How to Conduct IOC (Indicators of Compromise) Threat Hunting during a War
Post Credit: Ricoh Danielson
IOC Threat Hunting is about hunting down cyber-threats in the wild. This means that IOC threat hunters are on the lookout for suspicious activity in live data feeds. While performing IOC Threat Hunting, cyber threat hunters go through many servers, IP addresses and URLs to try and uncover threats. When analyzing IOC Threat Hunting results from a particular dataset, or set of data feeds, it will be very important to note the context of each IOC Hunt result.
These days, threat hunting has become so complex that it needs to be a collaborative effort between attack-minded security analysts, SIEM, and other security technologies. However, this doesn’t mean that IOCs are any less important. Indicators of compromise (IOCs) or indicators of presence (IOPs) are artifacts, activities, behaviors, or design elements present on a system that could be attributed to an adversary. There are various indicators which can help an analyst move from detection of malware infection to analysis of the malware.
In a war, understanding how to hunt an Indicator of Compromise is crucial
While there is a crisis in the world, war going on, and battles being conducted on the streets of other countries, there would always be cyber threat actor groups continuing their efforts to cause damage. It is critically important to keep an eye on the ball and not get detoured or distracted from a foreign Country conflict. This is an excellent opportunity for many threat actors to deploy their tactics and techniques to either steal information, cause damage, or even some cases, cause loss of life. Our responsibility is to ensure our companies, our people, and our businesses can combat these. The question is what we do for and where do we start.
Technical Requirements for conducting Indicators of Compromise Threat Hunting on a Warfront
For the best interest of this article, let’s assume that you have some SEIM or an ability to search items of enjoyable in your environment. This can be a tool such as Splunk, Q radar, or even as essential as velociraptor. As we see foreign connections from our Network calling out to areas of interest such as Russia, Ukraine, Belarus, and Chechnya or other known three warring states, here are some IOCs to take into consideration.
| User | Connecting IP | Date (GTM+3) |
| root | 89.163.249.244 | Wed Nov 10 14:11 – gone no logout |
| root | 107.189.31.241 | Wed Nov 10 09:09 – 09:10 (00:01) |
| root | 185.220.103.5 | Mon Oct 25 15:08 – 15:50 (00:42) |
| root | 192.42.116.25 | Fri Oct 15 20:25 – 20:28 (00:03) |
| root | 18.27.197.252 | Mon Oct 4 17:47 – 17:47 (00:00) |
| root | 45.153.160.134 | Mon Sep 27 14:12 – 14:18 (00:05) |
| root | 185.220.103.4 | Mon Sep 27 09:10 – 09:13 (00:03) |
| root | 185.130.44.108 | Thu Sep 23 21:08 – 21:26 (00:18) |
| root | 104.244.76.44 | Thu Sep 23 08:04 – 08:04 (00:00) |
| root | 104.244.76.44 | Thu Sep 23 08:01 – 13:02 (05:01) |
| root | 64.113.32.29 | Wed Sep 22 13:46 – 15:40 (1+01:54) |
| root | 54.36.108.162 | Wed Sep 22 12:54 – 13:10 (00:16) |
As we peel back the onion on this, we will see that there are also other TCP connections to Conti servers
| Detected TCP Connections on Conti Server |
| 1.177.172.158 |
| 104.244.76.44 |
| 122.51.149.86 |
| 176.9.1.211 |
| 176.9.98.228 |
| 18.27.197.252 |
| 185.130.44.108 |
| 185.220.103.4 |
| 2.82.175.32 |
| 217.160.251.63 |
| 218.92.0.211 |
| 45.153.160.134 |
| 46.101.236.25 |
| 49.234.143.71 |
| 51.75.171.136 |
| 54.36.108.162 |
| 6.11.76.81 |
| 61.177.172.158 |
| 64.113.32.29 |
| 66.211.197.38 |
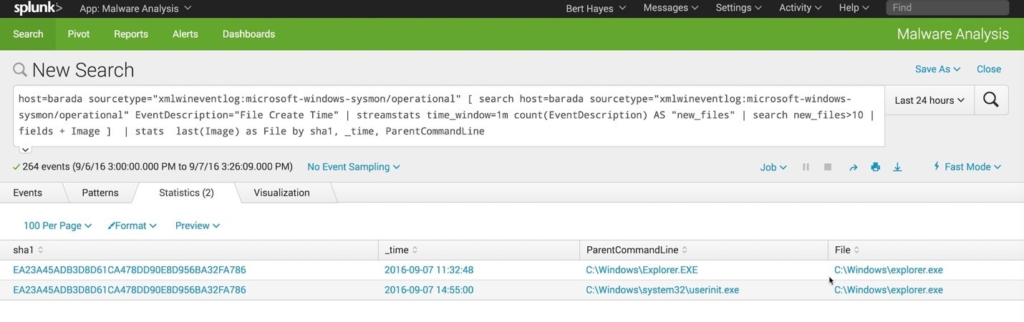
Here are some stings to help us using SPLUNK
sourcetype=”xmlwineventlog:microsoft-windows-sysmon/operational” EventDescription=”File Create Time”
| streamstats time_window=1m count(EventDescription) AS “new_files”
| search new_files>10
Diesel produce SHA Values that we can lookup and search as well.
EA23A45ADB3D8D61CA478DD90E8D956BA32FA786
When choosing between tools and manual processes, there can be good reasons to do so
There is no right or wrong answer when it comes to threat hunting, either done manually or from an automator perspective. It all comes down to time, money, labor, and resources. Some organizations have more money than others and some organizations have more labor resources than others. On the other hand, there’s something to be said about having an automated process. This will expedite the time spent on discovery and investigation and can possibly lead to a faster result in shorter amount matter time.
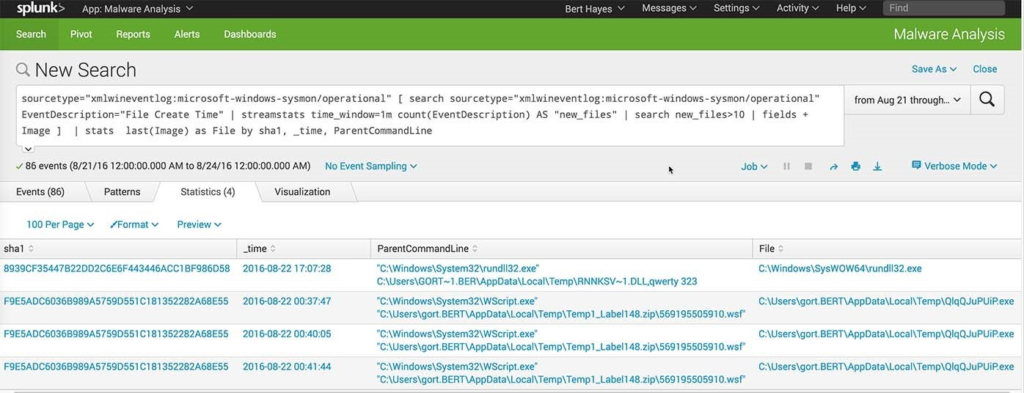
Here is what a manual process might look like when running PowerShell scripts and or command line forensics for artifact finding:
sourcetype=”xmlwineventlog:microsoft-windows-sysmon/operational”
[ search sourcetype=”xmlwineventlog:microsoft-windows-sysmon/operational” EventDescription=”File Create Time”
| streamstats time_window=1m count(EventDescription) AS “new_files”
| search new_files>10 | fields + Image ]
| stats last(Image) as File by sha1, _time, ParentCommandLine
Here is what a tool output might look like:
Both findings are of great value. However, the question is what we do with these findings. Where does he need to go, what team needs to digest us and what does this really mean to the overall investigation?
Data analysis for a live, digital, active IR hunt or investigation
As we searched through all the analysis findings, we will determine the values, timestamps, pathways and executables that were used to conduct this exploit. Now that we have the information the underlying question would be where it needs to go. Usually, the sharing of these indicators of compromise along with artifacts are greatly used throughout the cyber security community to help each other out. However, keep in mind that sharing information may be an intellectual property information issue. Check with your legal and privacy before sharing any indicators of compromise.
Conclusion
IOC hunting is the art of finding evidence of a cyber attack to triage the level of damage and build a forensics case. It is possible to do it alone, but an effective IOC hunt should involve collaboration from the team that is able to respond to the incident from all three phases: prevention, detection, and response.
The IOC is a proven methodology that has been guiding threat intelligence efforts for many years. There is no wrong way of searching for indicators of compromise during a war time event. Many threat actors are going to use their techniques and tactics delivered any type of attack they can either on the war-torn country or the current country, it is critically important to understand how these threat actors’ work. Remember, in cyber security and more specifically an incident response you are your own first responder.








