scan, you can use root@server [~] # maldet –quarantine SCANID to quarantine all malware results gathered from a previous scan.
To clean malware results from a previous scan for which the feature was enabled, you can use root@server [~] # maldet –clean SCANID to complete this.
If you have a file that you wish to restore after either manually cleaning it or flagging it as a false worry, you can use the following commands:
- root@server [~] # maldet –restore config.php.2384
- root@server[~] # maldet –restore
- /usr/local/maldetect/quarantine/config.php.2384
Useful Commands to keep in mind
Below are some useful commands that you may at some point need to use:
- To scan a directory: maldet -a /full/path/to/directory
- To conduct a background scan: maldet -b -a /full/path/to/directory
- To receive an email of a completed scan: maldet –report $SCANID [email protected]
- To monitor directory: maldet –monitor /full/path/to/directory/
- To monitor users: maldet –monitor users
- To receive a list of all reports: maldet -e list
Conclusion
Maldet is highly useful for shared hosting as it provides detailed results of scanned files, some of which may have been reported as malicious. Configuration of the program is dependent on the user, offering high flexibility. There is also no need to manually input login details to remove any detected malicious files or to disable users.
It is a program set apart by its particular design regarding threats faced in shared hosting environments through network edge intrusion detection.








