Modern problems require modern solutions. Present-day websites are very different from the websites a few years ago. Consider any website whether it is static or dynamic the way they operate, store, and process content to users has increased to a large extent. Due to more dynamic content distributed, backend infrastructure especially CDN becomes more complex and vulnerable. This is will be the main attack service for the hackers.
Content discovery is not a new method to gain information about a website. There are many tools in the market used for content discovery but unfortunately, they have a limited capacity. With the complications, tools are not being updated to scan in depth. But there are some tools which can solve this problem. The kite runner is one among them.
As per Kiterunner’s Github, it states that “ Kite runner is a tool that is capable of performing discovery in traditional routes and also able to brute force endpoints ( API).
Modern application frameworks such as Flask, Rails, Express, Django, and others follow the paradigm of explicitly defining routes that expect certain HTTP methods, headers, parameters, and values.
By collating a dataset of Swagger specifications and condensing it into our own schema, Kiterunner can use this dataset to Bruteforce API endpoints by sending the correct HTTP method, headers, path, parameters, and values for each request it sends.”
How to install Kite Runner
You can download a pre-built copy from https://github.com/assetnote/kiterunner/releases or you can clone the Git Repo and build from the source.
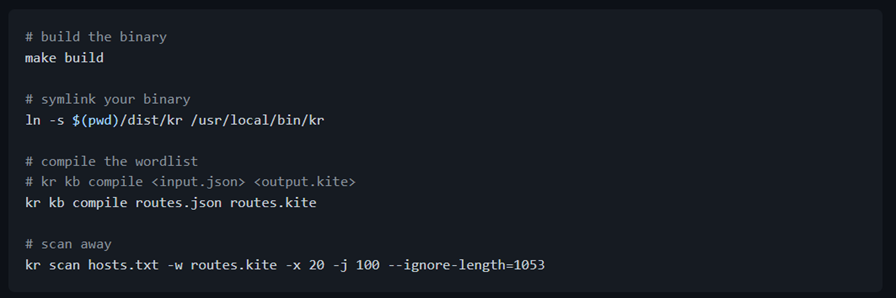
Usage of Kite-Runner
The kite runner has extensive and multiple options to scan domains and API endpoints with help of wordlists.
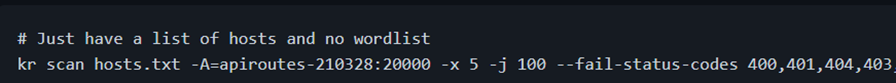
Any command in the kite runner starts with “kr”. Here we have a list of hosts “hosts.txt” using which we will scan the list of hosts and we don’t need any separate wordlists. Kite runner maintains a large database of world lists. Let’s break down this command.
-A is for selecting the wordlist along with the number of words with :
-x: Max connections to a single host – 5
-j: Max number of parallel hosts it can scan – 100
–fail-status – selecting the error codes and filtering out based on the status code
API Scanning using Kite runner
As we discussed, this tool has the capability to scan the API endpoints, it can scan single targets, multiple targets, and scan a list of targets at once.
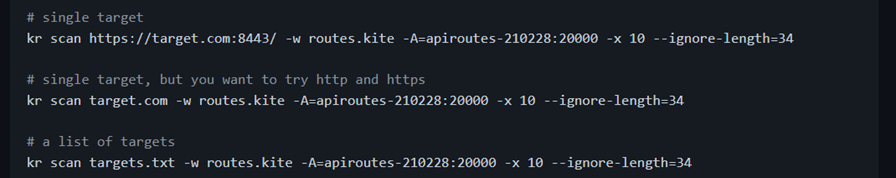
Usage of API scan is similar to domain scan.
Scan refers to the endpoint which we need to scan.
-w refers to the kite wordlist format
-A refers to a wordlist
-x refer to no of redirect
–ignore-length – ignore the length of the byte
We can select one single endpoint, whole domain, and list of domains.
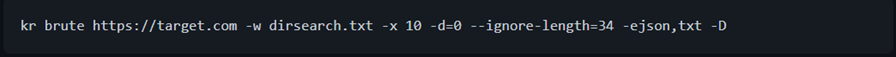
Dirsearch Bruteforcing
Many are familiar with tools like dirsearch and have default wordlist. Dirsearch is a tool used for directory search. Kiterunner is compatible to do brute force with dirsearch default wordlists also.
Kiterunner Working
Kiterunner can be used for both brute-forcing and scanning endpoints. With the flag available this tool can scan for depth, subdomains, and length of the endpoints, and API targets are scanned in multiple depth levels. Kiterunner will take both http and https into consideration. It gives priority to https and then go to ports for scanning but if we dont provide http or https, it will take both http and https or both 80 and 443
If you consider below URL’s
/api/v1/user/delete
/secrets/v1/
- At depth 0, only / would have the baseline checks performed for wildcard detection
- At depth 1, /API and /secrets would have baseline checks performed, and these checks would be used against /API and /secrets correspondingly
- At depth 2, /api/v1, /api/v2, /secrets/v1 and /secrets/v2 would all have baseline checks performed.
API Signatures in Kiterunner
Kiterunner database is regularly updated with different frameworks used to build API. These databases consist of the formats with parameters, and additional docs which can be utilized for API endpoint scanning.
This is one example. It covers from flask to spark and many more.
Another best feature of Kiterunner is to replay requests from the flow of scans.
When we export output from kiterunner, it will be difficult to immediately understand why a request is given a specific response code/length. Kiterunner offers a method of rebuilding the request from the wordlists used including all the header and body parameters.
- We can replay a request by copy-pasting the full response output into the kb replay command.
- You can specify a –proxy to forward your requests through, so you can modify/repeat/intercept the request using 3rd party tools if you wish
- The golang net/HTTP client will perform a few additional changes to your request due to how the default golang spec implementation (unfortunately).
Report Output
Kiterunner uses a kite file format for storing the JSON schemas from kitebuilder. These are simply protobuf encoded pkg/proute.APIS were written to a file. The compilation is used to allow us to quickly deserialize the already parsed wordlist. This file format is not stable, and should only be interacted with using the inbuilt conversion tools for kiterunner.








