In our previous article, we covered we can collect crucial Information on Windows Machines. But, attacks won’t happen only on Windows Machines but on other flavors like Unix and Linux. There are several instances where attackers exploit the vulnerabilities belonging to the Linux environment.
These vulnerabilities can be libraries, processes, kernel related, etc., so it’s important to protect and also know the method of extracting critical information from Linux machines. Unlike Windows, Linux is an open-source project and it has different flavors (or distros) for individuals based on their requirements. Some of them are Ubuntu, OpenSUSE, and RedHat.
Now, let’s start performing the digital forensic analysis.
Forensics for Linux
Since we covered detailed basics of forensics, I’m not repeating the same. In a nutshell, Digital Forensics is the way of collecting critical information and analyzing the activity to extract the performed activities. There are many ways to extract information. Like the way we did in windows, we will focus on collecting basic information.
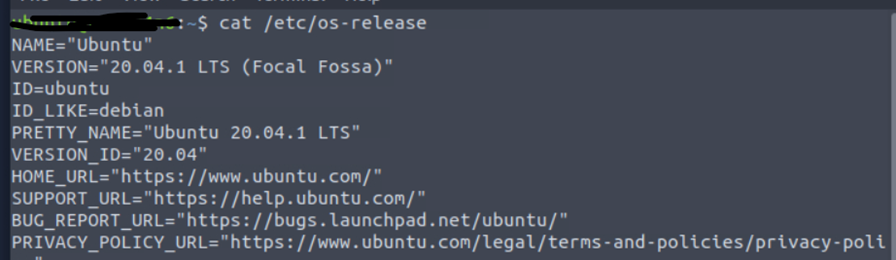
We have launched our Linux instance and went over to see which OS flavor we are using, along with version numbers. This is important as many OS-related vulnerabilities can be taken into consideration.
Based on the above screenshot, the machine we are running uses Ubuntu. People familiar with Linux know about the file systems – once we get a note of the os-version, we should see the username and password hashes to see existing information.
Starting to Investigate
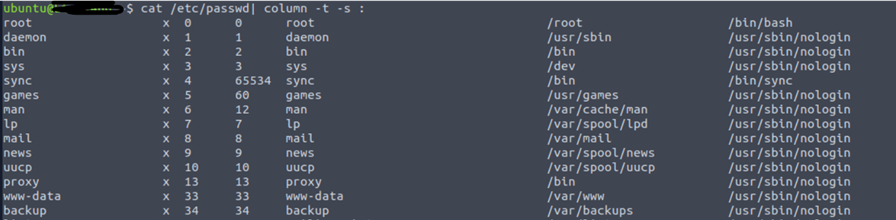
Using this file, we can see the users and their permissions. Attackers often target these files to get hashes of passwords.
We will use the command cat/etc/[passwd] | column -t -s :
Once we do that, the output contains 7 colon-separated fields, describing username, password information, user id (UID), group id (GID), description, home directory information, and the default shell that executes when the user logs in.
Users can be formed in groups for better management. We should not ignore group information as some policies can be assigned to groups, like user accounts and system accounts.
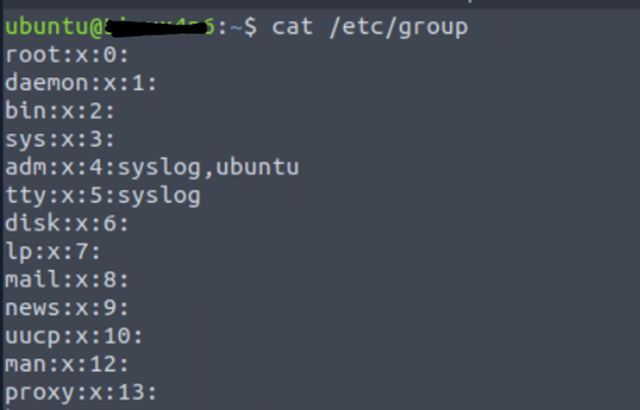
Based on the above snapshot, we can see that the Ubuntu user belongs to the ADM group along with the group id.
Next, we need to which ids belong to the sudoers list. This list provides users to have same access level as root.
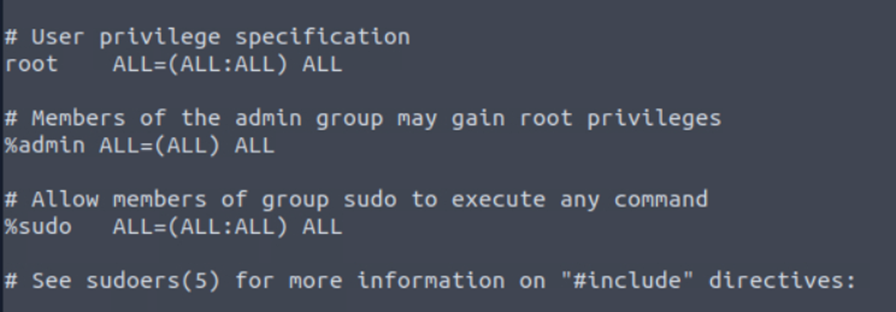
Now that we understand what all files to look into, we need to get some additional and critical information like Login Information and Authentication Information. This information can be retrieved from the log files in the var directory.
Using var
There are many types of logs in the var directory.
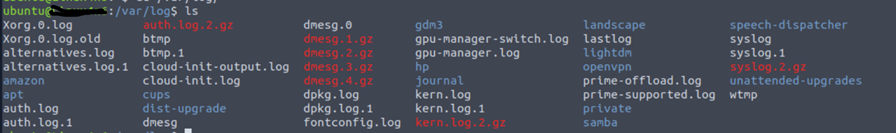
But, our focus is on only two logs btmp and wtmp.
- Btmp saves failed login logs
- Wtmp saves successful login logs
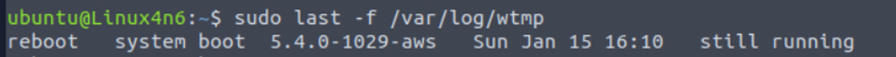
Now, I will read authentication logs to see the details of users logged in along with other information.
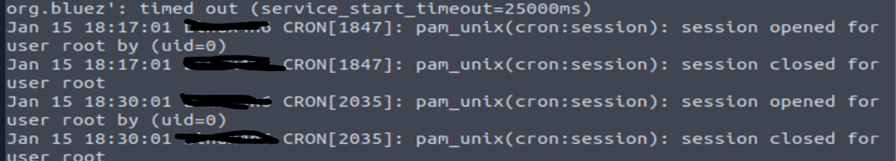
The last logs in the log file show timestamp username, cron session, and along with session details.
Syslog for Linux
The next one is the syslog; nothing but the system logs. It captures all the authorized and unauthorized changes. It is a continuous log-generating file; once the default storage of the file completes, then it will create a new file.
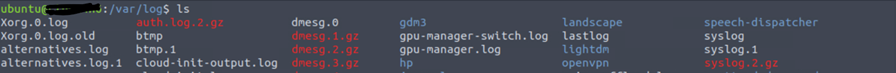
As we have captured all the important information, the next step is to capture information related to the system config and other config information. These configs are crucial as they may impact the security and functionality of the systems.
We need to know what processes are running using command ps aux.

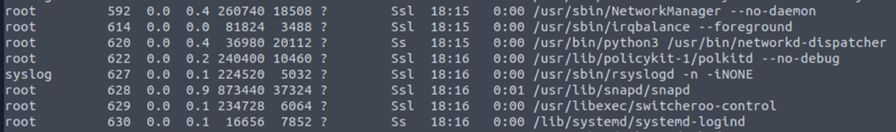
Often, attackers try to spoof processes and run malicious programs in the same way. Unless we analyze the information, we won’t be able to identify the source of the process, the path from the place it’s executing, the user running it, and the way of execution.
The next way is to watch running or scheduled tasks because some stealth processes are run using scheduled tasks for a short duration. This mainly occurs with worms and C2 connections.
Cron Jobs for Linux
The first among them is cron jobs. Cron jobs are commands that run periodically after a set amount of time. A Linux host maintains a list of Cron jobs in a file located at [/]etc/crontab. We can read the file using the cat utility.
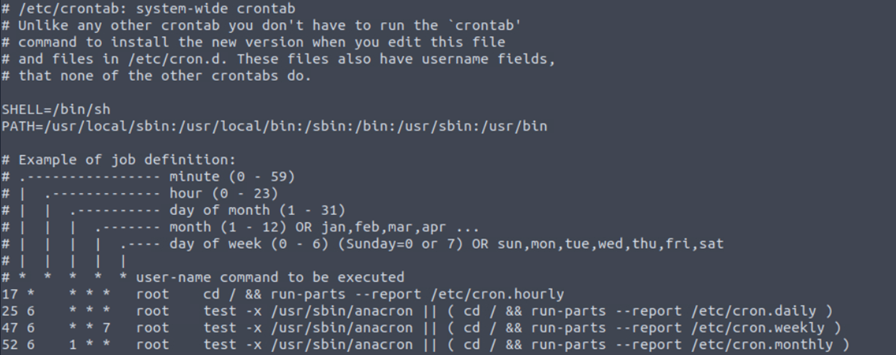
The above terminal output shows the contents of a sample [/]etc/crontab file. The file contains information about the time interval after which the command has to run, the username that runs the command, and the command itself. It can also contain scripts to run, where the script that needs to be run will be placed on the disk and the command to run it will be added to this file.
Startup Services for Linux
Next is startup services. This is because if any code is scripted in a way that the task will initiate after a restart. So these can be checked using [/]etc/init.d.
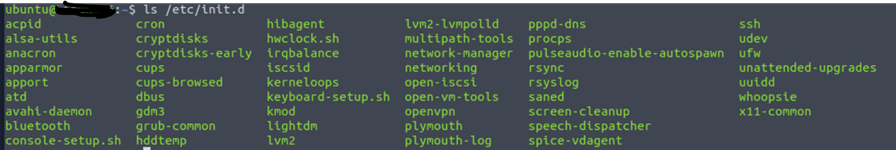
If you identify any suspicious process, it’s a process that needs to be reverse-engineered.
Knowing what programs have been executed on a host is one of the main purposes of performing forensic analysis. Till now, we understood about users, usergroups, tasks, system processes, and all, but that task requires elevated privileges. These executions are recorded in logs and these logs can are useful for forensic analysis.
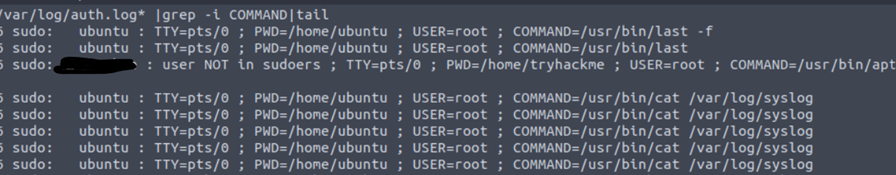
These logs will have all the required information.








