After web and mobile security, API security is also becoming widely popular and it is important to know how to conduct proper API penetration testing. A few weeks back OWASP released its must-awaited OWASP API Security Top 10 2023 which talks about all the top API flaws that are being exploited and which one needs to learn. Today in this article we will dig deep into what is API, what is OWASP API Security Top 10 2023, how to get started, and know more about different resources which we can use to master the skill.
What is API?
An API, which stands for application programming interface, serves as a means for diverse software applications to establish communication with each other.
The influence of APIs is pervasive, as they facilitate the seamless interaction between our beloved apps, websites, and devices.
Countless contemporary web applications heavily rely on APIs. For instance, when you place an order for a product on Amazon, the company utilizes an API to connect with your bank and carry out the payment processing. Similarly, when you check the weather on your phone, an API is employed to retrieve data from a weather service.
In essence, APIs play a pivotal role in driving the wheels of the modern world!
Why API Security is Important?
As more and more modern applications started relying on APIs for establishing communications among each other, the number of API-based attacks too has gone up to a large number.
The State of API Q1 2023 report, released by the Salt Labs research team in March 2023, revealed a staggering surge of 400% in unique API attackers targeting Salt customers within a mere six-month period. However, it’s not just the quantity of API attacks that have increased; their characteristics have also transformed.
According to the Securing the API Attack Surface Report by Palo Alto networks :
- 41% of orgs say security lacks visibility and control in development processes.
- 28% say the lack of visibility and control persists into the deployment of APIs.
- 40% of organizations report that new builds are deployed to production with misconfigurations, vulnerabilities, and other security issues.
- Only 25% report accurately inventorying APIs used by their organization.
- 88% of organizations are troubled by problems with the authentication of APIs.
- 94% of organizations say the most important API security feature is the ability to identify APIs with sensitive data.
So by far, I hope you must have understood why API security is important and why it is booming. Engaging in web API security testing can prove to be highly profitable, particularly for individuals involved in bug bounty programs. These programs often provide clear guidelines regarding the scope of their web application programming interfaces, presenting an excellent opportunity for conducting penetration tests on APIs.
An adept security researcher can also offer penetration testing services targeting prevalent API vulnerabilities, thereby assisting clients in evaluating the security of their web APIs. Whether it’s an internal or public API, employing a systematic and consistent approach to breaking web application programming enables the exploration of common attack vectors.
It is astonishing how easily one can discover lucrative API bugs by adhering to a straightforward methodology for breaking web application programming interfaces.
OWASP API Security Top 10 2023
A few weeks back OWASP released their much-awaited list of top 10 API flaws, offering a fresh take on application-program-interface (API) security weaknesses and risks that most often lead to specific vulnerabilities.
Among the risk categories, six have predominantly or partially retained their placement from the inaugural 2019 OWASP API Security Top 10 list. Two previous categories have been amalgamated, while two others have been assimilated into broader new categories. Additionally, a brand-new category dedicated exclusively to server-side request forgery (SSRF) has been introduced.
Here is a brief detail of the new OWASP API Security Top 10 2023 :
- Broken Object Level Authorization
Attackers can exploit vulnerable API endpoints with broken object-level authorization by manipulating the object ID in the request. Object IDs can be easily identified in the request parameters, headers, or payload. This is a common issue in API-based applications, where the server relies on client-provided object IDs to determine access without fully tracking the client’s state. Unauthorized access to objects can lead to data disclosure, loss, manipulation, or even complete account takeover.
- Broken Authentication
Authentication mechanisms are vulnerable to attackers as they are accessible to everyone. Even though exploiting certain authentication issues may require advanced technical skills, exploitation tools are readily available. Common misconceptions among software and security engineers regarding authentication boundaries and implementation complexity contribute to the prevalence of authentication issues. Detecting broken authentication methodologies is readily available and easy to develop.
Exploiting these issues allows attackers to gain full control over other users’ accounts, access personal data, and perform sensitive actions on their behalf. Distinguishing attackers’ actions from legitimate user actions is often challenging for systems.
- Broken Object Property Level Authorization
APIs often expose endpoints that return all properties of an object, especially in REST APIs. For protocols like GraphQL, it may require specific requests to specify the desired properties. While identifying and manipulating these additional properties may require some effort, there are automated tools available to assist in this process. By inspecting API responses, sensitive information can be identified within the object representations. Fuzzing techniques are commonly used to discover hidden properties that can be potentially modified by crafting API requests and analyzing the responses.
In cases where the target property is not returned in the API response, side-effect analysis may be necessary. Unauthorized access to private or sensitive object properties can lead to data disclosure, loss, corruption, and even privilege escalation or account takeover under certain circumstances.
- Unrestricted Resource Consumption
The exploitation of APIs can be done with simple requests, including concurrent requests from a single computer or utilizing cloud computing resources. Automated tools often focus on causing denial-of-service (DoS) by overwhelming the API with high traffic loads, impacting its service rate. Many APIs lack client interaction or resource consumption limits, making it possible to identify vulnerabilities by crafting requests that control the number of returned resources and analyzing response status, time, or length.
Batched operations can also be exploited. Although threat agents may not have visibility into cost impact, it can be inferred based on the business/pricing model of service providers (e.g., cloud providers). Exploitation can result in DoS due to resource starvation and increased operational costs, such as higher CPU demand and increased cloud storage needs.
- Broken Function Level Authorization
Exploiting APIs involves sending legitimate API calls to unauthorized endpoints, typically accessible to anonymous or non-privileged users. Exposed endpoints are vulnerable to exploitation. Implementing proper authorization checks can be challenging due to the complexity of roles, groups, and user hierarchies in modern applications.
APIs are often easier to assess for these vulnerabilities due to their structured nature and predictable access to different functions. These flaws enable attackers to access unauthorized functionality, with administrative functions being particularly targeted. This type of attack can result in data disclosure, loss, corruption, and ultimately disrupt services.
- Unrestricted Access to Sensitive Business Flows
Exploitation typically involves comprehending the underlying business model supported by the API, identifying critical business processes, and automating access to these processes, resulting in harm to the business. The prevalence of this issue is often attributed to the lack of a comprehensive understanding of the API’s role in fulfilling business requirements. Attackers manually analyze the target workflow, determining the involved resources (e.g., endpoints) and their interactions.
If mitigation measures are already in place, attackers need to discover ways to bypass them. While the technical impact is generally minimal, exploitation can harm the business in various ways, such as preventing legitimate users from making purchases or causing inflation within the internal economy of a game.
- Server-Side Request Forgery
Exploiting an API endpoint that accesses a client-provided URI is the goal for attackers. Basic server-side request forgery (SSRF) attacks, where the attacker receives a response, are easier to exploit compared to blind SSRF attacks where there is no feedback.
Improper validation of client-provided URIs is a common issue in modern application development. Detecting the vulnerability requires regular analysis of API requests and responses. However, in blind SSRF cases, detecting the vulnerability requires more effort and creativity.
Successful exploitation can lead to the enumeration of internal services, information disclosure, firewall bypass, DoS attacks, or the server being abused as a proxy for malicious activities.
- Security Misconfiguration
Attackers actively search for unpatched flaws, common endpoints, insecure default configurations, and unprotected files or directories to gain unauthorized access or system knowledge. Exploits for these vulnerabilities are often publicly available. Security misconfigurations can occur at any level of the API stack, from the network to the application.
Automated tools exist to detect and exploit misconfigurations, including unnecessary services or legacy options. These misconfigurations not only expose sensitive user data but also reveal system details that can result in a complete server compromise.
- Improper Inventory Management
Threat actors gain unauthorized access through unpatched and outdated API versions or endpoints with weaker security. They may also exploit third-party access to sensitive data. Outdated documentation complicates vulnerability discovery and resolution. Failure to maintain asset inventory and retirement strategies results in data leaks from unpatched systems. Unnecessarily exposed API hosts are common due to modern concepts like microservices.
Simple techniques like Google Dorking and DNS enumeration can help identify vulnerable targets. Attackers can gain access to sensitive data or take control of servers. Exploiting deprecated endpoints in old API versions allows access to administrative functions and known vulnerabilities.
- Unsafe Consumption of APIs
Exploiting this issue involves attackers identifying and potentially compromising other APIs/services integrated with the target API. This information is typically not publicly available or easily exploitable. Developers often trust external or third-party APIs without thorough verification of security requirements such as transport security, authentication/authorization, and input validation.
Attackers must identify and compromise the services integrated with the target API. The impact depends on how the target API handles the obtained data. Successful exploitation can result in unauthorized access to sensitive information, various types of injections, or denial of service attacks.
Tools used for API Pentesting
- Burp Suite: Burp Suite is a widely used tool for API pentesting. Its proxy allows intercepting and modifying API requests, while the scanner identifies vulnerabilities. Burp Suite is versatile, enabling manual testing and automated scanning to discover security flaws in APIs.
- Postman: Postman is a popular API development and testing tool that can also be utilized for API pentesting. It simplifies sending custom requests, analyzing responses, and automating tests. With its user-friendly interface and features like request chaining and assertions, Postman streamlines API security testing.
- OWASP ZAP: OWASP ZAP is an open-source tool with API pentesting capabilities. It intercepts and modifies API requests, performs active and passive scanning, and generates detailed reports. ZAP’s scripting support and community-contributed add-ons make it a valuable tool for API security testing.
- Insomnia: Insomnia is a powerful API testing and debugging tool, suitable for pentesting. It facilitates sending requests, inspecting responses, and managing API environments. With its support for various authentication methods, Insomnia aids in testing the security of APIs.
- SoapUI: SoapUI is a widely used tool for testing SOAP and REST APIs. It allows creating test cases, simulating requests, and analyzing responses. With its authentication support and scripting capabilities, SoapUI is beneficial for API pentesting, particularly for SOAP-based APIs.
Building an API Pentesting Lab
Once you have tools like Burp Suite and Postman you can get started with API Pentesting. A combination of Burp Suite and Postman is enough to do most of the API Pentest.
To learn more about API pentest you need to start practicing in your lab. Here are the top 2 API labs which you can use to practice.
- OWASP crAPI: Completely ridiculous API (crAPI) will help you to understand the ten most critical API security risks. crAPI is vulnerable by design, but you’ll be able to safely run it to educate/train yourself.
- OWASP Juice Shop: OWASP Juice Shop is one of the most modern and sophisticated insecure web applications! It can be used in security training, awareness demos, CTFs, and as a guinea pig for security tools! Juice Shop encompasses vulnerabilities from the entire OWASP Top Ten along with many other security flaws found in real-world applications!
Installing OWASP crAPI
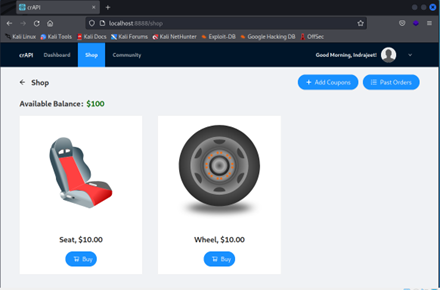
You’ll need to have Docker and docker-compose installed and running on your host system. Also, the version of docker-compose should be 1.27.0 or above. Check your docker-compose version using:
docker-compose version
Using prebuilt images
To use the latest stable version.
Linux Machine
- curl -o docker-compose.yml https://raw.githubusercontent.com/OWASP/crAPI/main/deploy/docker/docker-compose.yml
2. docker-compose pull
3. docker-compose -f docker-compose.yml –compatibility up -d
Windows Machine
- curl.exe -o docker-compose.yml https://raw.githubusercontent.com/OWASP/crAPI/main/deploy/docker/docker-compose.yml
- docker-compose pull
- docker-compose -f docker-compose.yml –compatibility up -d
Once the above is done, Visit http://localhost:8888
Installing OWASP Juice Shop
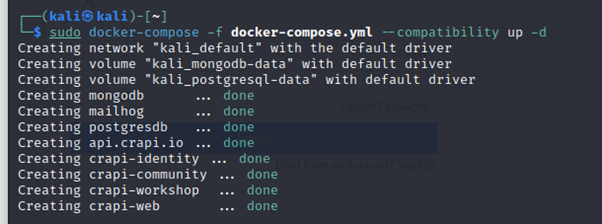
To install OWASP Juice Shop you need to do the following :
From Sources
- Install node.js
- Run git clone https://github.com/juice-shop/juice-shop.git –depth 1 (or clone your own fork of the repository)
- Go into the cloned folder with cd juice-shop
- Run npm install (only has to be done before the first start or when you change the source code)
- Run npm start
Browse to http://localhost:3000
Docker Container
- Install Docker
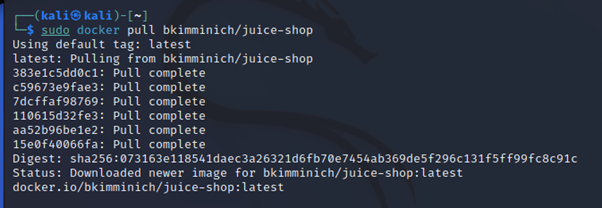
- Run docker pull bkimminich/juice-shop
3. Run docker run –rm -p 3000:3000 bkimminich/juice-shop
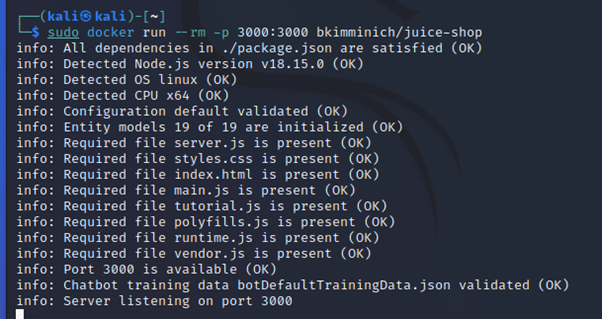
Browse to http://localhost:3000 (on macOS and Windows browse to http://192.168.99.100:3000 if you are using docker-machine instead of the native docker installation)
API Pentesting Mindmap
Once you are done setting up your pentesting Lab you can start experimenting with different security flaws that you know. You can take help from the OWASP top 10 for API. Here is a mindmap that you can follow which can help you find flaws better.
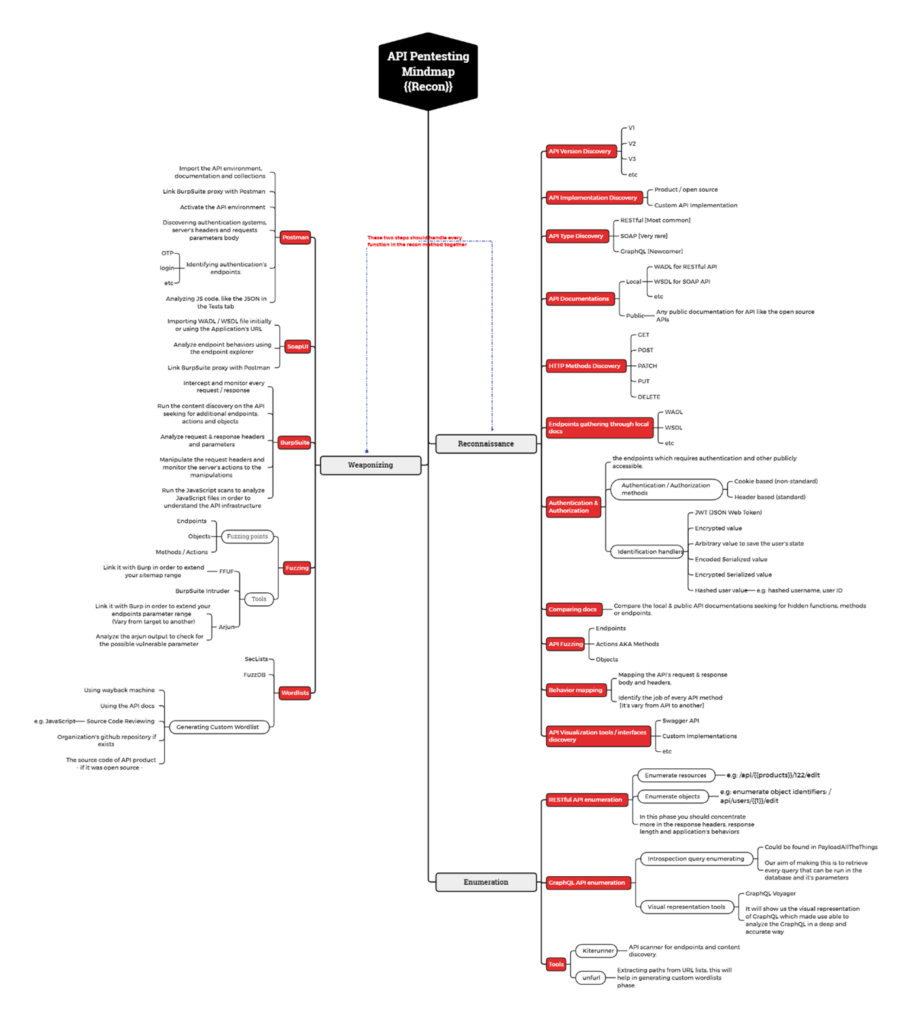
You can download the mindmap from here: https://github.com/Cyber-Guy1/API-SecurityEmpire/blob/main/assets/API%20Pentesting%20Mindmap.pdf








