Post Credit: Ricoh Danielson
Before we dive deep into the approach of conducting digital forensic triage in an active incident, let’s get to know the importance of DFIR and how it is used to identify, remediate, and analyze cybersecurity incidents.
Understanding the importance of DFIR
While investigating an incident, it is essential to understand the significance of Digital Forensics and Incident Response (DFIR).
Executing Digital Forensics Triage during an Incident Response is focused on speed. It is about how we get ahead of the threat actor and understand their Tactics, Techniques, and Procedures (TTPs) to gain utmost control over the incident. This is crucial because, at some point, Law Enforcement, Regulators, and other stakeholders will start inquiring about their attack vectors.
Conducting digital forensic triage will enable us to answer their inquiries not only from a “controlling the narrative” perspective but also from a legal perspective. The more data and metadata/indicators of compromise (IOCs) that are found, the more the cyber community will request the details of the compromised systems.
Especially for cybersecurity leaders, understanding DFIR from a high level along with its technical aspects would help solve any problem. If a leader can understand the technical details of DFIR then they can make better technology and business decisions.
Technical Requirements to conduct Digital Forensic Triage
There are certain things that need to be considered when it comes to understanding the requirements of a Digital Forensics Triage expedition during an Incident Response.
Location, location, location – just like real estate, the same applies to incidents. Having the right place for your environment and ensuring its effectiveness is vital. It is highly suggested that the environment be set up before engaging in an incident.
For this, you will need a location in an environment with remote central access for multiple reasons. If the incident is extraordinarily complex and affects many devices, then there will be a demand for a possible cloud environment so that other staff can work around the clock to get a better idea of what the threat actor has done and what they are going to do next.
Setting up a cloud environment with 5TB of storage, 64 gigs of ram, and a high processor to ensure data can process the data fast along with storing evidence that pertains to the matter at hand. Not all incidents are created equal, so different tools may be required. Tools such as conducting imaging, extracting RAM data, analyzing logs and grep metadata to extract data points that can help lead the closure to the investigation.
Why are we choosing Velociraptor?
Velociraptor aka VELO is a great tool to gain visibility when other tools cannot perform this and if there are no tools readily available. VELO can be deployed on live hosts and can obtain certain data needed to view the signature traits of the threat actors. VELO is commonly used during the integration process of the device. If certain hosts have a discovered IOC on it, then VELO can provide metadata points to empower the incident responder to gain more ground ahead of the threat actor.
Something to consider
When attempting to use Velociraptor, deploying it across an environment that a threat actor is currently active can be tricky. During an incident, there might be certain processes or applications that might be disabled to prevent the threat actor, so there will need to be a custom Velociraptor developed.
This is how you do it.
Implementing VELO to observe and conduct Digital Forensic Triage
Step 1:
Let’s find an application such as https://docs.velociraptor.app/
Step 2:
We will need to create an EXE to be deployed across the environment.
We begin by pulling down the installed package. We may need to develop a custom EXE package.
Step 3:
Monitoring will empower the forensic person to control the effort.
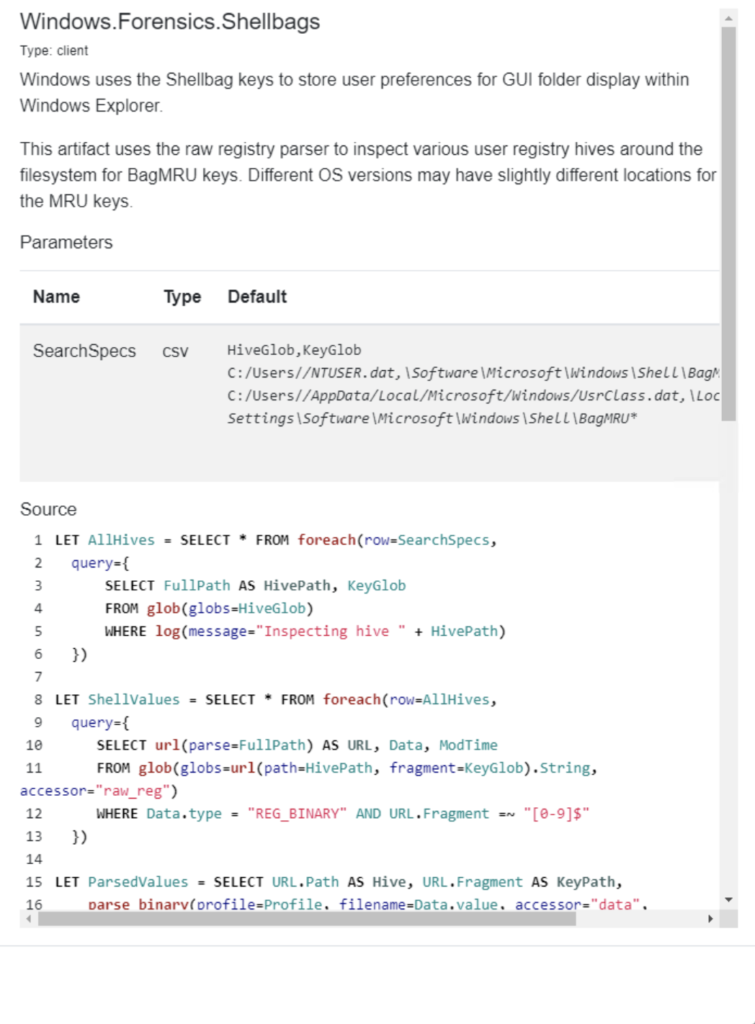
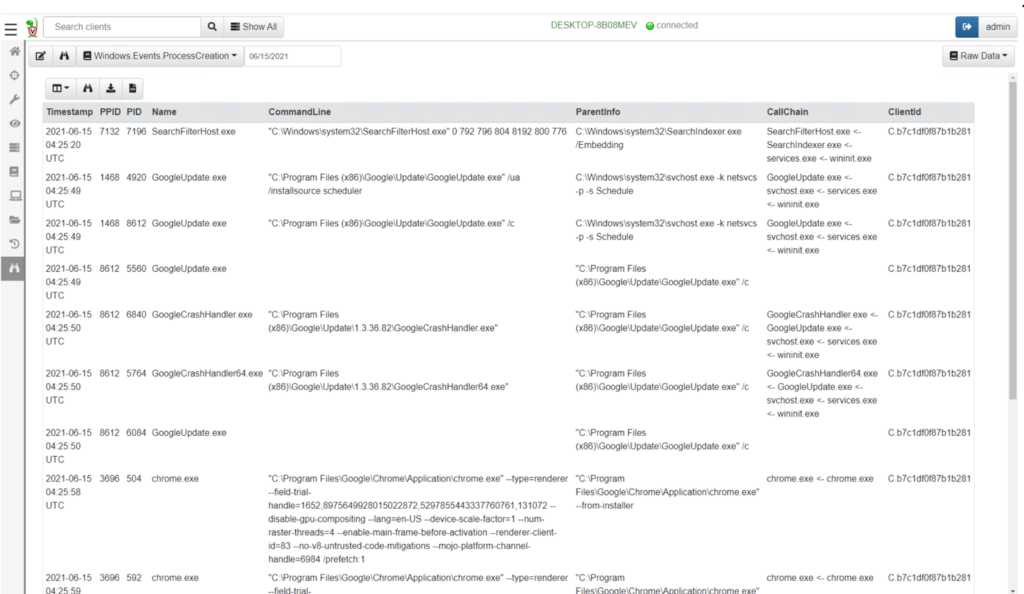
Steps for Accessing Velociraptor via Cloud
The best way to gain access to VELO in the cloud is to develop a cloud-based dashboard. Once VELO is installed and configured in your cloud environment and the agent deployed are calling back to the arranged servers that are allowing reporting back, then by accessing the dashboard the incident responders can gather more data to take more aggressive action. It is important to note that having a centralized location for research will be more helpful.
Analyzing an active incident for digital evidence through Digital Forensics Triage
Analysis during an active incident is an ongoing battle. Some days there is tons of data and some days there is no data to go from. This is where triaging the data that has been obtained during an incident is particularly important.
Taking it a step further and finding out the approach of the threat actor will yield what their approach is where they might be heading and with what tools. The evidence-gathering phase is something that is going to be discoverable and shareable from a legal perspective.
Summary
Conducting Digital Forensic during an Incident Response empowers the incident responder to get control of a cyber incident and helps in mitigating the threat actor. This can only be achieved if the incident responder has the correct environment, tool, technology, and support from their leadership and business.
Using tools such as VELO provide an application of use to gain a high amount of visibility during a cyber incident. VELO, if configured and deployed correctly, can yield a high amount of data to analyze and show how, when, and where the threat actor might be heading.








