5 Must have burp extensions
Written By: Indrajeet Bhuyan
Last week a friend of mine who is from a non-security background asked me to recommend one tool which he should learn in security. I instantly suggest Burp Suite. Burp Suite has been the number one choice for security professionals today because of its rich features and easy-to-use interface. Most web pentesting today can be done with the Burp suite alone and it gives you a taste of both manual and automated scanning.
What makes Burp suite stand out from its competitor is its extensions. Using Burp extensions, we can add more features to the Burp suite and customize it according to our needs. We can easily download extensions from the Burp store (it’s like the play store for burp suite). If the extension is made in Java, it can be installed directly, but if the extension is made in Python we need to install Jython.
Today in this article I will share with you 5 must-have burp extensions which will make your burp suite more powerful and help you in your pen-testing.
Authorize
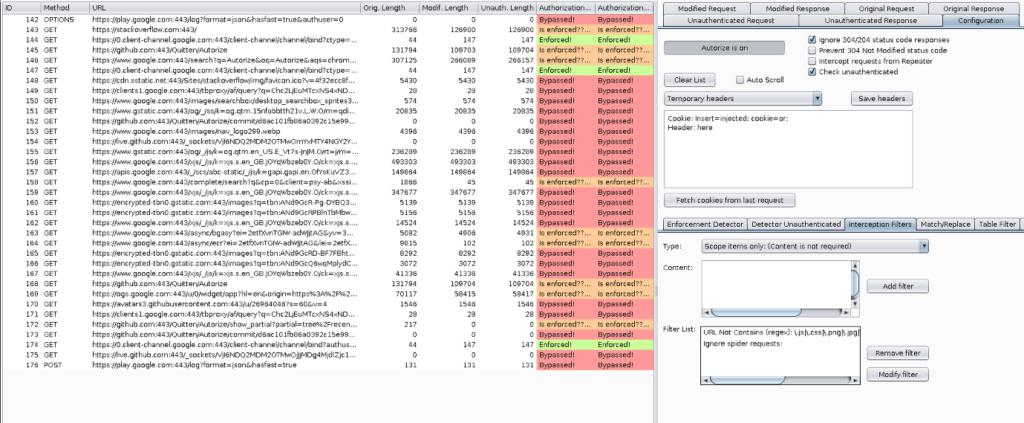
Generally, when we test for authorization vulnerabilities/IDOR vulnerabilities, we create two different accounts and repeat each request manually to see if account A can do the action of account B or if we are testing vertical privilege then we use two accounts – 1 high privilege account and 1 low privilege account and see if lower privilege account can do the action of higher privilege account. This whole process consumes a lot of time and is very tiresome.
Authorize is an extension that can help you solve this issue and automate the process to a great extent.
All you need to do is give Authorize the cookies of a low privilege user and navigate the website with a high privilege user. The extension automatically repeats every request with the session of the low privileged user and detects authorization vulnerabilities.
Turbo Intruder
Fuzzing sometimes can get boring due to slow speed. Maybe this is one of the reasons why in the Burp Community version Portswigger slows down the intruder speed but provides high speed in professional version. If you are someone who wants the fastest and most reliable fuzzer then Turbo Intruder is your answer. When most tools struggle to reach 1000 HTTPS requests per second, Turbo intruder uses a selection of custom HTTP stacks to exceed a massive 30,000 requests per second.
Active Scan++
Burp professional has an inbuilt vulnerability scanner that one can use to find flaws. But sometimes this scanner fails to find many flaws. This is where Active Scan++ comes into play. Active Scan++, a burp suite extension created by James Kettle who is working as a Director of Research at Portswigger – The company behind Burp Suite.
Once this extension gets integrated, it can help in discovering vulnerabilities like Host header attacks, Password reset poisoning, XML injection, and many more.
It also adds checks for the following issues:
- Blind code injection via expression language, Ruby’s open() and Perl’s open()
- CVE-2014-6271/CVE-2014-6278 ‘shellshock’ and CVE-2015-2080, CVE-2017-5638, CVE-2017-12629, CVE-2018-11776
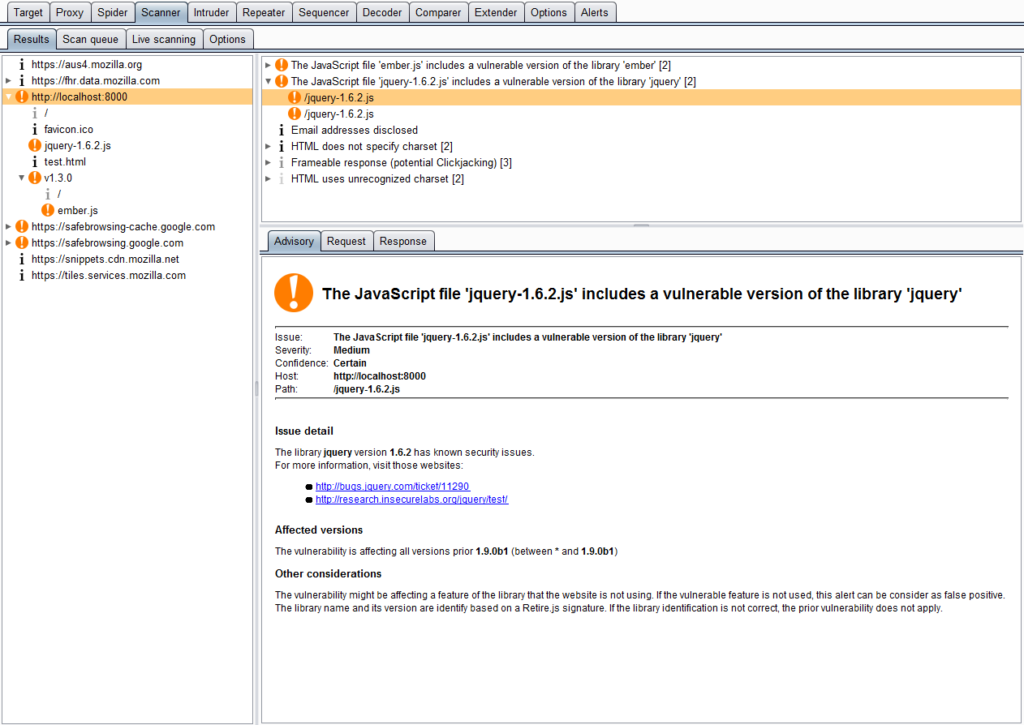
Retire.js
Many a time while developing web applications developers use a lot of 3rd party codes (libraries). While using libraries makes developers’ work easy, if any vulnerabilities get discovered in any of these libraries then all the applications that use these libraries automatically become vulnerable. One classic example is Log4j.
Retire.js, as the name suggests, looks at JavaScript files that are loaded when we request a page and identifies those which are vulnerable based on various signature types like URL, filename, file content, etc.
Once installed, this extension works automatically without any configuration and starts showing results.
JSON Web Tokens
JWT, or JSON Web Token, is an open standard used to share security information between two parties — a client and a server. Each JWT contains encoded JSON objects, including a set of claims. JWTs are signed using a cryptographic algorithm to ensure that the claims cannot be altered after the token is issued. JWT is becoming popular for securing APIs. Testing for JWT-based vulnerabilities is a time-consuming process just like finding IDOR. As one needs to decode the token, manipulate it, encode it in third-party tools and websites like jwt.io and insert it back into the burp suite.
To solve this issue, we can use an awesome Burp extension called JSON Web Tokens (JWT4B). It helps penetration tester in the following ways:
- Intercepting requests and responses
- Manipulation of payload
- Changing algorithms
- Resigning JWTs
- Decoding of JWTs in the history view
- Integrity verification
- Dedicated tab for tokens that are not transferred through the authorization header
This tool speeds up the whole process of finding JWT vulnerabilities and you don’t need to move out of burp to perform any of the tasks.
Conclusion
Burp Suite is a powerful tool for penetration testing. And burp extender makes it even more powerful. In this article, we explored only 5 extensions but there are many more useful extensions available that can help you in your pen-testing. Explore the burp extension tab and try out different extensions. You can sort it based on ratings and popularity and start by trying the top-rated extensions first.








