By Sai Adithya Thatipalli
API – a term we hear on a regular basis when it comes to web applications. These have made the applications less complex and more useful with the ease of development of APIs for different use cases. All modern mobile applications are built with API and microservices which allows them to integrate multiple services – lightweight applications at your fingertips! API usage also extends to cloud applications and APIs can play a major role in securing the applications. But before deep diving into API security, we need to understand API architecture and how Cloud adapted the API technology to provide services.
API Architecture consists of the client, gateway and server. When a user interacts with an application, the API will request the web server to provide the information. The API acts like a messenger between client and the web servers, but it can also communicate to multiple applications with right authentication and right authorization. This makes it to load balance the request, route to specific API gateway to fetch the information.
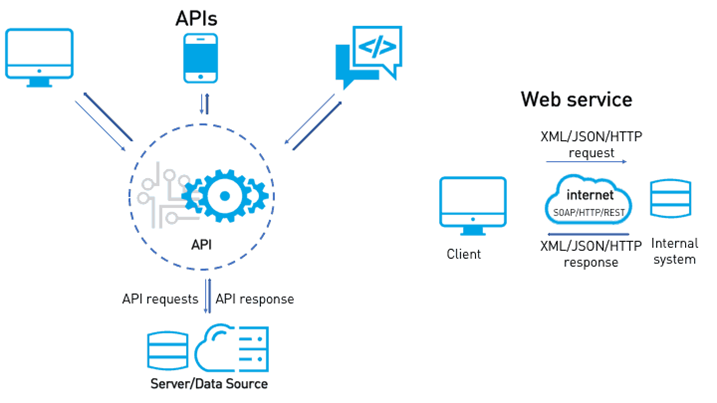
How Cloud Technology Adapted to API technology
The Cloud technology comes with microservice architecture and APIs as part of it.
In simple words, majority of the cloud bases SaaS applications are hosted in cloud and provide services to users. Since there are hosted in cloud and many of applications are interconnected to one way or the other in terms of authentication, authorization or service based, several applications shifting to microservices architecture and adding API capabilities so that they can provide more services under one umbrella.
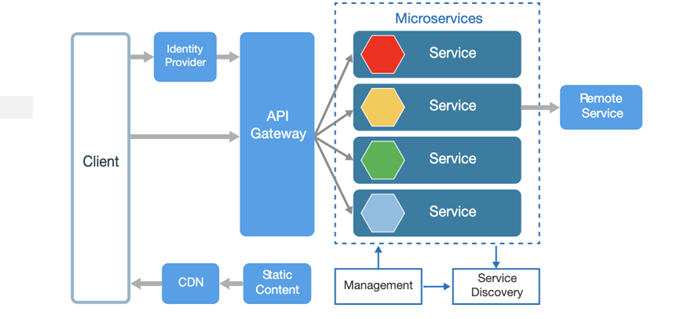
Example:
Let’s assume that you are trying to buy some fashion items from an e-commerce site, you login using yourGgoogle ID, you select the products from different sellers, add it in your cart, select the payment provider like Amazon, Paypal, Razorpay, UPI etc. and proceed the order. You will get an invoice with the track it, logistics details until the delivery.
In your one request, different microservices are integrated into the platform like Auth Servers, Payment gateways, Logistic supplier APIs, E-commerce API, and those have been processed to perform your request.
While Microservices are best for cloud applications, there are two important aspects which makes microservices technology successful for platforms like AWS and Azure. The two characteristics are:
1. Easy to implement—with the microservices architecture, you can make changes without impacting the rest of the application. There are several steps in this process e.g., easing the upgrade process of an application by using APIs.
2. Microservices and APIs can improve Productivity and flexibility of developers who use it as part of cloud technology, especially with tools like Amazon SWF to enable developer for more productivity.
3. Containers are another technology that complements microservices. Whenever you develop your application, the containers hold all the dependencies, environment and configurations before setting up the code in an isolated environment.
There are certain benefits to using Containers:
- Containers provide a lightweight option to virtual machines (VMs).
- It is easy to deploy containers as it takes just one command to set up.
- Containers are easy to work with when it comes to organizing the applications from the start-up phase.
- It is also easy for developers and users who don’t know how a technical environment works.
- Servers are one of the biggest expenses for a business. In the cloud, you pay for what you use.
- Operating systems are also available in the cloud which allows developers to choose their preference easily
- There are different tools and libraries which helps in providing a standard infrastructure across the cloud platform
- Security is another major concern when it comes to APIs, but with several ways to develop secure servers, there are several ways to secure APIs with security measures like sensitive data like user information should be encrypted during transit or at rest on a server and in an application.
How Security can be implemented in these Cloud API’s
APIs also face the same level of attacks just like any other software with many vulnerabilities and more attack surface. Since APIs allow users to use many microservices it should be well developed with best practices by keeping top API security threads into consideration.
One of the major Attack API’s can be exposed to is Code level bugs and Injection attacks. Proper code review and regular penetration tests can help to minimize risk. Next one is improper authentication and authorization protocols which can make the APIs ends loose and allow attacker to exploit and access the sensitive data
Business APIs should define their business logics and constantly review them to avoid misuse of the input validations.
Best practices:
- Create definite policies in terms of input validation to prevent injection attacks.
- Cloud Platforms default provide API management tools to create security and admin policies to manage multiple API to prevent attacks like Abuse, DDOS, rate limiting etc.
- Do not encourage practice of storing the keys, instead use the SSO mechanism OAuth mechanism for secure authentication.
- Implementation of additional security controls like SSO, MFA and session expiry can prevent attacks to larger level
- Implementing Role Based Access for APIs and providing access as per requirements.
- Doing API risk assessment to identify privilege access level vulnerabilties and unauthorized access resource vulnerabilities to mitigate access to such resources from public domains








