Post Credit: Austin Miller
Every year the Superbowl rolls around and America celebrates with a larger than life occasion. But this year, a ransomware gang came back from almost a year in the wilderness to throw the celebrations into disarray. The BlackByte ransomware (known primarily as an RaaS that was first noticed in July 2021) took down the San Fransisco 49ers network systems on Superbowl Eve, casting a grim shadow on the American government’s plans to make 2022 the year that the ransomware gangs get what’s coming to them.
In truth, the attacks have been further reaching than an isolated server attack on a football team. The US government has confirmed that at least three attacks were launched against critical infrastructure sectors, one of which was the government. Now that the BlackByte gang has reintroduced itself to the world, we need to look at how it works, how it enters a system, and how you can stop it taking down your network.
Wait, wasn’t BlackByte already stopped?
Right you are – BlackByte originally surfaced in July 2021 and caused problems for organizations around the world. However, security researchers saved the day for potentially thousands of people by finding out that BlackByte’s encryption method was pretty amateurish.
Whereas most ransomware gangs would use a variety of encryption methods to lock down a variety of targets, it quickly became apparent that the BlackByte gang had only used one. This meant that when a victim had paid the ransom and received the decrytion key, everyone was able to decrypt their systems by using the same tool. To say the least, this was a massive oversight by the cybercriminals.
But now that BlackByte is back, I’m sure that we will see attacks which aren’t so easily circumvented.
Do I need to worry about BlackByte?
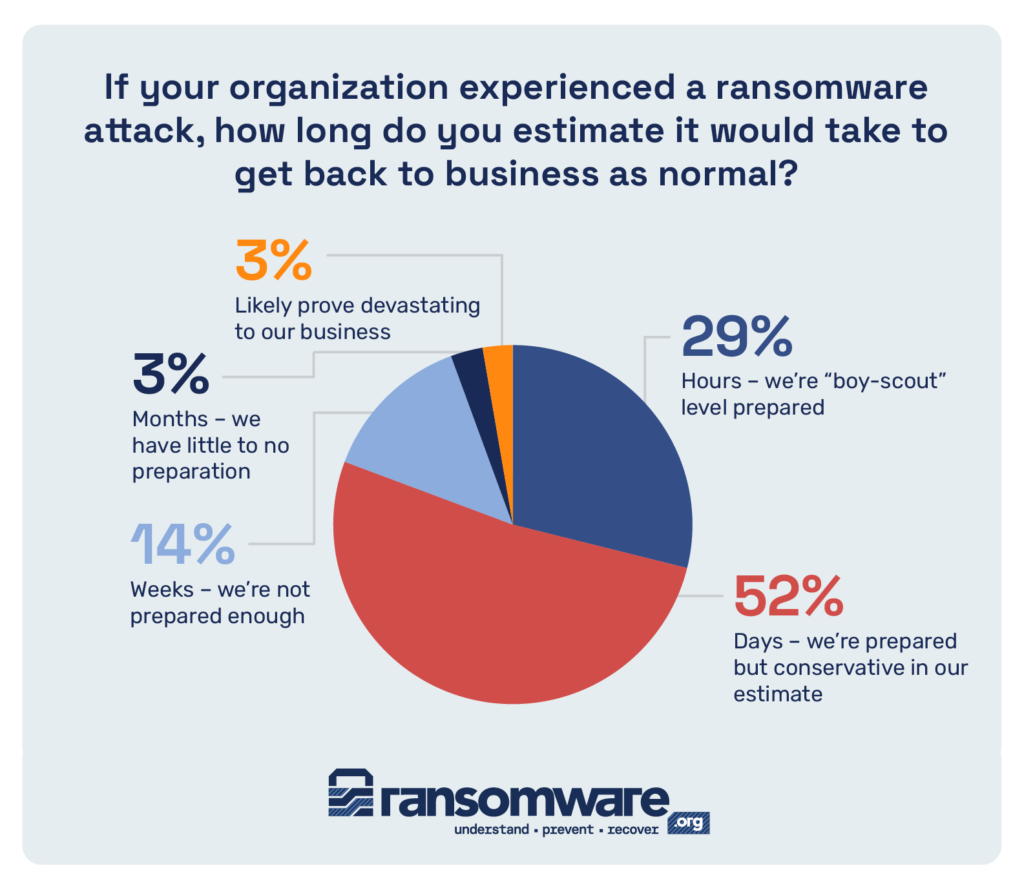
All ransomware is worrisome. In a world where 71% of organizations estimate that it will take days if not months to recover from a ransomware attack, being vigilant and avoiding infection should be a top priority for everyone.
However, BlackByte is a distinctly less threatening form of ransomware. Other ransomware gangs usually have a plan of attack that plays out as such:
- The ransomware infects an endpoint, spreads around the network, and encrypts critical and sensitive aspects of the network.
- Data is stolen and held by the ransomware gang on threat of leaking the details, potentially causing millions of dollars in damage in terms of data protection.
- The infection may also have a tertiary attack built into the code or launched manually by the gang on failure to pay – the most notable example of this addition attack is BlackCat’s DDoS threats for anyone who doesn’t give into their commands.
Much like BlackByte’s first iteration, however, this new form of ransomware has no method for extracting data from a network. For that reason, it’s expected that any organizations that fail to pay the ransom will not find any stolen data leaked. Possibly lost forever, if no backups were made. But the actual threat of BlackByte is significantly less than other crypto worms such as LockBit 2.0 or BlackCat.
What are the Indicators of Compromise for BlackByte?
Although most organizations should have adequate defenses against the first iteration of BlackByte (namely in the form of updates to close the Microsoft Exchange Server vulnerabilities), it has become apparent from the new Indicators of Compromise (IOCs) that BlackByte has change its tactics, techniques, and processes (TTPs).
Suspicious files discovered after infection
WindowsMicrosoft.NETFramework64v4.0.30319Temporary ASP.NET Filesroote22c255992c7e946 |
inetpubwwwrootaspnet_client |
Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauth |
Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthCurrent |
Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthCurrentthemes |
Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthCurrentscripts |
Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthCurrentscriptspremium |
%AppData%BB.ico |
%AppData%BlackByteRestore.txt [the ransom note left in all folders with encrypted files] |
%AppData%dummy |
%HOMEPATH%complex.exe [the ransomware executable] |
Userstree.dll [contains the message “Your HACKED by BlackByte team. Connect us to restore your system.”] |
Observed commands discovered after infection
The full list of observed commands that are executed by complex.exe is extremely long, so here are some highlights and commentary on the most interesting aspects of BlackByte.
cmd.exe /c powershell -command “$x = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String(‘VwBpA’ +’G4ARAB’+’lAGYA’+’ZQB’+’uAG’+’QA’));Stop-Service -Name $x;Set-Service -StartupType Disabled $x” |
schtasks.exe /DELETE /TN “”Raccine Rules Updater”” /F |
cmd.exe /c vssadmin resize shadowstorage /for=c: /on=c: /maxsize=401MB |
cmd.exe /c vssadmin resize shadowstorage /for=c: /on=c: /maxsize=unbounded |
powershell.exe $x = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String(‘RwBlA HQALQBXAG0AaQBPAGIAagBlAGMAdAAg’+’AFcAaQBuADMAMgBfAFMAaABhAGQAb wB3AGMAbwBwAHkAIAB8AC’+’AARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUAYwB0A CAAewAkA’+’F8ALgBEAGUAbABlAHQAZQAoACkAOwB9AA==’));Invoke-Expression $x |
sc.exe config SQLTELEMETRY start= disabled |
sc.exe config SQLTELEMETRY$ECWDB2 start= disabled |
sc.exe config SQLWriter start= disabled |
sc.exe config SstpSvc start= disabled |
powershell.exe Set-MpPreference -EnableControlledFolderAccess Disabled |
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();} [at this point, all shadow copies are deleted] |
To find a list of the full IOCs, consult the FBI Joint Cybersecurity Advisory Indicators of Compromise Associated with BlackByte Ransomware document here.
Next week, we’ll be looking at the TTPs of the BlackByte ransomware gang (and just know that there are a lot of them!) as well as the mitigations that you can put in place to defend your systems.








