Post Credit: Ricoh Danielson
How to do Insider Threat or Risk Profiling: I think most of us would agree that it is important to perform insider threat profiling and hunting. Unsurprisingly, our security professionals are in agreement with this too! After all, 91% of confirmed data breaches involved an insider threat or malicious employee. This makes sense, since it only takes one person to make a huge mess out of the organization you work so hard to build!
Do you know why it is important to perform Insider threat profiling and hunting?
Have you ever asked yourself why you should perform insider threat profiling and hunting? First, have you ever wondered whether your organization is vulnerable to an insider threat? The answer is more than likely yes. There are many factors that make an organization vulnerable to insider threats. At the core of these vulnerabilities stem from individuals with malicious intent who have been able to bypass controls and security measures meant to protect sensitive data.
Let’s look at the idea of conducting an insider threat and insider risk analysis. For us to accomplish this, we must define the term insider threat/risk. The insider threat/risk could be an employee, contractor, consultant, or a person within the organization with access to valuable information or data. Now that we have identified these, we need to know what our business profiles might look like. So, what does this look like for your business? How are the high-stake key players in your business?
Detailed technical requirements and tools
Insider Threat or Risk Profiling is a method to identify, assess and mitigate the risks to an organization presented by insiders. At its simplest, it can be seen as an attempt to profile a person’s intentions, plans and future behavior on the basis of existing information about their background, behavior and thinking processes. The reasons for trying a profiling approach include assessing the likelihood of an insider intentionally causing damage to an organization or making unauthorized access to information assets resulting in damaging leaks of information.
It’s pretty tough and time-consuming to conduct insider threat technical reviews without tools. Assessing Insider Threats manually may consist of doing a few different things at one time. You might have to pull the Internet history, DLP Alerts, Computer Forensic image. Then we would need to develop a timeline in which we are interested. Reviewing a wide amount of data at one time we’re only spinning in circles or it will not inundate you with too much data. We need to narrow down a timeline for timeline analysis. Once we have a timeline now we have to understand what items of interest we are looking for. This might be anywhere from emails of interest all the way to topics of interest. It really depends on your investigation. As we can see doing this the manual way is very labor-intensive and cumbersome.
Insider Threat Tooling with O365
Now, let’s look at it from the inside of threat tooling perspective. Before we start diving into that we need to set the stage of what specifically insider threat use cases may fit your business name. Here are the top insider threat use cases.
- Detecting Compromised User Credentials
- Anomalous Privilege Escalation
- Command and Control Communication
- Data Exfiltration
- Rapid Encryption
- Lateral Movement
Now what does this look like from a tooling perspective.
Here are some examples. Lets look at an O365. There are some things we need to really look at here.
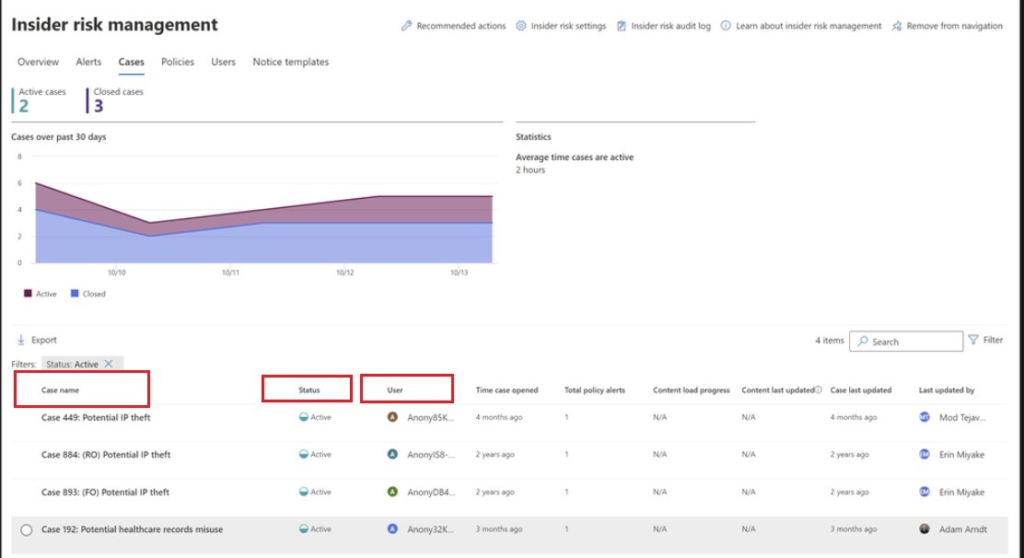
Above we can see that the 0365 alerts were tripped when it came to setting the policies within O365. These alerts tripped up and provided a case name, users and a time range. All these are going to be critical components when conducting an insider threats investigation. This also allows you to rate the incident along with providing a risk rating to the overall case and profile.
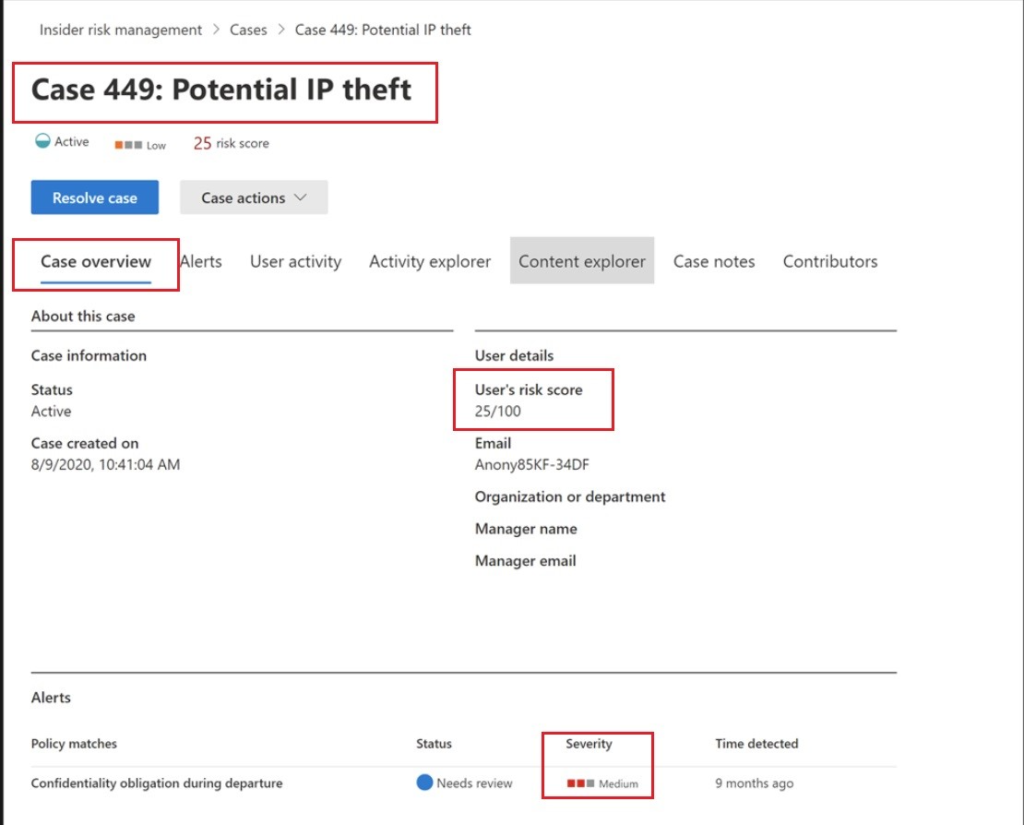
Above we will take a deeper dive into the individual case. In the highlighted sections we will understand that there are certain severities that the policy assigned certain values of the data. As we dig in further, we will see not only the case overview but also the risk rating associated with it. Along with that, we can determine what was the mechanism in which the policy was tripped. In this case it was email.
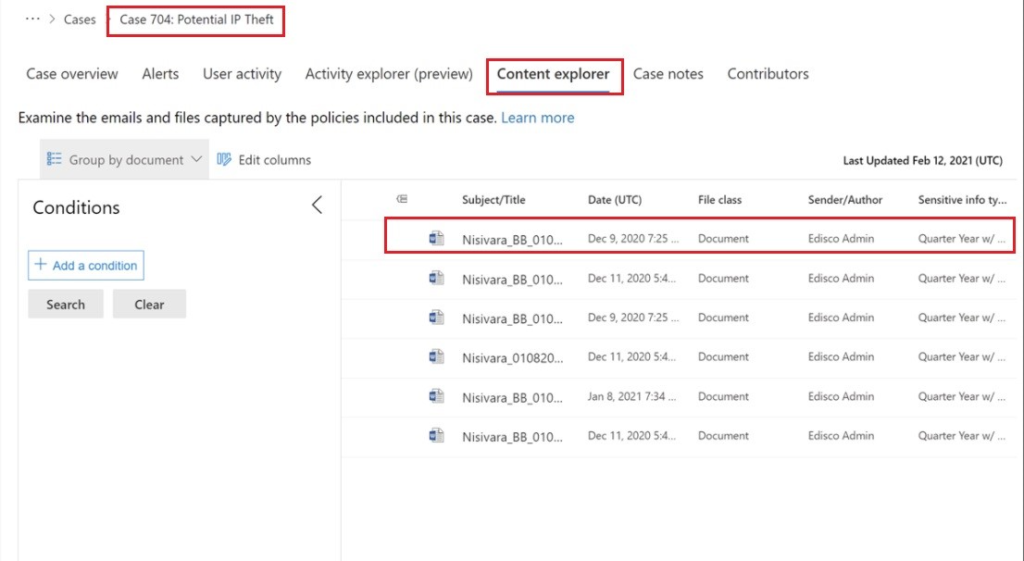
When we find meditative points of interest, we can then further expand our investigation into the concert explore tab. This tab provides us not only the time, file and also the center. Furthermore, it provides us with the documentation for the file of interest. This will be critical when conducting digital forensics and immediate analysis.
Analyzing Key findings and data elements
Analyzing insider threat (insider behavior) or risk profiling techniques to identify malicious users, associated techniques and patterns, possible motives / triggers and other index of activity. Insider threats can be tracked in a variety of other ways as well: through logs and metrics associated with specific actions by users over time, by analyzing behavioral patterns to identify deviations from pre-defined patterns, and through data elements extracted from stored data.
When we do the insider threat analysis there are a couple of things that we need to take into consideration whether we do them manually or with tools. When we were reviewing these data elements, we needed to extract certain critical points such as header analysis, user, data points in time. Help us determine what the insider was trying to achieve but also pointers in a different direction of tactics and different protocols that insider threat may be leveraged to carry out their attack.
Why do we choose manual processes over tools?
There are several interrelated and broad issues affecting the decision to use manual processes over tools for Insider Threat or Risk Profiling. These include: lack of transparency in using automated tools, the cost effectiveness of using automated tools and perhaps most importantly, concerns about the accuracy of the automated tools. This last point is important because we know that many organisations use low-risk employees as test subjects to verify the accuracy of any advanced analytical algorithms being used by the software.
As we can see from the above conducting an insider threat and insider risk investigation manually takes a lot more time along with a lot more additional resources. Some companies only have manual processes to conduct any sort of investigation let alone an insider threat investigation. If a company can really use tools, possibly open source tools it would benefit them with time and speed. There are several open source tools (such as OSINT and FOCA) that can assist us in performing social reconnaissance. However, we see many organizations’ rely on their own manual processes or use services provided by vendors to conduct this type of analysis. Understanding an insider threat and getting ahead of them before damage is done can help protect the Company and mitigate the financial impact.
Summary
There’s a lot to consider here. Whether you’re doing this manually or whether you are doing this with tools there’s a lot of data to digest and understand. In order to catch an insider threat this may consist of understanding the company’s vulnerability is not only from a cyber perspective but also from a business perspective. If you put your hat on “what are the most critical assets to the company and what would cause the most damage” this would put us in different mindset of what an insider threat might be in your environment. It might be the CEO, CFO or the IT generalist. It really depends on the business and also it’s most important critical assets and data. Having a good awareness program in place as well as setting up monitoring tools can catch insider threats before they do any damage. Corporate cyber security teams must be involved in this process or it will fail or not be taken seriously by company employees. A balance needs to be struck between an employee’s privacy and their employer’s need for the business to function safely & securely. An insider threat program can help with this but requires the correct framework and only gains from best practice.








