As we move from one year to the next, cyber-attacks are on the rise once again. While many people focus on attacks against applications and the web, it’s just as important to pay attention to network attacks. These can be just as damaging to crucial infrastructure.
As the network infrastructure has evolved over the years, it has become more than just a system for transporting packets, IP addresses and protocols. It is now a complex system that supports the operation of cloud networks and many other types of data., so we should be aware of different ways to identify critical network infrastructure information and approaches to attack.
In this article, we are going to understand how the tool Snort works.
What is Snort?
As per the official documentation, “Snort is the foremost Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generate alerts for users.”
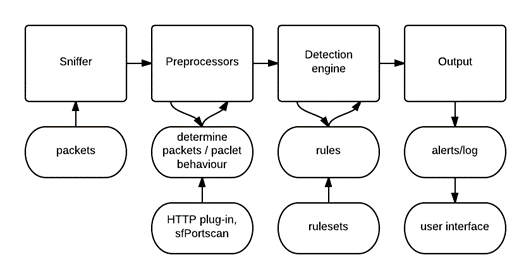
Main Components of Snort
- Packet Decoder – Packet collector component of Snort. It collects and prepares the packets for pre-processing.
- Pre-processors – A component that arranges and modifies the packets for the detection engine.
- Detection Engine – The primary component that process, dissect and analyse the packets by applying the rules.
- Logging and Alerting – Log and alert generation component.
- Outputs and Plugins – Output integration modules (i.e. alerts to syslog/mysql) and additional plugin (rule management detection plugins) support is done with this component.
To detect any intrusions, we have two types of solutions: IDS and IPS. IDS is to detect the anomaly and IPS is to prevent suspicious behaviour. But as the attack methods evolved over the period, these solutions were divided into different types.
IDS are of two types :
- Network IDS: Monitor the network flow for any attack patterns.
- Host IDS: Monitor host traffic behaviour for any kind of attacks targeting the host.
1. Traditional( Network and Host) IPS: These are the original IPS systems that simply detect and block suspicious traffic.
2. Reputation-based IPS: These systems use information from a variety of sources to determine which traffic is safe and which is not.
3. Anomaly-based IPS: These systems look for unusual or abnormal traffic patterns that could indicate an attack.
4. Behavioral-based IPS: These systems constantly monitor traffic and compare it to known patterns to identify suspicious behaviour.
These IDS and IPS solutions have different ways to secure the infrastructure.
- Signature-based protection
- Proactive approach: Use algorithms to predict the behaviour and act.
- Reactive Approach: React in the best possible way based on attach pattern
Now we understood IDS, and IPS and also that Snort is an Open-source Network IPS solution.
So, what exactly snort can do?
Snort can detect a wide variety of attacks and intrusions, including buffer overflows, stealth port scans, web application attacks, SMB probes, and OS fingerprinting attempts. It can also perform protocol analysis and content searching/matching. Snort can detect and prevent intrusions on a network. It can also monitor traffic and analyze it for suspicious activities throughout, snort has in-depth functionality, and we can use snort in operating the different modes.
- Packet Sniffer
- Logger Mode
- IDS/IPS
Once we install snort from the official website, we can access snort using the CLI:
In the above image, we can observe all the details related to install snort.
For snort to work perfectly we need to create the configuration file or import the already created snort file from the sample configs.
We can see the snort is configured complete. Snort has another flag ‘-T ‘ which helps in analyzing the config files and rules created.
How Snort rules are created in configuration
Rules are heart of the snort configuration files which give the tool the capacity to protect from the attacks.
Snort’s intrusion detection and prevention system rules consist of two main sections:
- Rule Header
- Rule Body
The rule header defines the action based on the defined conditions, which includes protocols, network addresses, port numbers, and direction of traffic
The rule body section defines the message associated with a given rule,The following is an example of a fully-formed Snort 3 rule with a correct rule header and rule option definitions:
alert tcp $EXTERNAL_NET 80 -> $HOME_NET any
(
msg:”Attack attempt!”;
flow:to_client,established;
file_data;
content:”1337 hackz 1337″,fast_pattern,nocase;
service:http;
sid:1;
)
The rule header includes all the text up to the first ( , while the body includes everything between the two ( ).
Let’s breakdown the rule and understood how we can create
- The action defined in a given Snort rule’s header will not work until all the rule’s individual options execute completely. There are different type of actions we can create in the rules ( alert, log, drop, reject ).
- In the Rule body, we include both payload and non-payload detection rules. Based on the criteria we can configure elements like protocol, Port as payloads and configure it
Snort has a detailed documentation about the rule writing structure with description. For users comfort snort provides with pre-configured rules in both free and paid base.
In this article we have discussed the brief overview of snort, its architecture and rule creation basics.








