How to mitigate DDoS Attacks
By Nazifa Alam
Distributed Denial of Service attacks, if successful can lead to an average loss of $20,000-$40,000 per hour, no doubt leaving the attack as one of the most alarming and expensive cybersecurity threats prevalent in the evolving digital landscape. This is a number that even some of the largest organisations can feel threatened by. With each hour of an attack, ramification costs increase. Therefore, what can be done to reduce these costs?
Common forms of DDoS attacks
- Ping of Death – Where the attacker(s) send multiple pings to overload the targeted device. IP packets which are larger than the network’s maximum packet capacity is sent to the victim’s network which are then reorganised, leaving the network unable to handle legitimate packets. This forces the network to become inactive.
- UDP (User Datagram Protocol) Floods – This form of attack floods the targeted network with UDP packets with the aim to flood ports on a remote host. This way, the host continues to look for an available application at the port. Once it is discovered there is no receiving application, the host transmits that the destination was not reachable. This consumes network capability, preventing other devices from connecting.
- NTP Amplification – Where the attacker(s) exploits the performance of NTP server.
- SYN Flood – This involves the attacker using the TCP connection to render the targeted network unavailable. The method behind this consists of SYN requests being sent to the targeted network, which replies with a SYN-ACK response. In response to this reply, the sender who is typically expected to respond does not or sends a response using a spoofed IP address. With each unanswered reply, more network resources are used, preventing other devices from connecting.
- HTTP Flood – This type of attack involves overwhelming the targeted server with an overload of HTTP requests. This attack is effective when the targeted server or application becomes required to meet each HTTP request with the maximum responses.
- Zero-Day Exploits – One of the more powerful forms of attack as this is when all the security flaws of the targeted server or application will become known. The best prevention method against Zero-Day Exploits is to routinely install the released patches as soon as possible.
- Slowloris – Involves the attacker(s) systematically sending incomplete HTTP requests. Each request occupies the network’s resources until the server becomes no longer able to form connections. This type of attack does not need any bandwidth hence, the popularity of this form of attack among cybercriminals.
Why do cybercriminals like to carry out DDoS attacks?
A common reason behind DDoS attacks includes extortion. Typically, the victims of DDoS attacks tend to be corporations of small to medium-sized businesses however, the amount of DDoS attacks being levied onto larger corporations has largely increased in the past few years.
Additional causes behind DDoS attacks include hacktivism, theft, disgruntled employees or simply boredom.
DDoS attacks commonly occur when cybercriminals identify underlying vulnerabilities which likely have not been patched in time. Sometimes, automated bots are used to scan for vulnerabilities of multiple targeted websites which are then attacked once an opening is detected.
Checking if your server is being targeted in a DDoS attack
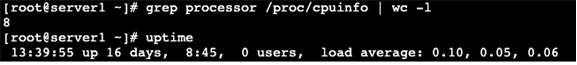
If you suspect that your server is being targeted in a DDoS attack, you first need to check your server. Entering either uptime or top commands will give you an idea of server’s current load.
An acceptable load is dependent on the available number of threads or CPU resources. To find out the current load of your server, you can enter:
grep processor /proc/cpuinfo | WC -1
This will notify you how many logical processors (threads) are available. In the case of a DDoS attack, you may see a load at double, triple or past maximum load.
The two following commands will give you your server load and uptime:
grep processor /proc/cpuinfo | -1
Uptime
An example of how this can look is as followed:
How many IP addresses are connected to your server?
As DDoS attacks are committed through an established connection with your server, it is important to check how many IP addresses are connected to your server.
To do this, you can enter the following command:
Nestat -ntu|awk ‘{print $5}’ | cut -d: -f1 -s|sort|uniq – c|sort -nk1 -r
For example:
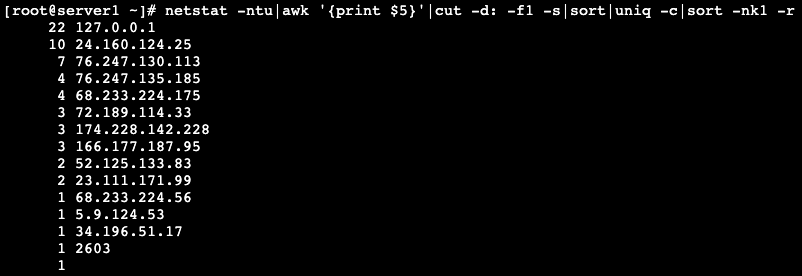
This will give you a list of how many IP addresses are connected to your server and the number of connections each one has.
How to mitigate a DDoS attack?
Once you realise that your server is being targeted in a DDoS attack, you can enter a few commands to block these suspicious IP addresses.
To begin with, you can use the command ‘route add (suspicious IP address without the bracket) reject’ to block the suspicious IP address.
Once this has been done, you can check if the suspicious IP on the server has been blocked using the command:
route -n |grep ipaddress
You can also block IP addresses on the server using itables with the following commands:
iptables -A INPUT 1 -s IPADDRESS -j DROP/REJECT
service iptables restart
service iptables save
You will then need to halt any HTTPd connections and restart them by inputting:
killall -KILL httpd
service httpd startssl
If there is more than one unrecognised IP address forming a multitude of connections, these steps can be repeated.
The most important practice
It is indeed difficult to handle a DDoS attack, given that multiple spoofed IP addresses may be used. Blocking hundreds and thousands of these attacking IP addresses can also be very time-consuming. Therefore, the best method against DDoS is actually to have in place effective prevention strategies in place.
This can include:
- Ensuring high levels of network security – By having in place traffic scanning barriers between networks, installed anti-virus and anti-malware software, effective endpoint security practices, web security tools in place and tools to check if traffic source is consistent with the origin of address.
- Using multiple distributed servers – Which will make it harder for the hacker(s) to simultaneously attack.
- Staying on top of the warning signs – Which can include slower performance, multiple crashes, a spike in traffic from users sharing a common profile for example geolocation and web browser version as well as high demand for a single page and poor connection.
The growing financial strains
The IT Security Risks Survey conducted by Kaspersky in 2017 showed that the average cost of a DDoS attack has vastly increased. For SMEs, the cost increased to $120k and for larger corporations, the cost levelled to $2m per attack. These figures have continued to increase into 2022 and will do so into the future years.
Conclusion
The financial consequences that come with DDoS attacks continue to increase and with the increased use of botnets, blocking an overwhelming number of IP addresses is without a doubt a difficult task. During instances like this, stopping a DDoS attack is incredibly hard. The best practice that can be done against DDoS attacks is to utilise all prevention strategies possible.








