Post Credit: Austin Miller
Cybersec Fundamentals: “Why should I care about password strength?”
Credential stuffing is on the rise and the effects of these attacks are costing businesses $6 million a year. Brute force attacks are becoming quicker than ever thanks to next gen GPUs. The adversary’s tried and tested methodology is only getting better – for network administrators and security professionals, these numbers should be alarming. Our only defense – an understanding of cybersec fundamentals.
How can we defend out systems against the threats that come from people not understanding the importance of strong passwords? In the wake of the most reason set of research carried out by Hivesystems, there’s an easy infographic which might help you teach a valuable lesson when the time comes to educate the non-cybersecurity employees. It is vital that all employees understand cybersec fundamentals.
HiveSystem’s Password Matrix
One of the vital cybersec fundamentals is a password. We know that strong passwords are important. Gathering tools to crack weak passwords really isn’t that difficult – anyone can access Jack the Ripper to try their hand at breaking down password-guarded defenses. But the average end-user doesn’t see it that way.
The time comes around for staff to refresh passwords and you might have heard some of these comments:
- I just change one number at the end of my password every time.
- I try to get around the “too similar to a previous password” thing by changing it until the system forgets.
- I can never remember what my password is – why can’t you just let me have the one I can remember!
- Why do I have to use “special characters”? It’s only a password!
The next time that employee education comes around, show them this matrix:
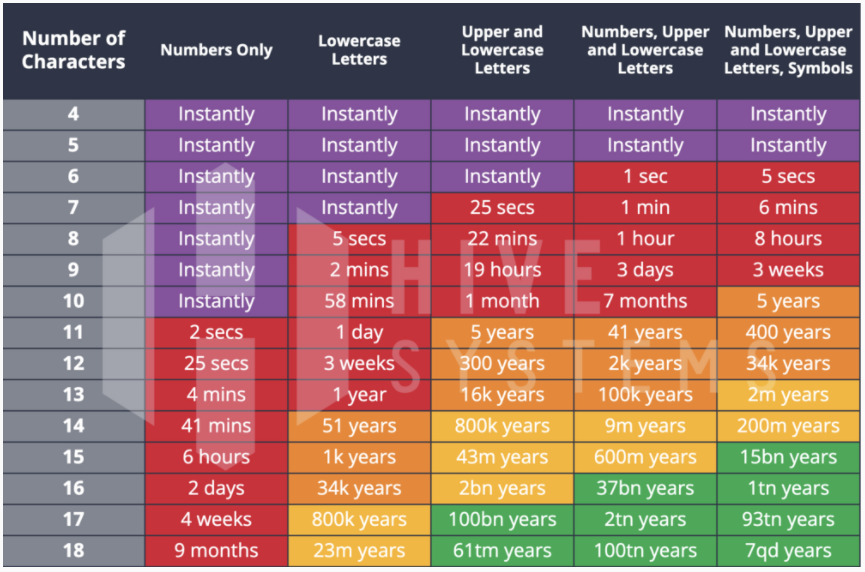
All passwords tested by Hivesystems were MD5 hashed passwords.
Understanding the password matrix
As we can see from Hivesystems’ research, simple passwords aren’t even a minor concern for would be adversaries. For the employee that uses <Un1ted> (one capital letter, one number), it will take the adversary all of one (1) second to gain access to the account. Because a fan of the red team in Manchester only put in the bare minimum to reset their password, the adversary has an easy way in.
As we move to the bottom-right of the matrix, you will see that passwords start to enter the green zone – this is where a password is so uncrackable that you can almost stop worrying about the risk of a pure brute force attack. Where you set your threshold for password strength is really up to you – would the 7 months that 10 characters, numbers, upper and lowercase deliver be enough for you? Or do you want to convert your team to password managers and insist on 18+ characters including numbers, upper and lowercase letters as well as special characters/symbols? That depends on your organization’s needs and willingness to adopt new software.
Can I stop worrying about brute force attacks now?
Although it would be nice to say yes, the adversary who uses brute force attacks isn’t going away anytime soon. The above tests were run with a RTX 2080 GPU – let’s see what happens when we upgrade to an RTX 3090 GPU:
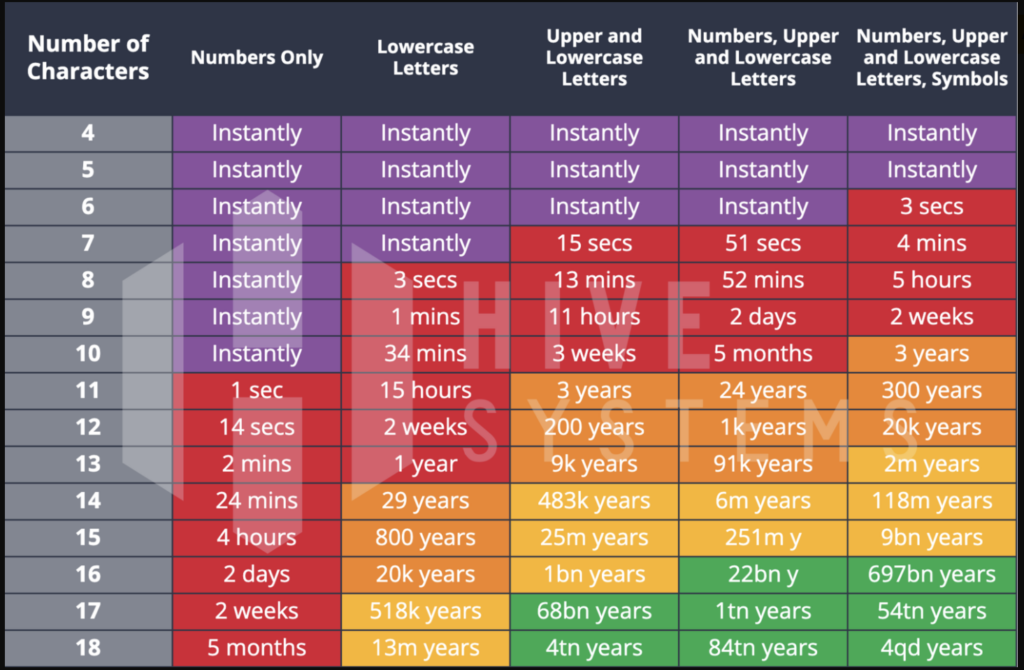
Although the password manager using, 16+ character password creator is still going to be fine, there are changes. As the adversary accesses better hardware and tools, these numbers will only go down. Staying on top of password health is not only a blue team activity – you also need to think like a red teamer.
My team all have 25-character passwords with numbers, uppercase, lowercase, and symbols – are we safe?
Due to the popularity of data aggregation sites such as Have I Been Pwned? (and the black-market equivalents), the adversary has a wealth of password information at their fingertips. If there is a data breach somewhere, you can bet that there is a threat actor who is excitedly trying to use the leaked credentials to access sensitive data.
Somewhat amusingly, here is the Hivesystems’ strength matrix for passwords that are on popular rainbow tables, prone to dictionary attacks, or are otherwise compromised at a hash level.
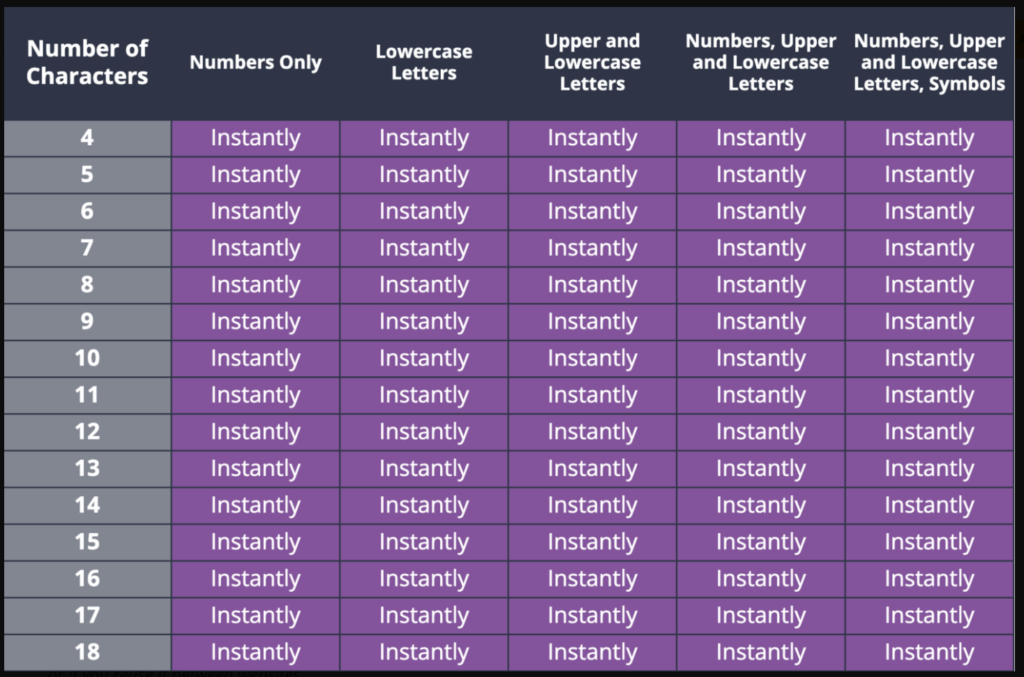
No password is going to be safe forever. This is especially true for people who don’t realize that their data has been leaked into the dark underbelly of the internet. Healthy password practices that you can implement in your organization on the back of these findings include:
- Password selection should be monitored in relation to threat intelligence, preferably through an extensive blacklist of compromised passwords.
- Password managers – both premium and free – are necessary tools for implementing the most secure passwords.
- All passwords of ten or more characters enter the zone of “practically uncrackable” when uppercase/lowercase, numbers, and symbols are used
- Refreshing passwords frequently will stop the adversary running long-term brute force attacks
As always, the weakest part of any cybersecurity system is the human part. Hopefully you now have enough information to encourage robust password policies and convince your end-users of the importance of listening to the cybersecurity team.
The SecPro is a weekly security newsletter to help you stay sharp and upgrade your skills with trending threat insights, practical tutorials, hands-on labs, and useful resources. Build skills in as little as 10 minutes. Join the newsletter here.








