Are Wipers the New Weapon of the Adversary?
Written By: Austin Miller
Despite the enduring popularity of ransomware attacks among adversaries over the last few years, there has been an increase in the usage of a new kind of malware – wipers, also referred to as wiper viruses which begs to the question: Are Wipers the New Weapon of the Adversary? Unlike ransomware, wipers aren’t created with the intention of extorting a payment from a victim. Instead, the adversary is only intending to cause harm through data destruction, system corruption to the point of inoperability, and reputational damage that comes from these attacks which lay waste to entire companies.
We have seen numerous wiper attacks launched against Ukrainian governmental systems and businesses over the past month, leading us to believe that the malicious source is Russian or Russian-aligned. Regardless, wipers are a fascinating subject because they really put the malicious in malware. In this lab we will answer the question: Are Wipers the New Weapon of the Adversary?
What is a Wiper?
As the name suggests, wiper malware is only concerned with destroying information and rendering systems incapable. If the adversary does intend to simply wipe information from the victim’s computer or server, there is a distinct possibility that there is no way to retrieve the data. This makes wipers the kind of malware quite different from other adversarial favorites such as ransomware or Trojans in that they do not intend to capture information that can be used against the victim e.g., as a ransom.
Because wipers do not generally lead to great monetary gains for cybercriminals, they are quite rare. However, some high-profile wipers include:
- Shamoom, a wiper that targeted Saudi Aramco and other Middle Eastern oil companies in mid-to-late 2012.
- Dark Seoul, a wiper that targeted South Korean companies in 2013.
Why would the adversary use a wiper?
Despite there being no way to restore data to a wiped system, the malware delivers an error message to the victim:
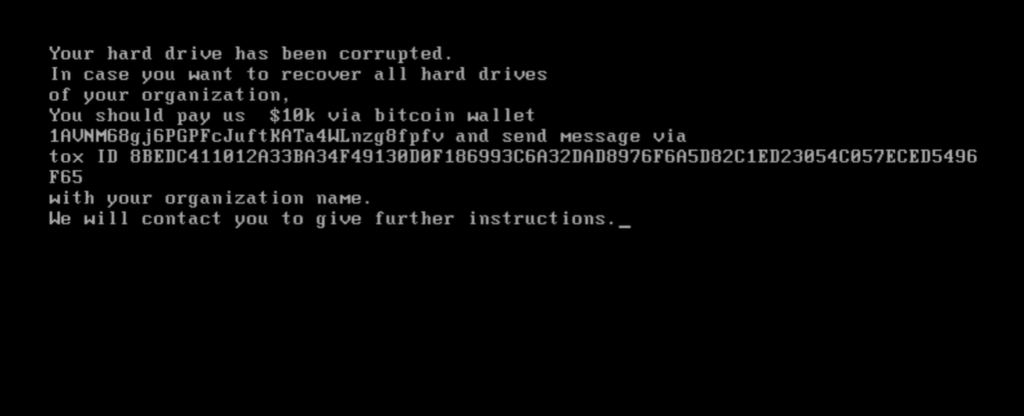
This error message displays a bitcoin wallet address and a demand for $10k (0.25BTC) to restore “all hard drives of [the] organization”. In mimicking the tactics of a ransomware gang, the wiper virus still has possibility of harvesting “ransoms” from people desperate to get their data back. Of course, there is no way – the virus writes over the data and deletes it all.
How does WhisperGate work?
Although WhisperGate, HermeticWiper, and IsaacGate function differently, they are very similar. What is clear from looking at the code for WhisperGate is that the wiper virus was put together quickly and with the intention of causing maximum damage, not necessarily being well-coded or difficult to analyze pieces of malware. For that reason, it’s easy to use a program like IDA to analyze the source code.
We will deep dive into the nature of HermeticWiper and IsaacWiper next week – as they are more advanced versions of the malware, they deserve to be analyzed in their own right.
Initial Infection
When the malware is on the system, we can see that the parameter CreateFileW is called. At this point, WhisperGate is preparing to write over everything that it has access to in the system.
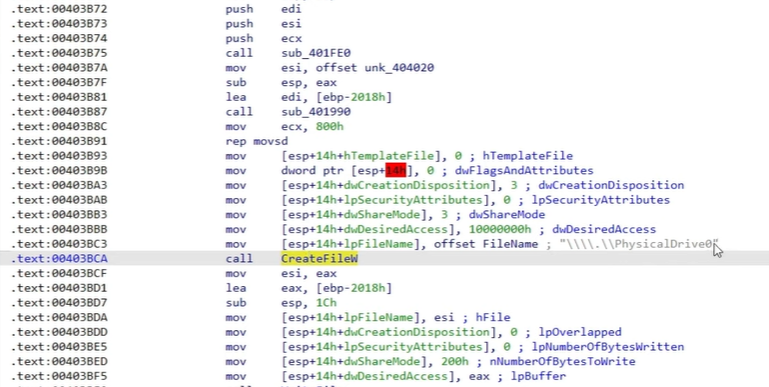
And then the WriteFile parameter starts to overwrite the contents of the physical drive. If this part of the code has run, you can say goodbye to your data – the code has no way to restore the data it overwriters, so the only intention here is to destroy.
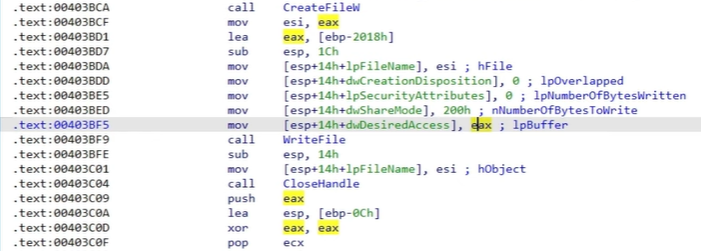
From nNumberofBytesToWrite, we can see that 512 bytes are written to the head sector of the disk. This corrupts the entire disk and renders the contents inaccessible to the user.
How does it overwrite the sector?
This is actually quite difficult to find in the malware – most of it is made of generic nonsense, so trying to find an encryption tool that could be reverse engineered is wasted time. However, when we look at the piece of code below:
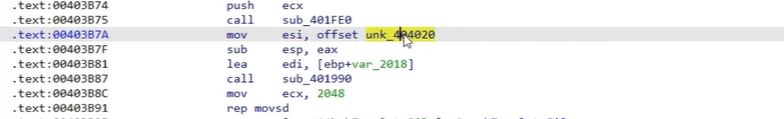
We can see the content that overwrites the master boot record (MBR):
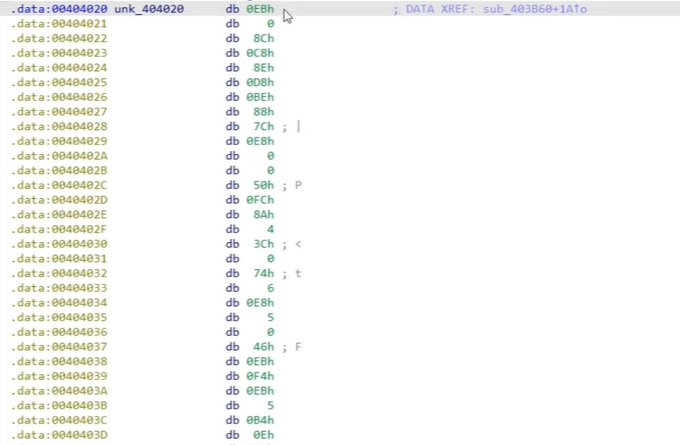
This is, of course, not very clear from the code itself. When the malware runs, it replaces the MBR with the below ransom note so that it launches automatically when the system would usually boot. If we shift our view around a little more, we can actually see that the code is mostly obfuscated – there’s very little aside from the Write command and the buffer.

Everything else that we find in the code is either garbled code or a repeat of the ransom note, meaning that this is an extremely simple piece of malware that has caused a relatively large amount of destruction in Ukraine and the surrounding areas.
How do I defend against these wiper viruses?
Wiper viruses are especially fearsome because they are not designed by sophisticated cybercriminals who want to capture data and extract ransoms. These viruses are simply designed to destroy and the largely uninteresting source code tells us more than you might think – if the only functionality is to overwrite and display a ransom note, this is the work of opportunistic adversaries who are just trying to earn a quick buck.
As always, defending yourself against these kinds of malware is both reactive and proactive:
- Create backups that are not accessible over your network, either by airgapping the backups or by storing them remotely
- Sanitize and check over incoming emails that may be phishing attacks containing a wiper
- Keep all software up to date to stop exploits which allow malicious agents to send serious malware into your systems.
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes. Join the newsletter here.








