WPScan for WordPress
Written By Indrajeet Bhuyan
WordPress is one of the most popular CMS used on the internet today. According to BuiltWith, currently, more than 455 million sites are running on WordPress. According to W3Techs, WordPress powers 43% of all the websites on the Internet, including those without a content management system (CMS) or with a custom-coded CMS.
Whenever you are testing any target be it client or bug bounty you will for sure come across a website that is running on WordPress.
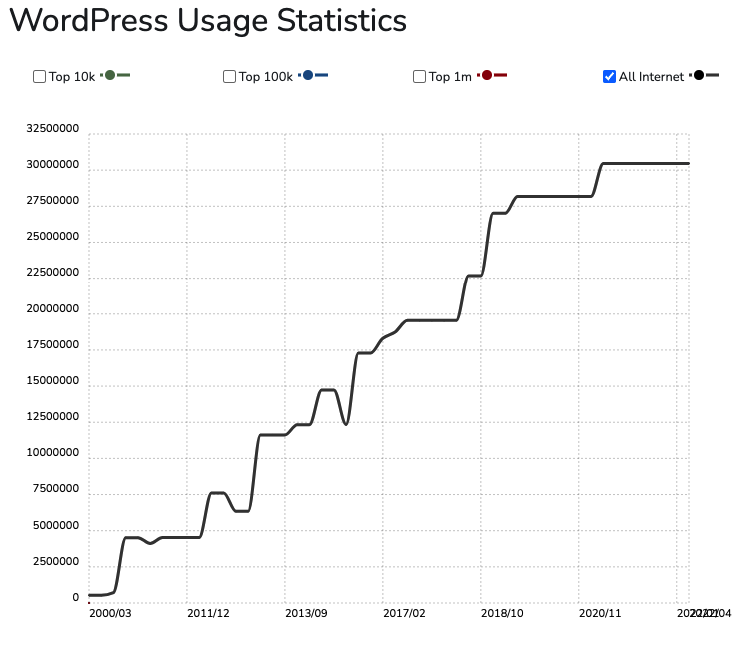
Though WordPress was initially made just for running blogs, today – thanks to its ease of use and wide range of plugins and themes – it is being used for e-commerce sites, learning platforms, and many other types of websites.
These days most companies host their blog or marketing site on WordPress. What makes WordPress interesting is that since such many people use WordPress, one flaw in it equals the same flaw in all the sites running the CMS.
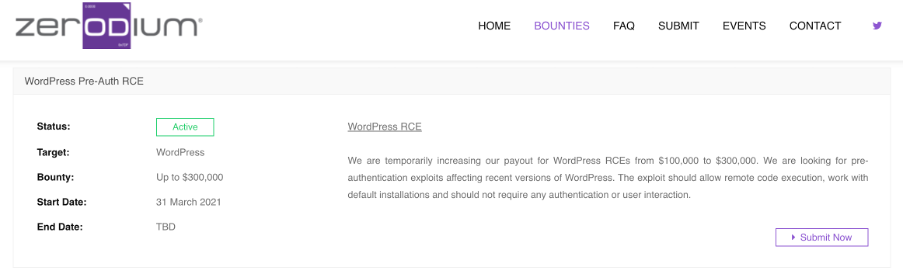
Critical flaws in WordPress are in so demanding that popular exploit acquisition platform Zerodium is paying researchers up to $300,000 for finding a remote code execution vulnerability (RCE) in WordPress. Remember, one RCE in WordPress means millions of exploitable RCEs all across the web.
Today in this article we will explore a tool that can be used for WordPress scanning and will help you find flaws in WordPress-based websites quickly. Before using the tool, we first need to check if the website is using WordPress or not.
- Use Wappalyzer: Wappalyzer is a Chrome extension that will help you detect what technology is being used by the website. If it uses WordPress, it will show up.

2. Use a Nuclei template: In one of my previous articles, I discussed nuclei and how to use it. Nuclei have a template called wordpress-detect.yaml which can be used to detect if a website is running on WordPress.
Once we are sure that the site is running WordPress, we can start using the WPScan tool.
The WPScan CLI tool is a free for non-commercial use, black box WordPress security scanner written for security professionals and blog maintainers to test the security of their sites. The WPScan CLI tool uses our database of 28,908 WordPress vulnerabilities.
Using WPScan, we can find out:
- The version of WordPress installed and any associated vulnerabilities
- What plugins are installed and any associated vulnerabilities
- What themes are installed and any associated vulnerabilities
- Username enumeration
- Users with weak passwords via password brute forcing
- Backed up and publicly accessible wp-config.php files
- Database dumps that may be publicly accessible
- If error logs are exposed by plugins
- Media file enumeration
- Vulnerable Timthumb files
- If the WordPress readme file is present
- If WP-Cron is enabled
- If user registration is enabled
- Full Path Disclose
- Upload directory listing
Once installed the first thing that we need to do is update its database of the latest version by running the following command: wpscan –update
Once it is updated you can run commands for a different task:
- To scan installed plugins: wpscan –url http(s)://your-domain.com –enumerate p
- To scan vulnerable plugins: wpscan –url http(s)://your-domain.com –enumerate vp
- Scan installed themes: wpscan –url http(s)://your-domain.com –enumerate t
- Scan vulnerable themes: wpscan –url http(s)://your-domain.com –enumerate vt
- Scan user accounts: wpscan –url http(s)://your-domain.com –enumerate u
- Scan vulnerable timthumb files: wpscan –url http(s)://your-domain.com –enumerate tt
A demonstration
- Try to enumerate all users of the website. This can be done by running the command: wpscan –url http(s)://your-domain.com –enumerate u
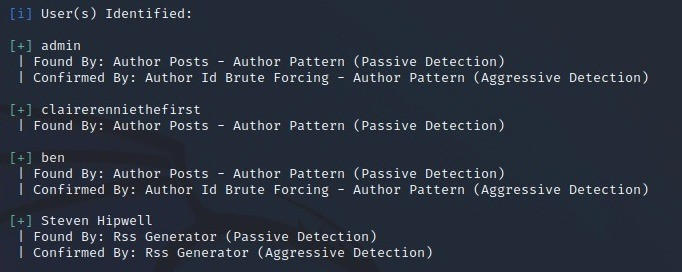
2. Check for vulnerable plugin installed in the website. Command can be found above.
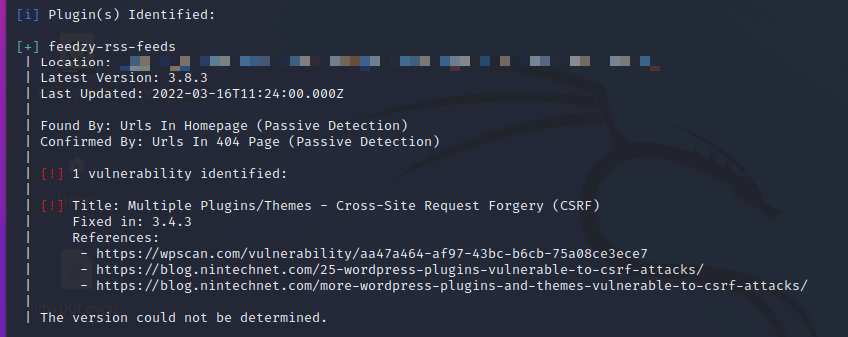
Conclusion
WordPress is one of the most popular CMS on the internet. It is very common to find WordPress-based sites while doing penetration testing. One should add WordPress website testing methodology to their checklist while pentesting as there is always a high chance of getting flaws in WordPress-based sites as often website owners don’t regularly update the site or sometimes ends up running outdated themes/plugins.








