How to ensure Kubernetes (K8) and Container Security
Last 5 years was all about the transformation of Traditional Infrastructure and Cloud Adoption, Migration by many businesses. From Traditional Data Centers to cloud, from cloud servers to Containers, pods, from containers to functions, Infrastructures have been changed in many ways.
Before jumping into Kubernetes, we need to understand container architecture.
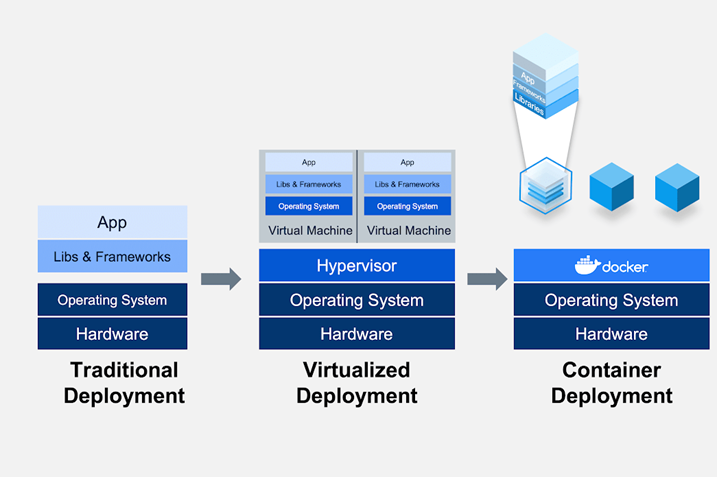
If you see the above image you will understand that Traditional Deployment has Servers, Hardware appliances etc. Then the virtualization also replicates the same in a better manner, but it still consumes much resources and eventually increases the cost.
Then came the container deployment. Here we have the basic resources like Hardware and Operating system and then instead of having a whole virtual system in place, we will have a platform on which applications can be deployed. We call it docker, docker resembles the space on a big ship where the cargo containers will be placed with low space and more in number.
Docker helps us to launch our applications with low resources, high efficiency. Containers as nothing but a package contain all the files required for an application.
What is Kubernetes?
As per official website, “K8 is an open-source container orchestration platform for managing, deploying and automating workloads. It was made public by Google in 2014”.
A container is a package containing all the required files for an application to run. When multiple containers run on a docker or multiple dockers as per the architecture, we need someone to monitor, schedule and manage the workflow.K8 does the same work. It automatically deploys, schedules the workloads.
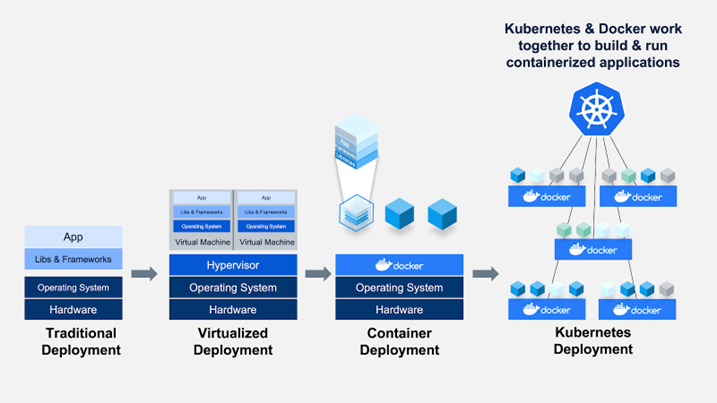
As seen in the above image, K8 manages multiple containers and automates the workloads.
K8 deployment consists of two main parts. 1. Cluster and 2. Node
- Cluster: Group of nodes including a master node and worker nodes as per requirement.
- Node: Host on which containerized applications run.
Nodes can have containers individually or a pre-configured set which we call pods. Pods provide the ease to scale up as they all have similar configurations.
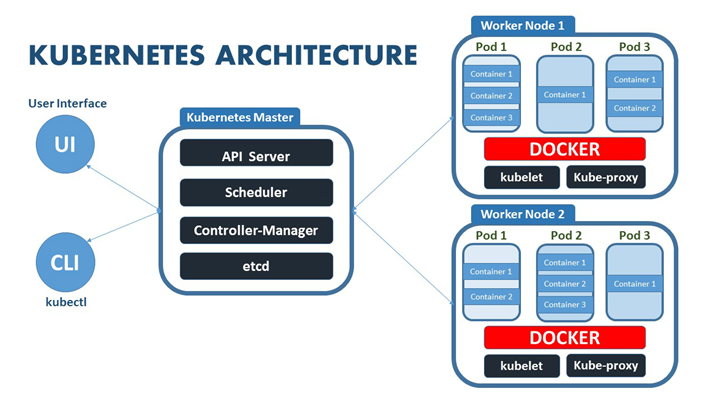
K8 Architecture
Kubernetes became an integral part of Cloud Native Deployment architecture. K8 architecture is a complex architecture yet, an efficient one.
K8 is all about 3 planes. Control, Management and Data Plane.
- Control Plane is all about controlling the K8 using UI, CLI for managing the K8 clusters
- Management plane is all about managing the cluster, pods and nodes
- Data Plane is where the actual data related to configuration, schedule, data transfers lies
Kubectl is a command line tool used to access the K8 API for scheduling task and managing the master node in the cluster.
In any node, Pod configuration plays an important role as it needs to balance the application performance with using minimal resources along with processing the instructions from Master Node.
Pod Configuration YAML files should be secured and access to be restricted to prevent any misconfiguration.
Open Source K8 Security Tools
Securing and Scanning K8 involves multiple layers from Cluster to Node to Container and then Code,
Each of the layer security is responsible for K8 security. Evey layer should be implemented as per the best practices and should be up to date.
- KubeHunter
Kubehunter is an open source tool by Aquasec to scan K8 clusters for vulnerabilities.
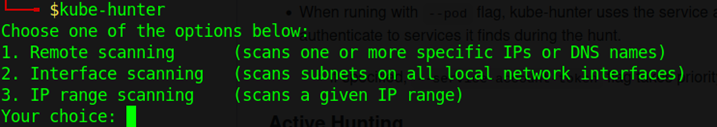
Kube-hunter have an option to scan in 3 ways. Remote, Interface and IP range scanning. This tool will help us to dig down k8 clusters for security vulnerabilities.
Source: GitHub – aquasecurity/kube-hunter: Hunt for security weaknesses in Kubernetes clusters
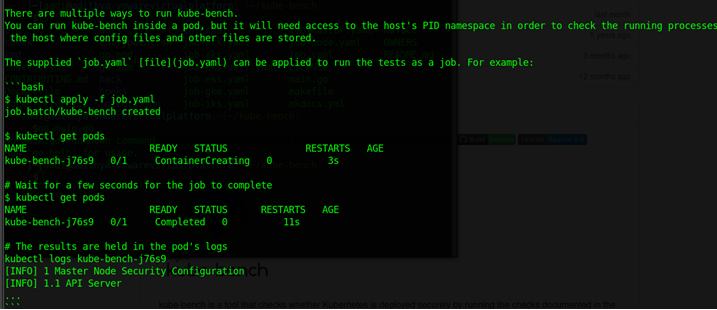
- Kube-Bench
Kube-Bench is a K8 configuration Audit tool as per CIS Benchmark standards. Tool is created in Golang and scan configurations are created in form of yaml files.
- Clair
Clair is a static analysis tool for scanning container images for vulnerabilities. Clair makes use of API for indexing Container images.
- Terrascan
Terrascan was created by Tenable, the market leader in Vulnerability scanners and Security Center. It acts as Nessus scanner for K8 by scanning the environment against the security standard and custom policies for any policy violations or security loopholes.
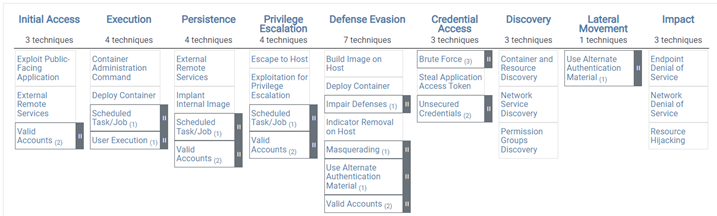
Kubernetes MITRE ATT&CK Matrix
MITRE ATT&CK has created a matrices for Containers also on their website which includes the tactics, techniques and Mitigations. MITRE provides various detected tactics and techniques which are used to identify and exploit known kubernetes or container related vulnerabilities.
Kubernetes Security Best practices
Security of K8 should be designed separately for control, management and data plane. Working of Each Level is different, hence different Security Strategies need to implement.
- Always keep all the components of K8 up to date with scheduled Vulnerability scanning and Patch management Process
- Create and Manage accounts in IAM as per the role and restrict access to limited individuals to CLI
- Ensure Critical Authentications are binded with multi factor Authentications
- Make sure to review to docker images /source code of container application running in the container before pushing into production for any privilege escalation, configuration loopholes
- Enable Logging and auditing events by creating security policies and integrating these logs to Monitoring tools like Kibana for alert detection and response
- Secure and restrict the access from API client to Kubelet API and Kubelet to K8 API by creating security policies around Node based Restricted Access or Role Based Restricted Access
Thanks for reading 🙂








