The Clop threat group is a notorious cybercriminal organization that is known for deploying ransomware attacks against various targets worldwide. The group has gained significant attention and notoriety due to its sophisticated tactics and high-profile victims.
What is Clop?
Clop first emerged in early 2019 and quickly became one of the most active and successful ransomware groups. The group primarily targets large enterprises, particularly in the finance, healthcare, and retail sectors. They exploit vulnerabilities in networks and systems, often gaining initial access through phishing emails or by exploiting weakly secured Remote Desktop Protocol (RDP) connections. Once inside a victim’s network, they move laterally, compromising additional systems and spreading their ransomware to maximize the impact.
How has Clop attacked?
Multiple attacks have been launched by the Clop group prior to the recent outbreak across Europe and North America. Some of the most profile attacks include:
- Attack on Software AG (2020): Clop targeted Software AG, a German software company, and successfully breached their systems. The attack disrupted their internal operations and resulted in a significant financial impact for the company.
- University of California San Francisco (UCSF) Ransomware Attack (2020): Clop launched a ransomware attack against UCSF, one of the leading medical research institutions in the United States. The attack encrypted critical data related to COVID-19 research, causing operational disruption and highlighting the potential impact on vital scientific endeavors.
- Attack on Accellion File Transfer Appliance (FTA) Users (2021): Clop exploited vulnerabilities in the Accellion FTA, a widely used file transfer solution, to target multiple organizations worldwide. By gaining unauthorized access, they stole sensitive data and demanded ransom payments.
- Breach of ExecuPharm (2020): Clop targeted ExecuPharm, a leading pharmaceutical outsourcing company. The attack involved data exfiltration and ransomware deployment, disrupting their operations and potentially exposing confidential information.
How do I deal with Clop?
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) recently released a joint advisory to address the Clop ransomware threat. The Clop ransomware gang, also known as TA505, has been exploiting vulnerabilities in software solutions like Progress Software’s MOVEit Transfer and Accellion File Transfer Appliance (FTA) to steal data and carry out ransomware attacks. They employ a double-extortion technique, where they encrypt the victim’s files and then steal sensitive data. This gives them leverage to extort ransom payments by threatening to release or sell the stolen data if the victim does not comply.
Mitigation
To mitigate the threat of Clop ransomware and similar attacks, organizations are advised to take the following actions:
- Conduct an inventory of assets and data, identifying authorized and unauthorized devices and software.
- Grant admin privileges and access only when necessary, establishing a software allow list that only executes legitimate applications.
- Monitor network ports, protocols, and services, and activate security configurations on network infrastructure devices like firewalls and routers.
- Regularly patch and update software and applications to their latest versions, and perform vulnerability assessments periodically.
These recommendations aim to reduce the likelihood and impact of Clop ransomware and other ransomware incidents. It is important for organizations to stay vigilant, implement these measures, and stay updated on the latest advisories and resources provided by the #StopRansomware effort.
The advisory also provides technical details about Clop ransomware and the tactics used by TA505. It describes the history and evolution of Clop as a Ransomware as a Service (RaaS) and highlights TA505’s involvement in phishing, malspam, and financial fraud activities. Specific malware types associated with Clop, such as FlawedAmmyy, SDBot, Truebot, Cobalt Strike, DEWMODE, and LEMURLOOT, are discussed.
CVE
Furthermore, the advisory outlines the exploitation of vulnerabilities in software solutions like MOVEit Transfer, providing details about the CVE-2023-34362 SQL injection vulnerability and the web shell named LEMURLOOT used by TA505. The affected versions of MOVEit Transfer software and the recommended actions, including software upgrades and patching, are also mentioned.
Given the rapid and successful exploitation of vulnerabilities by TA505, organizations are warned about the widespread exploitation of unpatched software services in both private and public networks. The advisory includes a table of indicators of compromise (IOCs) related to the MOVEit campaign for reference.
It is recommended to refer to the original advisory and associated files for complete information and technical details on CL0P ransomware and the TA505 threat actor.
Practical defence
In order to protect yourself, here is a YARA rule which will offer you some protection through detection. Other rules are available below.
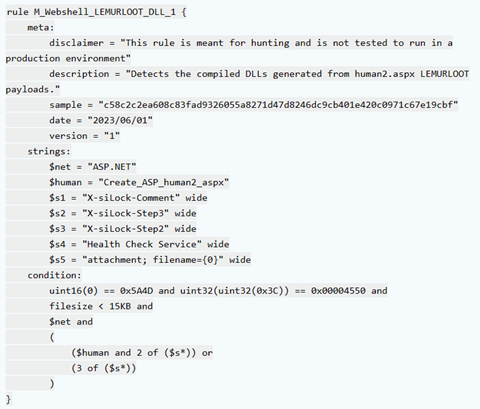
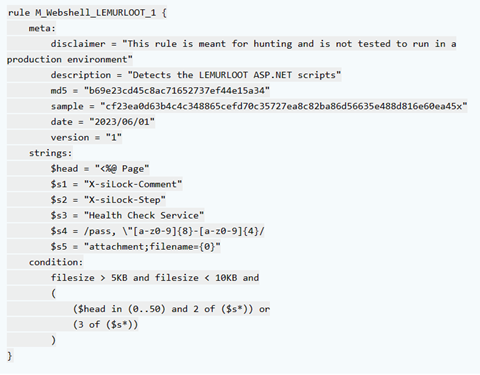
For a full investigation of the indicators of compromise, known malicious emails, and other useful information, check out the CISA website.








