How to do IAM forensics
Written By: Ricoh Danielson
IAM forensics is a branch of forensics pertaining to digital identity, the practice of creating accurate digital identities and accounts, and the data that is associated with them. Whether it’s for an external company (you) to acquire good actors or a pentester performing post-exploitation, IAM forensics can be a powerful tool in your arsenal. This guide will provide the basics required to perform and interpret IAM forensic analysis using open source tools and resources.
Understanding the importance of how to IAM forensics
When it comes to identity access management (IAM) forensics is either a matter of conducting it manually or tactically and technically. If you’re using tools such as guard duty or IAM or some sort of privilege access management tool this will help you to arrive at the conclusion faster. If you ever do it a manual way such as unchain the group policies and also understanding the different privileges that users have, this may take a little bit longer. Both are crucial for understanding and conducting during an investigation.
Technical Requirements
Identity access management in forensics and discovery requires a few different tools and methodologies. This article will discuss how to do it in AWS and at the Group Policy Objects (GPO) level. Again, both are perspectives that we commonly use inside security to understand how to read actors navigate a raised privilege.
Was it possible to stand what groups the threat actor is targeting? We can then decipher where the threat actor might be heading and cut them off by getting ahead of the power curb.
If you can run a power shell command script to export all GPO settings as well as all AWS policy configurations in advance, this will help with the aspect of data preservation of the investigation.
IAM AWS technical review:
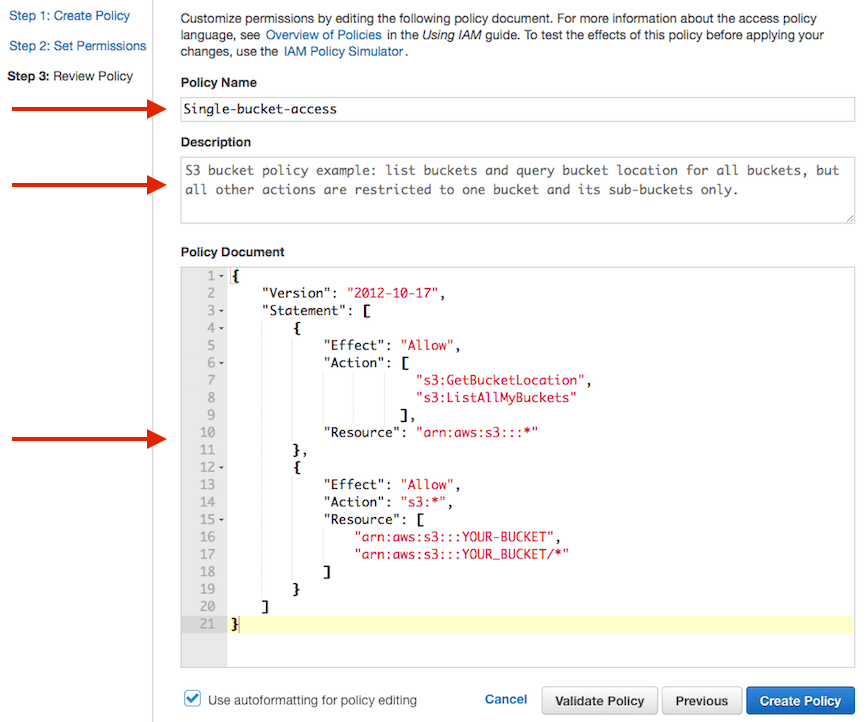
With AWS IAM manager from a technical policy perspective, we can see that there is a breakdown of the actions and resources available to each line item. On exhibit one we will see that there are certain allowed accesses to certain buckets. Having said that, this means that users can access certain things. From an Investigation perspective, this gives a lot of information to the researcher on where and how the director can leverage this policy to gain access to other areas.
If the threat actor can leverage certain aspects to gain access, then they can gain access possibly to the entire environment.

IAM from a manual perspective:

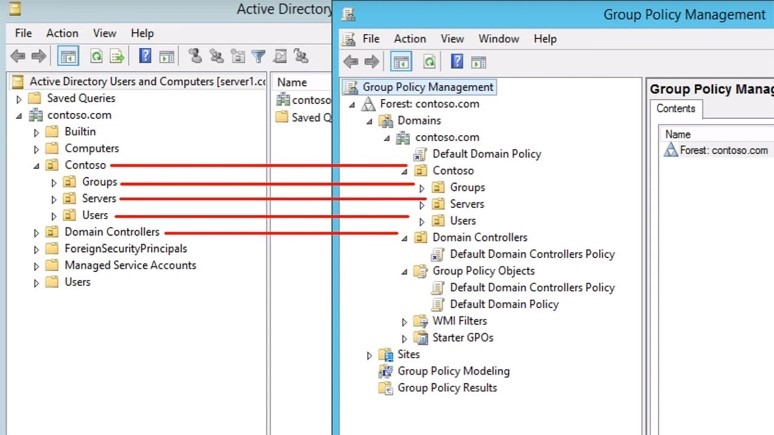
Now we have to roll our sleeves up and do this manually. There are many investigations there have been times where we had to roll up our sleeves and jump into the active directories Area to determine diverse groups, users, and privileges in which these users head. As we can see in the exhibition, system administrators follow a simple process that is quickly bypassed by threat actors.
Analyzing findings and data element:
When conducting an analysis, it is very important to fully understand which groups must have administrative rights in relation to non-administrative rights. I thought hackers would leverage any opportunity to gain a higher level of elevation privileges. That is why this is where security group management and scope creep need to be well managed. I know it sounds boring, but in the same aspect I need to have an ongoing audit of them to make sure there are enough security safeguards around them. As can be seen above, users are simply thrown into a user group with hopes and prayers. It’s a great playground for thread actors to harvest their credentials and also make lateral movements with the escalation of privileges. A playground for threat actors.
Why are we choosing manual process over tools might be a good idea
No matter how you cut it up, whether you use a tool to conduct identity access management to understand privilege access management or have to do it the old-fashioned way via command line, there is no wrong answer. Both are necessary during the investigation in a highly sought-after skill set that is needed to mitigate the threat actor.
When it comes to data preservation, it must also ensure that we can keep these groups to convey the story needed for the investigation. Sometimes we can use screenshots, imaging devices, and active directories, which are always useful and sometimes we have to export group and party use. There will be another through the command line or through the use of a tool. Either way, there is no wrong answer.
Summary
IAM forensics will allow you to discover more about what an account is doing, where the requests are originating from, and how attackers gained access. The first thing to do is to break down the network out the WAN and back in again through your updated IAM infrastructure. Look at accounting logs and query data. Look at session creation, authentication, and authorization. Check to see if any of your permissions were misconfigured. Once you have collected all of your logs and data points you should be able to verify that you blocked an intrusion attempt properly, or just see where an attacker was trying to get into your environment.
So, now that we have a good idea of how to conduct IAM Forensics by using a tool or an application, we can now move forward in understanding how these things play critical points in an investigation. When conducting threat hunts or incident response activities, understanding the different GPO policies and roles as well as the differing identity access management policies will help you determine where the threat actor will likely go and what they may attempt. More than likely, the threat actor tries to gain more administrative access for lateral movement to continue their attacks. Remember that even in identity access management forensics incident response, you are the first responder.








