Written By: Andy Pantelli
Okta breach – Writing was on the Wall, a view of the Genesis Market Place
The Okta breach, without doubt, is InfoSec World’s number one breach of 2022. At least, for now. Although brilliant in terms of publicity that the breach generated for the Hackers, it wasn’t rocket science. Not even a master criminal or two at work to pull it off. Audacious of course, hacking one of the foremost Identity & Access Management Providers takes some nerve, if not ‘brass neck’.
Today I’m not going to focus on the actual attack or the various stages of it, but if you haven’t read the Intrusion Timeline here’s a quick summary; upon initial compromise, the attackers (literally) used a search engine to find a Privilege escalation tool then quickly followed by another Bing Search to find a Process Explorer tool. Process Hacker duly downloaded from GitHub and it was seemingly quite easy enough to stop the XDR agent from finally downloading Mimikatz used to escalate privileges. Off the shelf tools, Bing & GitHub – breach did.
As I said, Okta isn’t the real focus and not the moral of this story. What we know is that the group previously took the credit in a blaze of glory for breaching EA Games security and allegedly gaining access to game source code and other related internal tools. Some of the code for FIFA 2021, Battlefield and tools for the Frostbite Engine. In all 780Gb of data was claimed to have been compromised with the sale of EA Proprietary Frameworks, SDKs. All of which were then advertised for sale in various hacking forum posts.
It seems though that the group responsible not only revealed their ‘magicians’ trick’ how they did it regarding the EA breach but also stated as long ago as June 2021 that Okta was in their sights. A ‘representative’ of the hackers claimed to have purchased a digital fingerprint from the online Marketplace ‘Genesis’ for as little as $10 which gave them access to a Slack account which then let them social engineer EA IT support granting access to the internal network. Sounds far-fetched? It gets better. The hacker rep explained how it was possible to filter a search on the marketplace Genesis by URL allowing ‘hackers’ to search for Slack or Okta, for example, they said. So, in an article published online some 9 months earlier someone apparently speaking on behalf of Lapsus$ had explained how they breached EA, and if they wanted to could use the same dark web marketplace to try and breach Okta. That place? Genesis.
GENESIS – the marketplace for Cybercriminals
It’s the one-stop shop for Dark Web Market Place, enabling cybercriminals to make millions stealing online identities. Is Genesis elusive? Maybe. Hidden away? Not so much. Genesis hides in plain sight. I won’t link to it but finding it is not rocket science. It is exclusive though, access to the site content is by invitation code only. Basically, to get access to the market place a ‘trusted’ user needs to generate an access code for you. Unless, of course, you’re fairly competent at finding whatever you want online and hey presto, you got yourself an access code. Once you’re in though, it even has a Support ticketing system and FAQ. I kid you not.
The site is pretty slick, giving a professional user experience of the kind you would expect from any major eCommerce site. Genesis is not just a place where usernames & passwords are traded though. With increasing security countermeasures unique device ’fingerprints’ are being traded instead.
Containing a combination of IP address, browser cookies, user-agent string, username, password & OS details many anti-fraud solutions consider a device fingerprint to be a truly unique identifier.
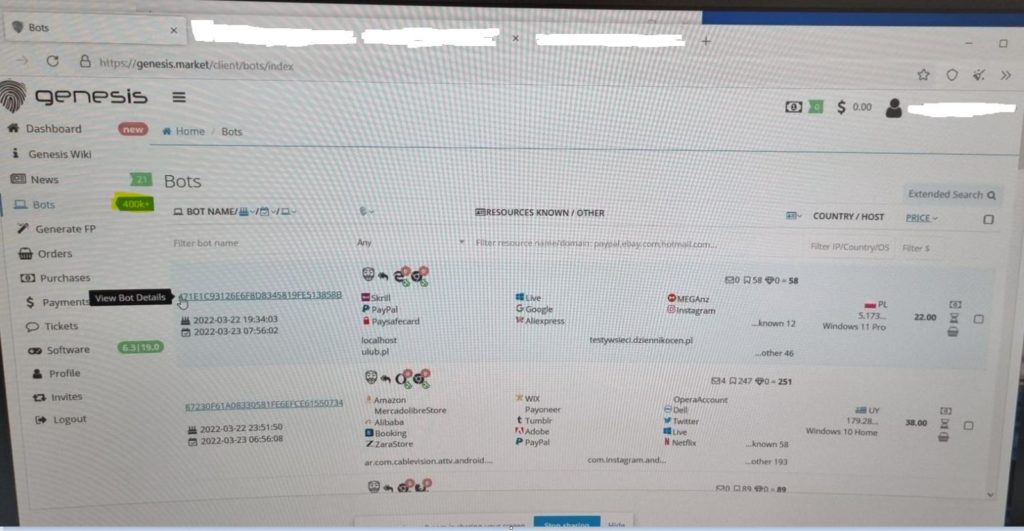
Enter Genesis. Victims are targeted with Malware which infiltrates devices gathering login credentials…and the all too critical device fingerprint. These are then advertised on the Genesis platform for sale from as little as $0.70 to around $350 per ’bot’, with a bot representing the compromised digital fingerprint.
After purchase, our little kiddie hacker gets access to a custom browser and can browse the web masquerading as the victim, use the stolen logins and access online accounts where cookies exist making is seem like the original device was making the transaction. When Genesis first became noticed, in the region of 100k compromised digital fingerprints were being traded. When the site was accessed in the image below over 400k compromised ’bots were available for purchase. Also shown in the image is the cost of this bot and some of the sites that would be accessible upon purchase. Also can be seen is the geographic region of the compromised bot. Interestingly enough, no compromised ’bots’ were seen from Russia. Make of that what you will.
Genesis trades in Crypto, Bitcoin transactions accounted for $250 in 2012 but increasing to $1Bn during 2019, it’s not hard to see the demand with ’Marketplaces’ such as Genesis. Of course, it’s not exactly new, Silk Road generated over $9Bn before being closed down. It seems though, that Genesis isn’t going anywhere, it’s online presence has been seen for around 3 years so taking it down doesn’t seem to be an easy thing to do, although the site did disappear for a short time before remerging.
It’s easy to get accustomed to online fraud, it’s there. We accept the risks when making online purchases, or using online banking, social media, email to communicate & just about every other thing we make use of online. During the Pandemic it is reported that 1.5 billion credentials were compromised with Juniper research estimating online fraud will cost 48Bn by 2023. The thing with Genesis, when you actually see how easy it easy, when you see how much of your life could be traded so easily, it’s a very sobering thought. It’s so easy & open in fact, that the writing is on the wall what they do, and how they do it. Just ask Okta.








