Thanks to the overwhelming feedback from the SecPro community, we’re starting up our next piece of industry analysis – our ten favourite open-source intelligence (OSINT) tools that you can implement in your day-to-day work life. We took a vote amongst the team and almost compared it to the GitHub most popular OSINT tools list, so we’re sure that you will find plenty of value in our breakdown.
Sadly, we’ll have to leave the MITRE D3FEND matrix analysis for another time. If you would like to analyze the D3FEND matrix (which is still under construction), you can find the 0.10.1-BETA-1 version here.
What is OSINT?
OSINT stands for open-source intelligence and refers to any tools which are both open-source and concerned with collecting or managing data. For a cybersecurity professional, these are obviously useful in the usual flow of the working day, but the range of tools is vast – everything from newly open-sourced Have I Been Pwned? to persona creation tools is included in this ambitious and expansive field, so knowing where to start can be difficult.
If you have not spent much time dipping your tops into the OSINT waters, using the OSINT Framework is a necessary first step to getting ahead of the adversary. Now that we’ve established that, on with the Top Ten!
#10: Have I Been Pwned?
As mentioned above, Have I Been Pwned? is an essential service for people working with intelligence these days. Not only is it the most famous hub for compromised email/password combinations, it is also the best place to turn for updates on industry-wide data breaches which could have knock-on effects for your organization.
Using Have I Been Pwned?
First things first, let’s look at the name. If you grew up in the 2000s, you would remember the slang term “owned” or “owning someone” – basically getting one over on someone else. Due to the perception of the adversary’s poor typing skills, an intentional misspelling has been used in the title. And
If you’ve never used this tool before, you should see this display when you access the website through your browser. It’s a very simple site that has a place to enter an email address or phone number, as well as a few other functions that we will look at in a moment.
Of course, we’re not here to evaluate the aesthetic choices of the Have I Been Pwned? development team – let’s take it out for a test spin. In the interest of science, I decided to use a long-abandoned email address that I had started using in my youth (a time further away than I would like to admit). I typed the address into the search bar and readied myself to find out how many threat actors are able to potentially capable of accessing all the spam that presumably fills that email box these days.
Now that we’ve inputted our address, let’s have a look at the damage.
Diagnostics and Have I Been Pwned?
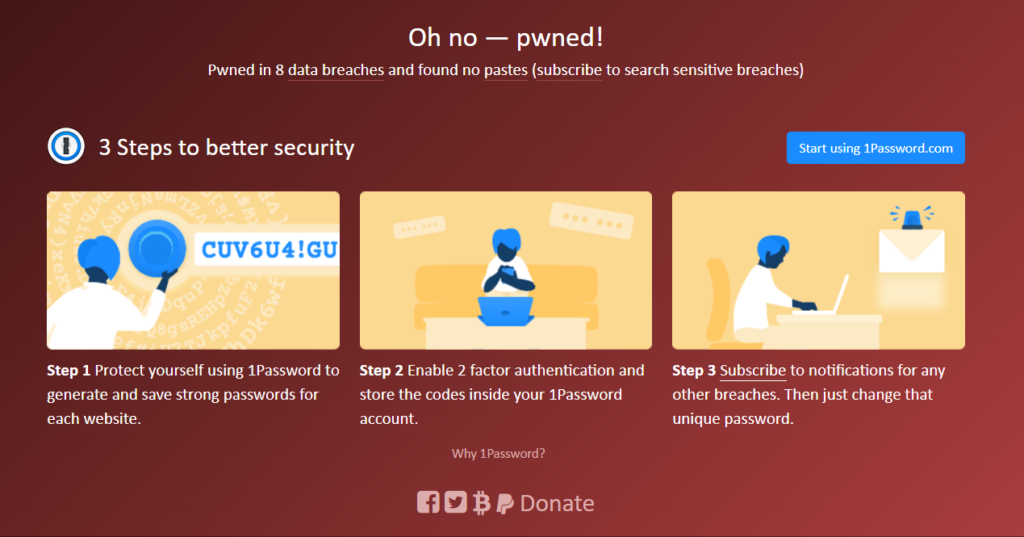
Oh dear – my old email address has been left vulnerable in eight separate data breaches. As you can see, Have I Been Pwned offers access to sensitive data breaches through their subscription service and also seems to be working with 1Password.com, a password manager. Many password managers offer effectively the same service, so using once at all is often a better approach to strategy than worrying about which particular service you sign up with.
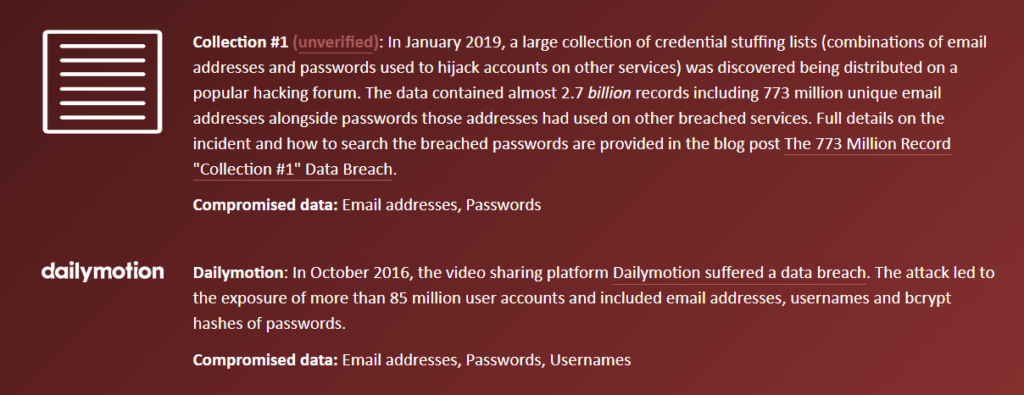
From a user perspective, you can find the richest data just under the “oh no – pwned!” message. This is where the breaches are listed, including the types of compromised data that the adversary potentially has access to.
Using Have I Been Pwned? at Enterprise Level
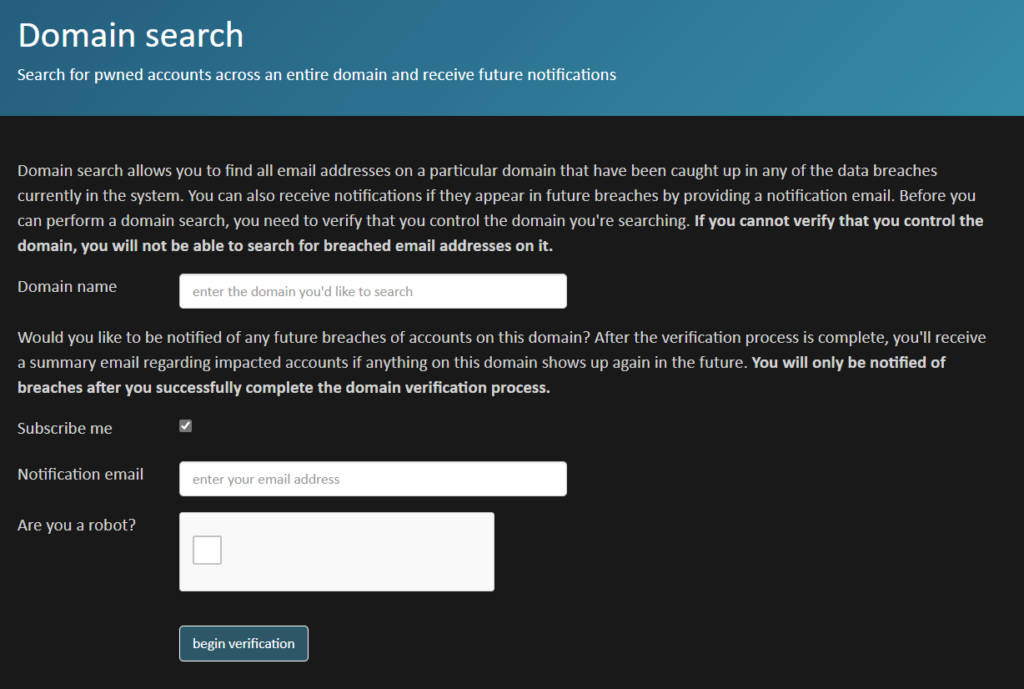
Of course, you wouldn’t exclusively be working with the personal side of Have I Been Pwned? – instead, you will have to turn to the automated notification system and domain search features to get the most out of the service.
By using Notify me, you can receive automatic updates about data breaches that the service finds. As the team aggregates and analyzes hundreds of data dumps and pastes, this is one of the most expansive tools that you can use. If you enter your email (and any other emails relevant to your organization) and sign up to be notified of the “pwnage”, you can receive automatic updates when the adversary gains a foothold.

Similarly, using the Domain search function allows you to track any domains that you are responsible for and get updates the second that you are caught in a data breach. A very handy tool for people who don’t have time or resources for threat intelligence hunting in their day-to-day workflow.
Pwned Passwords – Setting Up a Mature Security Culture
For organizations that still are relying on manually generated passwords, i.e., not a password manager with a password generator, the Pwned Passwords feature is key for people who need a quick tool to verify whether a password is being abused by the adversary in a brute force password repository or a rainbow table.
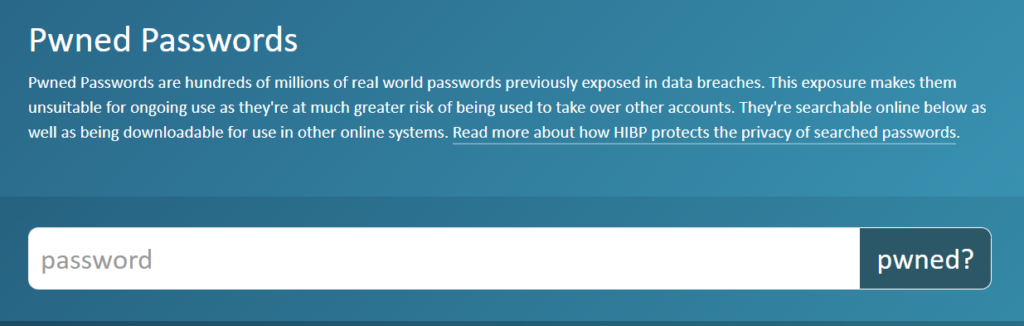
If you need evidence for why someone shouldn’t use “password123” for their company account (or any account!), just type it in and watch the report generate.








