DDOS is called the “takedown” or known as the relentless attack. If a firm does not have the proper network defense or a DDOS process or tool to ensure it can combat DDOS threat actors, then it might be a rough day. Threat actors can cause significant damage.
Some suitable lessons learned from a DDOS attack can be captured from the world famous uses cases:
- Google’s DDOS of 2016
- AWS DDOS of 2020
- Mirai Kerbs and OVH DDOS of 2016
- EU’s Gambling Company DDoS Attack of 2021
As we can see, these attacks can come from anywhere and everywhere at any time!
You cannot hit what you cannot see
So, what might these DDOS attacks look like? Internal graphs can show how the timeline of bit might show how there might be accessing and or attempts to enter. We can look at the high and low points to determine a baseline.
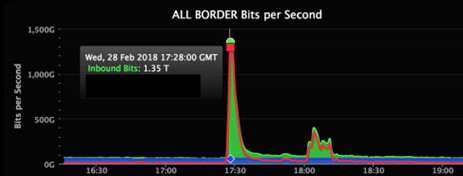
Heat mapping
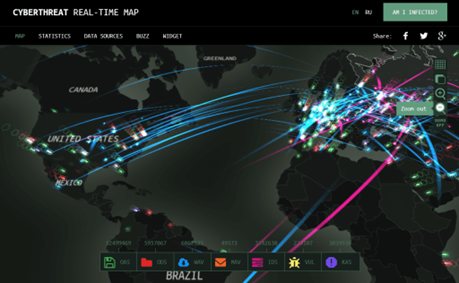
Firms with funds and firms without
Suppose your firm has funds to budget for a DDOS tool. You might want to look at NeuStar or botman DDOS. Now, these tools might come at a cost. Some devices such as these can range anywhere from $100,000 to $1,000,000 contracts. It all depends on the net flow, where it flows, and how it flows. Tools like Botman can help address root attacks and ML/ AI-based attacks.
Allow listing vs Blocklist
Now, if you are in a position where you are either a small firm or do not have any funds, then it will consist of fundamental tactical handling.
Bottom line, one of the best things you can do is go a “allow listing” approach from the start. If you must do blocklisting, it is cool, but you will be playing a “whack-a-mole” game. This will be un-management. It all depends on your business too. If it fits your business operation to go to an allow list, that would be ideal. Even when firms are breached, one of the significant things we do is take the environment from open to a restricted allow listing. This, at a bare minimum, will help people add an extra layer of security in front of your environment, application, or network.
Why are we choosing manual process over tools might be a good idea
Automation
There are some good things on both sides when it comes to automation and manually.
Automation helps with speed and helps move things faster and learned. However, you need to ensure from the start that the automation needs to be fine-tuned and baseline from time to time to ensure new trends are being captured.
Manually
From a manual perspective, there is a lot to be said here. This will require a heavy left and also require continual baseline. Make sure you have hired a person just to handle this. So you will need to create certain firewall rules. The customer rules might require narrowing down and updating these rules are they are created and baseline.
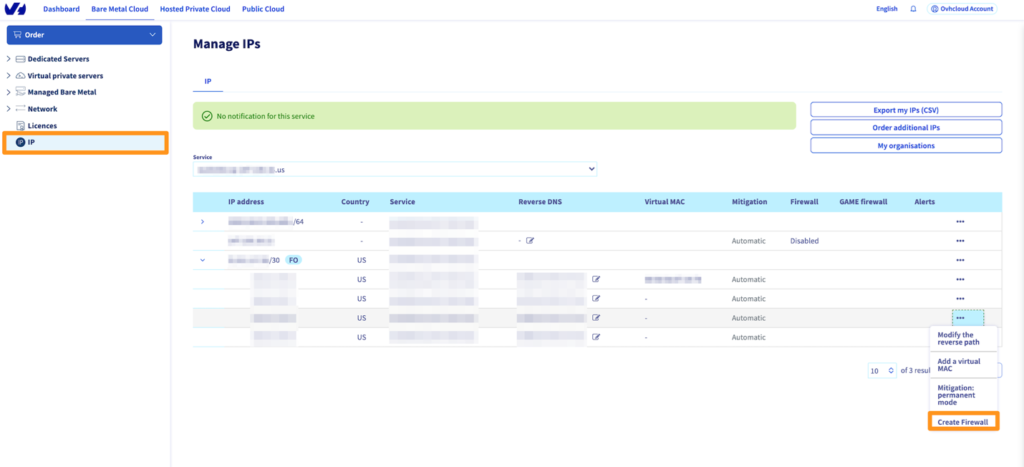
Analyzing findings and data elements
This is an area that needs to be conducted continually. This means you will need to conduct a net flow analysis to ensure there are no offenders. When it comes to these net flows, narrowing down the port, Ips and protocol might help conduct research.
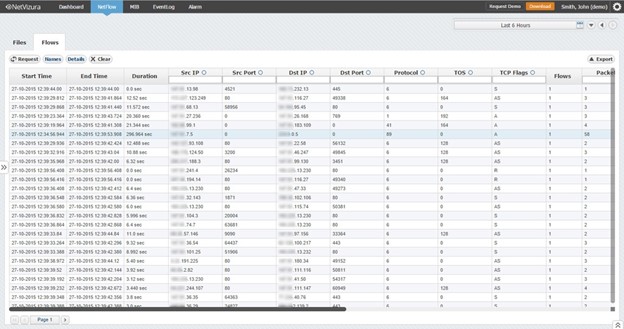
When it comes to these logs, a big something to consider is monitoring business hours.
How can I protect my organisation against DDoS attacks?
You must determine what makes sense for your business. You might need to have your environment forward facing, which can be a risk or threat to your business. These are inescapable facts of working in modern industry. Just understand the network and net flow and how to determine what is not right in your environment. On the other hand, use your tools. Let the device do the work; let the firepower do the job to mitigate the threat. Lastly, be your first responder.








