How to hunt Follina using Splunk
Written By Sai Adithya Thatipalli
Security Researchers and hackers will always be on the run to hunt 0-day vulnerabilities and try to exploit them. From small firms to large enterprises, their products are always undergoing constant testing and exploiting. Because of the increase in data breaches, and attack activities, companies are trying their best to update their products on a regular basis but this doesn’t help them from getting exploited.
What is Follina?
Follina was a Zero-day vulnerability identified in Microsoft Support Diagnostic Tool ( MSDT), a tool used by the Microsoft support team to analyze data shared by the user and support them accordingly. But on May 27th, 2022, a security researcher at Microsoft identified that there is an easy to exploit bug in the MSDT that attackers can leverage and take control of the system.
On May 30, 2022, Microsoft officially addressed this as a bug and issued CVE-2022-30190. This vulnerability exists in all the Microsoft office products where the attacker can attack previous versions also. The vulnerability has received the name Follina and has been tagged with a score of 7.8 out of 10.
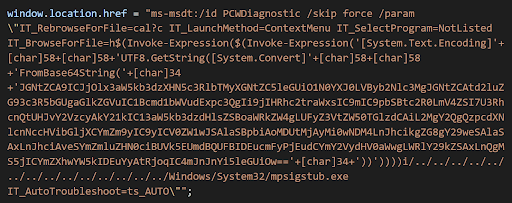
How does Follina work?
Security Researcher Kevin Beaumont explained how Follina works in a blog post – Follina – a Microsoft Office code execution vulnerability. In simple words, the attacker can use importing of templates remotely in the Word Document option to exploit and redirect it to the malicious site. The attacker can then install programs, view, change, delete data, or create new accounts in the context allowed by the user’s rights. This is still possible if we disable the macros as the MSDT tool is performing this activity.
Microsoft has a default protection layer “Protected View” which won’t allow links to load unless manually allowed. But this feature cannot protect against this vulnerability – it is bypassed if we convert or save the file in Rich Text Format (RTF); when opening an RTF, the Windows file preview pane will automatically launch the file for a preview.
Immediate workaround and precautionary measures :
As a precautionary measure, Microsoft advised users to disable the MSDT URL protocol. This is the protocol used to communicate remotely between the Support tool and Microsoft Applications.
Several Microsoft Security solutions have created a detection and prevention mechanisms to identify the suspicious behavior
- File and process detections are provided for detecting MSDT-related processes using Microsoft Defender.
- Trojan: Win32/Mesdetty.X (blocks msdt command line)
- Behavior: Win32/MesdettyLaunch.A!blk (terminates the process that launched MSDT command line)
- Trojan: Win32/MesdettyScript.X (to detect HTML files that contain msdt suspicious command being dropped)
- Microsoft Defender for Endpoint tool also has the capability to perform a behavior-based analysis to identify Suspicious behavior in MSDT applications and Office Apps.
- Microsoft Defender has the rule to block office applications to launch MSDT or any other child process
Hunting Follina using SIEM tools like Splunk
Splunk is one of the most commonly used enterprise applications in terms of data analytics, data correlation, and aggregation. Splunk is also used as a monitoring tool in SecurityOps to integrate multiple log sources in one place and review the events and trigger alerts.
Based on the POCs and the sources through which these behaviors can be observed, Splunk created a query to retrieve information about the trigger of the MSDT process.
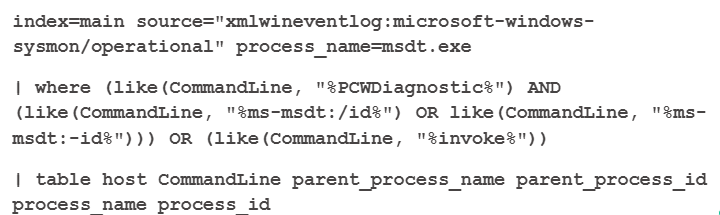
This query uses the Microsoft’s system monitor process logs as main source and msdt process as sub category.
If the MSDT process is started then the query narrows down to see if the command line contains commands of diagnostic process “PCWDiagnostic” along with ms-msdt:/id OR ms-msdt:-id commands or any request to invoke another process by the MSDT process.
We can narrow it more by taking the parent process id as another data value and seeing if any traffic has been generated during the process time frame.

Here, we take sysmon as source log and take the parent process as data value and Microsoft Event code =3, which is used for network-related activities. We will extract the data of source and destination IP addresses and ports for any network-related activity.
We can create an alert mechanism for this query on a real-time basis to trigger any suspicious behavior in the environment.
Splunk also provides the one-tap query run and threat advisory containing the indicators, detected process, and other information related to this vulnerability to all the tools which use the Splunk search engine.
After the critical event, the MITRE community also shared insights on under which category or technique will this vulnerability comes under.
- ATT&CK Technique – T1218 System Binary Proxy Execution is performed majorly by exploiting the system process of Microsoft like DLL, etc.
How is Microsoft tackling this vulnerability?
Microsoft has released a security patch to fix this vulnerability during the Patch Tuesday for the month of June. MSFT urges companies to install the patch on a priority basis to secure, which is always considered the very basics when it comes to cybersecurity! Keep updating often and you will avoid a large number of the threats that people suffer with today.








