Cybersecurity is no longer a binary combination i.e., Red Team or Blue Team frameworks. Attack types and threats are increasing year-on-year and security teams need to keep updated about newer tactics, techniques, and procedures on how attackers target.
But with a vast amount of information, it’s not easy for security analysts to keep tests and track of each TTP. That’s where certain frameworks come into play.
In simple words, frameworks are just combinations of these TTPs to demonstrate certain attacks. In this article, we will understand a framework called the Atomic Red team framework, a framework developed from the perspective of a Blue team member.
What is the Atomic Red Team Framework?
Atomic Red Team is an open-source project that provides a framework for performing security testing and threat emulation. It consists of tools and techniques that can be used to simulate various types of attacks and security threats, such as malware, phishing attacks, and network compromise.
This framework can help security professionals assess the effectiveness of their organization’s security controls and incident response processes and identify areas for improvement.
The Atomic Red Team framework is designed to be modular and flexible, allowing security professionals to select the tactics and techniques most relevant to their testing needs. You can use this with other frameworks, such as the MITRE ATT&CK framework.
The beauty of this framework is that it is compatible and can be deployed on any platform like Windows, Linux, and local deployment or cloud deployment.
But how does this atomic work?
To replicate the threat activity, the triggers will be executed from a process called executors. These vary from platform to platform and sometimes manual processes are also used as triggers. Ex: cmd.exe, /bin/bash, powershell.exe, etc.
Before seeing Executors in action, let’s understand the details inside an Atomic.
Atomics refers to different testing techniques based on the MITRE ATT&CK Framework. Each works as a standalone testing mock-up that Security Analysts can use to emulate a specific Technique
Each Atomic typically contains two files, both of which are named by their MITRE ATT&CK Technique ID:
- Markdown File (.md) – Contains all the information about the technique, the supported platform, Executor, GUID, and commands to be executed.
- YAML File (.yaml) – Configuration used by frameworks, such as Invoke-Atomic and Atomic-Operator, to do the exact emulation of the technique
How to launch Atomic Red Team
First, you have to download the Atomic Red Team repo from GitHub. Once you download this is what the structure looks like.
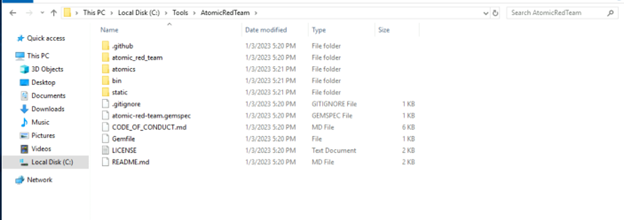
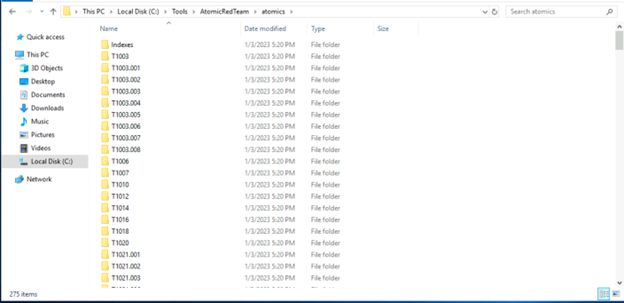
The Atomic Red team can be accessed using the cmd line. If you are using Powershell, you can invoke the module by using the command Invoke-AtomicRedTeam
Open a PowerShell window with ExecutionPolicy set to bypass all security warning prompts while loading the module.
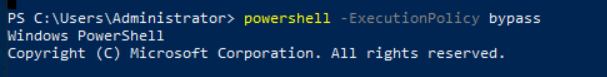
Then execute the command Invoke-AtomicRedTeam:
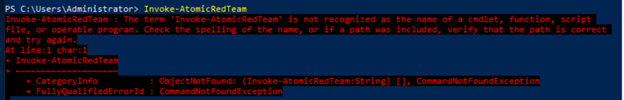
The above error shows that PowerShell is unable to invoke the module by default. Hence you have to invoke it manually by navigating to the folder.
Navigate to the path in the below screenshot and execute the PS script to invoke the framework.
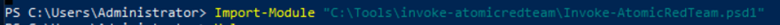
We have successfully imported the module. Now we will try to invoke the framework again.
You can use the Invoke-AtomicTest function to run an atomic test on the system where you installed Atomic Red Team (Local), or on a remote machine through a PowerShell Remoting session (Remote).
We have invoked the atomic test module for our testing purpose and checked an atomic to see what we can do.
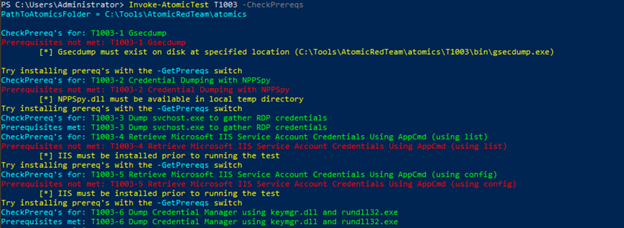
This seems so confusing and blank, right? So this framework gives us the option to check the details before execution so that we are aware of what we are going to execute.
Let’s use the help command and see what commands we can execute
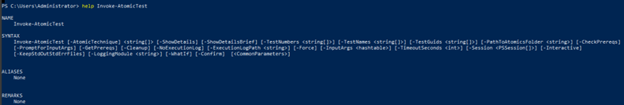
Let’s use ShowDetailsBrief. ShowDetailsBrief is a command that can give us brief details on what will be the steps of the module.
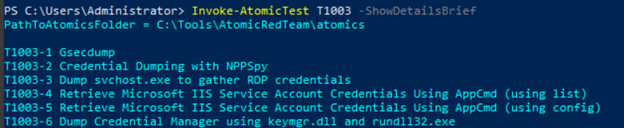
This is how you can check and execute the tests along with exporting the logs.
The Atomic Red Team framework is closely connected with MITRE ATT&CK, resulting in each Atomic being created for a specific MITRE Technique. To reflect this link, each Atomic’s filename is named after its corresponding MITRE Technique ID.
You can correlate existing atomic and create new atomic with the help of the ATT&CK framework.
MITRE GitHub page has something called Attack Navigator which can help you to identify patterns.
For demonstration purposes, I’ll take a threat group called admin@338. Once you select the threat group using the search box, you can see the tactics highlighted in blue boxes.
In every stage, you can see different approaches with IDs mentioned once you roll over the module.
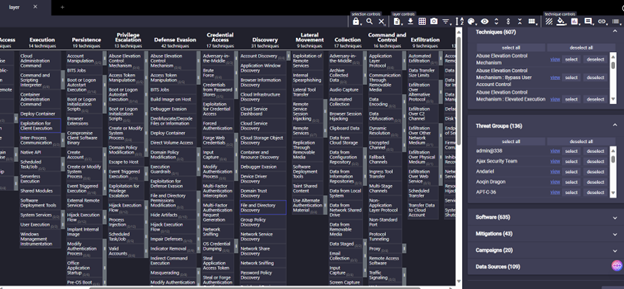
This is just an example, you can use this ATT&CK framework to create new custom atomics for your framework or reverse map your atomics to this mitre framework and make changes as per your requirement.
You can also expand the sub-techniques, remediations, software, and many other options given by the MITRE on this page.
The threat Emulation Frameworks such as the Atomic Red Team is commonly viewed as a tool only for Red Teamers, yet being knowledgeable about it may aid in learning how threat actors do the job.
By connecting with MITRE Framework it will be useful for security analysts to review the preventions or remediations performed for certain threats in your environment and reverse analysis of the activities.








