Written By: Ricoh Danielson
Vulnerability management is not a one-time task; it is an ongoing process to identify, classify, prioritize, remediate and mitigate the weak spots in software systems. Conflict is where opportunities are born, so responding to an incident is the best chance to understand the vulnerable points of our infrastructure.
The Significance of Live Vulnerability Management
Vulnerabilities are the key that leads to an incident or a cyber event. Understanding how these vulnerabilities have been exploited and leveraged to continue the attack will pay tenfold and give large amounts of data with IOCs.
Finding out where the vulnerabilities reside also provides a great inside look of the environment or the application along with the weaknesses that were exploited during the attack.
Technical Requirements for Conducting Live Vulnerability Management
Let’s take a closer look at the technical requirements for vulnerability management during the incident. In some cases, there will be tools that will help us identify and isolate some areas of compromise.
There are a lot of tools like Tenable Nessus, Engine Management and others. Let’s assume for this process that you are a boot-strapped organization that only has access to free or open-source tools. From this point of view, we were more likely to rely on an app called OpenVas.
This product is a free tool that many start-ups use and it provides a great deal of information when deployed. As we can see below, the information provided not only identifies the vulnerability but also provides a timeline along with remediation.
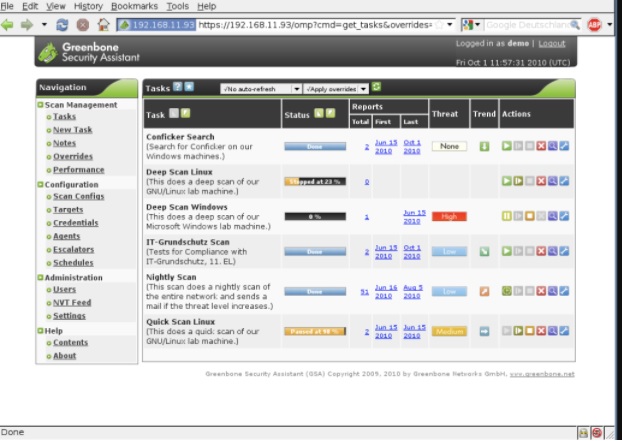
Deep diving into the metadata, as shown above, will provide a bigger picture of how the adversary infiltrated the organization.
Is it a good idea to choose a manual process over tools?
Using tools during the incident to understand vulnerabilities is a great method for understanding what happened. At the end of the day, however, the cybersecurity professional must be able to roll his sleeves and understand from a technical and tactical point of view what it might look like and its true form. Many tools provide cool images but miss the mark when it comes to metadata.
In the section below, we can understand the rule setting with conditioning over a period of time that will give us sensitivity and a reading level that this might look like in terms of vulnerabilities.
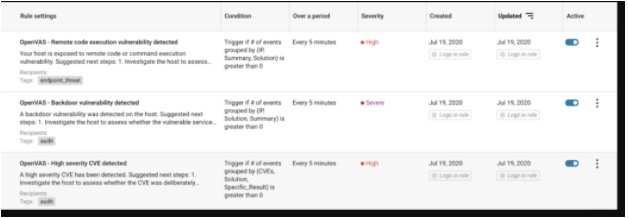
Following are steps to perform Vuln Management.
When it comes to vulnerability management or incident response, it is essential to set up the right configuration. Deploying this throughout the environment will be the best way to understand vulnerabilities.
At the same time, there must be criteria measurements such as a schedule. Ensuring that the schedules account for off-peak hours along with non-critical business hours will help build a fuller picture of the environment and cancel out white noise. Below is a way to capture and plan timely scans to capture these data points.
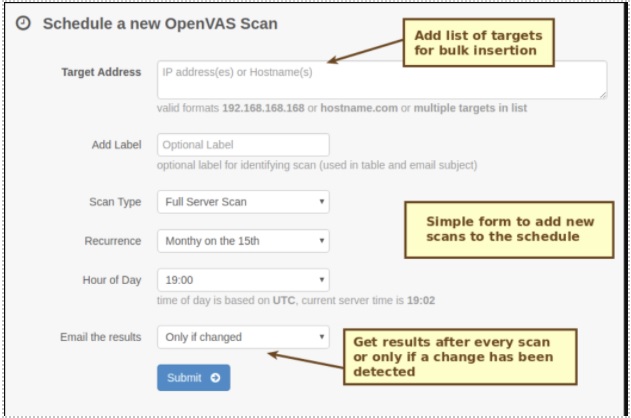
Analyzing findings and data elements of a Vuln management during an active IR
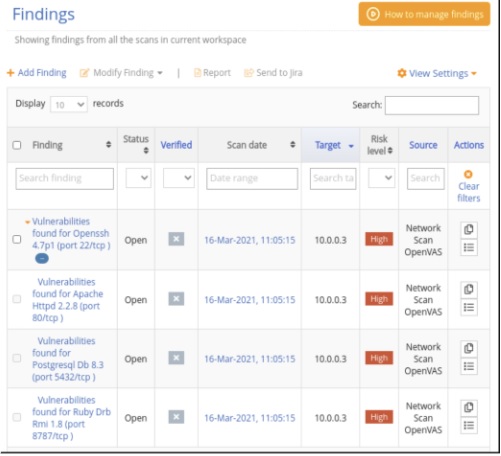
Now begins the analysis. Understanding what devices, environments, and infrastructure may be out of the patch cycle or exploiting them can be a cause of route or a source of truth in which the threat is used to exploit.
In the capture below, we see that there is an open SSH as well as other vulnerabilities such as open ports and existing Apache vulnerabilities. This is very critical as the actors will try to use these as a libertine point for data exploration and other means of attack. However, the analysis does not stop there. There might be a reasonable business decision why these vulnerabilities are pre-existing and need to be taken into consideration.
Again, this is where the cyber security expert’s rubber meets the business aspect road.
Summary
In summary there is no wrong answer and there’s no right answer of how to conduct vulnerability management during the incident response. After all, it will be the best effort forward to make sure they get the best metadata for the incident.
More tools don’t necessarily mean more visibility. It just means more things we must look at. I believe that accurate vulnerability management that is relevant to the response to the incident during the cyberattack is what is needed. This is where hard technical skills set and roll up your sleeves or pay high dividends versus relying on a tool.
Understanding the command line and the native way to conduct vulnerability management assessment and incident response can help provide skills as well as a way forward to make an instant response. Whether you are a small organization or a large organization, what matters is that you are your own first responder.








