In this article, we will discuss more in detail Windows Forensic analysis and the process of doing it. Before going into it, we need to do a brief recap of the forensic steps of an infected windows machine.
There are three basic steps in digital forensics:
- System image and all other required information to be collected and machine to be recreated for analysis.
- Based on the possibility, of performing live analysis or isolation analysis
- Examine every log, change, and process executed on the system
- Note the changes and report the root cause
Earlier, we touched briefly upon live analysis, capturing, and analysis of the Network and System process. Now we will explore how can analyze certain collected information like System process logs and registry information.
The Windows Registry is a collection of databases that contains the system’s configuration data. This configuration data can be about the hardware, the software, or the user’s information. It also includes data about the recently used files, programs used, or devices connected to the system.
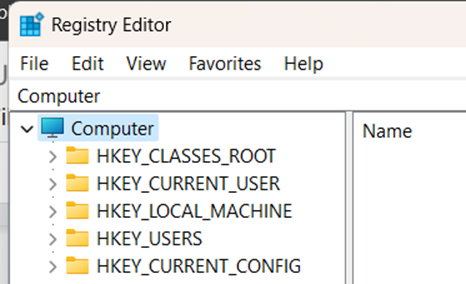
The Windows registry consists of Keys and Values. The registry on any Windows system contains the following five root keys:
- HKEY_CURRENT_USER
- HKEY_HKEY_USERS
- HKEY_LOCAL_MACHINE
- HKEY_CLASSES_ROOT
- HKEY_CURRENT_CONFIG
In layman’s terms, any software installation, process execution, and configuration changes cannot be completed without a registry value change. A legit target to take control and create new sets of keys and values in the registry
In the case of offline analysis, isolated environment, you need to access the registry backup files to access the same registry sets.
These are located in the C:\Windows\System32\Config directory and are
- DEFAULT (mounted on HKEY_USERS\DEFAULT)
- SAM (mounted on HKEY_LOCAL_MACHINE\SAM)
- SECURITY (mounted on HKEY_LOCAL_MACHINE\Security)
- SOFTWARE (mounted on HKEY_LOCAL_MACHINE\Software)
- SYSTEM (mounted on HKEY_LOCAL_MACHINE\System)
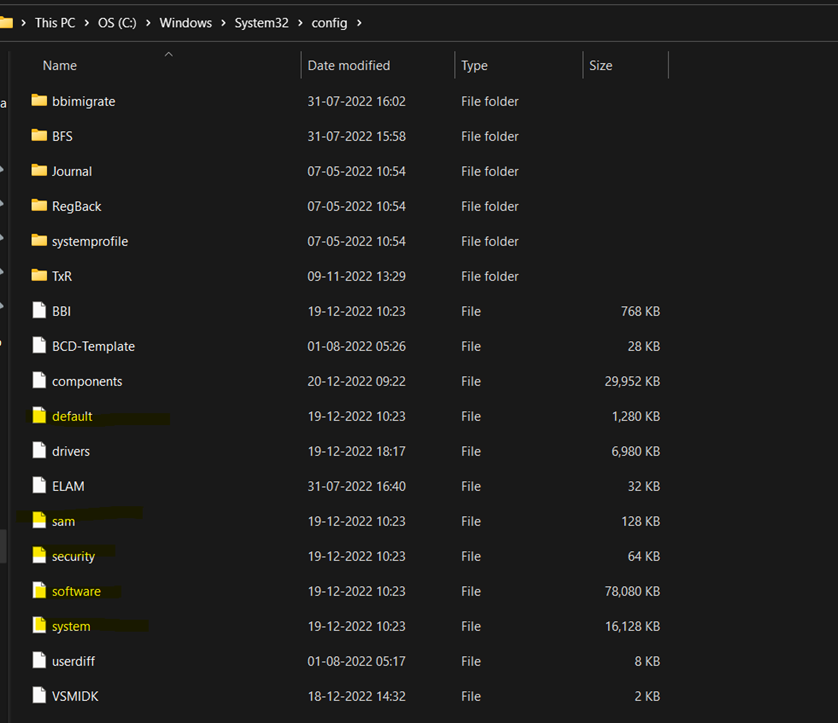
These are standard and updated logs that contain the details of registry keys and values. Apart from these files forensic analysts lookout for the user log data, application data, registry transaction, and backup logs.
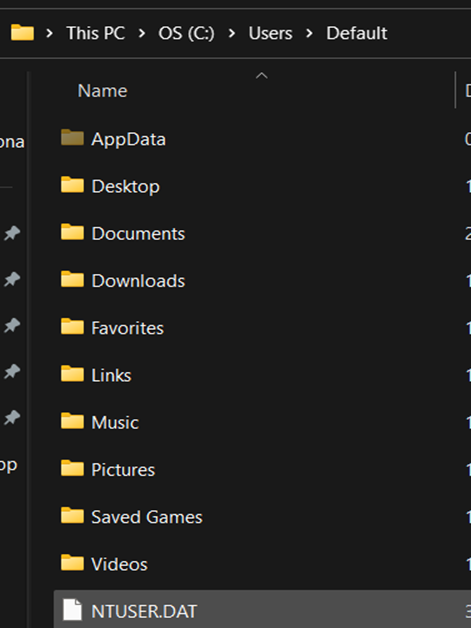
- NTUSER.DAT (mounted on HKEY_CURRENT_USER when a user logs in)
The NTUSER.DAT hive is located in the directory C:\Users\<username>\.
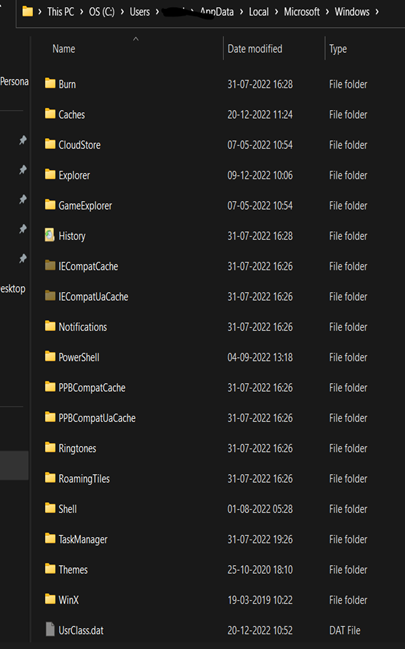
- USRCLASS.DAT (mounted on HKEY_CURRENT_USER\Software\CLASSES). The USRCLASS.DAT hive is located in the directory C:\Users\<username>\AppData\Local\Microsoft\Windows.
- AmCache hive is located in C:\Windows\AppCompat\Programs\Amcache.hve. Windows creates this hive to save information on programs that were recently run on the system.
These files won’t change often but there are files that change regularly and are overwritten which works as backup and transaction logs. These logs are helpful while investigating and tracking all the changes and timelines of change.
The transaction log for each hive is stored as a .LOG file in the same directory as the hive itself. It has the same name as the registry hive, but the extension is .LOG.
Registry backups are located in the C:\Windows\System32\Config\RegBack directory and are updated every ten days.
While it’s easy to know about these files and understand that they are important but accessing these files from isolated images for analysis is not direct. We have some open-source and professional forensic tools for registry analysis like RegRipper and Registry viewer.
Once we get access to registry data, we need to check the standard system information and default users of the system.
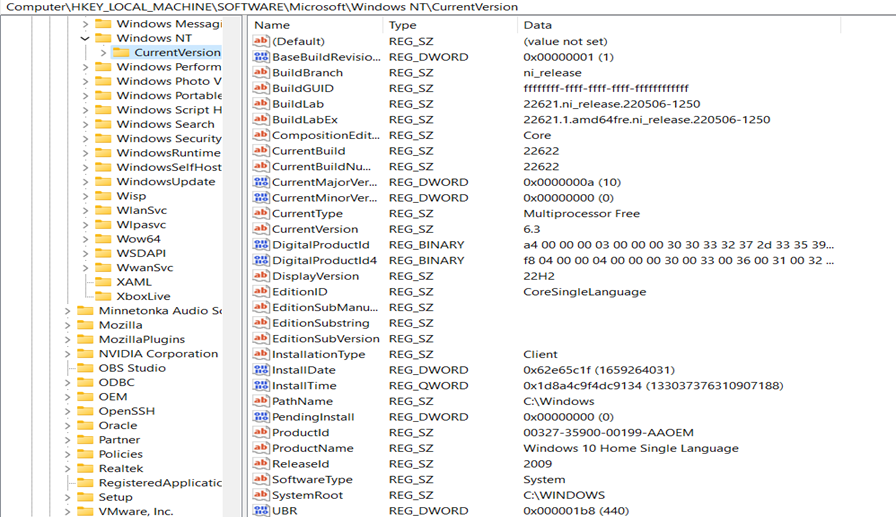
Standard information like OS type and the build number is available in this set. Then we proceed for the system to know any additional information about users, hardware, network, and other information.
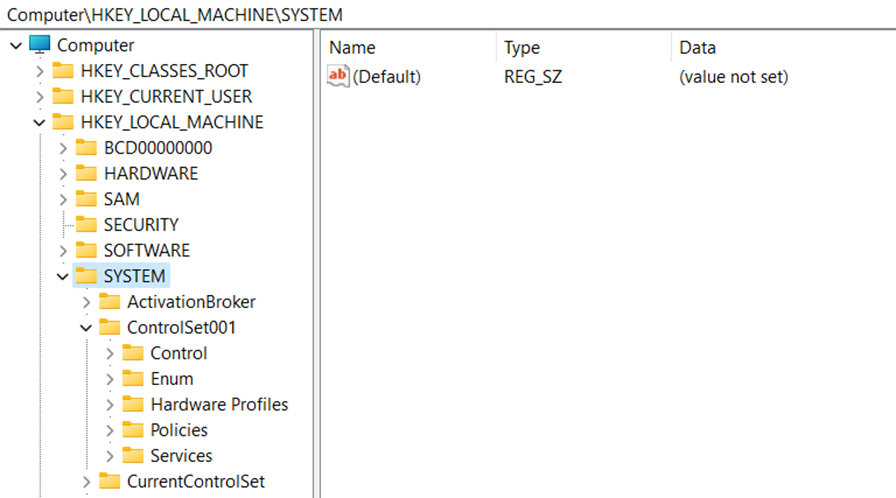
Under the system tab, we have a key named “ControlSet”, a config file in windows with all the details of the machine. The value gets updated or a new file is created when a new configuration is generated and acts as a snapshot.
We can explore this to extract key information for reporting and other sensitive information required.
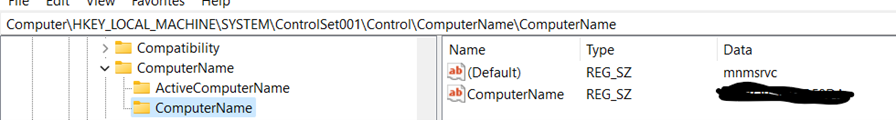
Computer Name
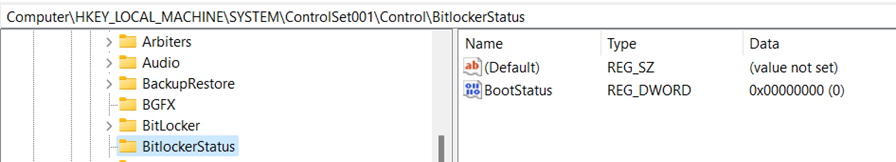
Bitlocker Encryption
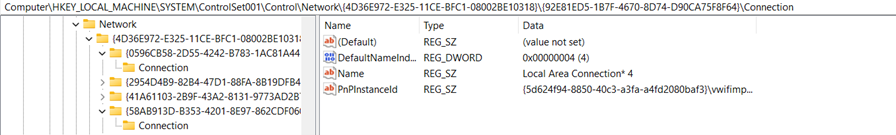
Network Interfaces and past connectivity status
Services
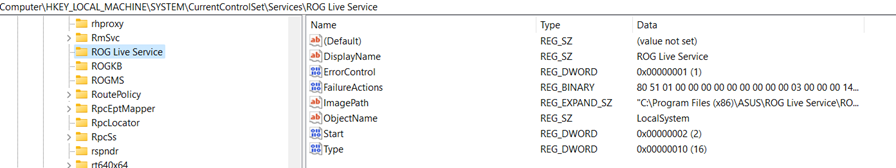
In the registry key, if the start key is set to 0x02, this means that this service will start at boot.
User/Profile Information
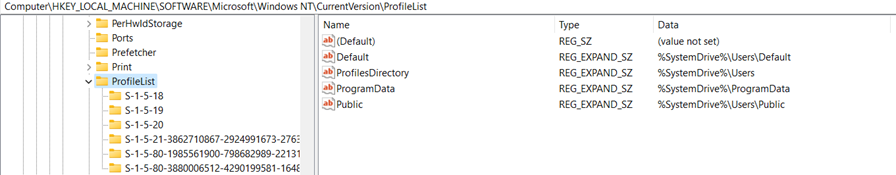
Once we complete exploring such information, it’s important for us to know the recent files and process executed.
On many occasions, these data will be cleared to clear off traces but registry transaction logs can help us to identify this information or retrieve it. But since it’s not in human-readable format, we need tools like Registry explorer to view them.
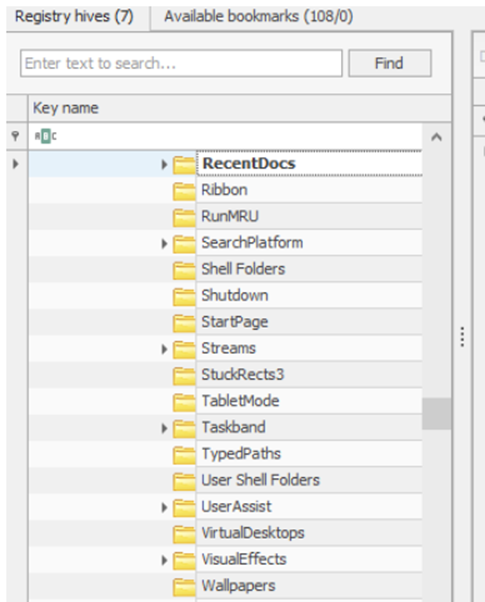
Windows keeps track of applications launched by the user using Windows Explorer for statistical purposes in the User Assist registry keys. These keys contain information about the programs launched, the time of their launch, and the number of times they were executed. However, programs that were run using the command line can’t be found in the User Assist keys
I can able to extract the USB connection history to understand if there are malicious devices like Rubberducky or any other spoofing tools have been inserted into the machine.
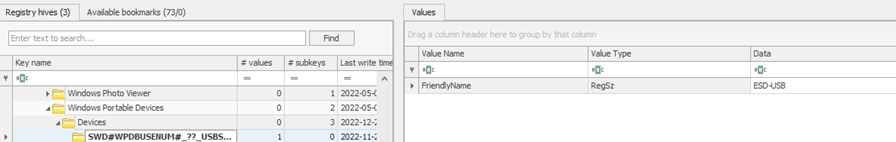
These are some of the ways, we can extract the information from the registry which are not available in the system information.
Thanks for reading. In our next article, we will explore how we can extract executed information, and recover deleted files using tools like Autopsy.








