According to a report published by a cybersecurity vendor, there were around 450,000,000 brute force attacks happening every day in 2021. With the increase in remote work with newly onboarded employees with less security awareness knowledge and lazy, relaxed controls to monitor making the users most vulnerable to attacks. The majority of these attacks are RDP, and SSH access controls for gaining access to systems and elevating to high-level access or creating a C2C server.
RDP, SSH are types of user authentications into the machines. In windows, there any many other authentication services such as Kerberos authentication.
What is Kerberos Authentication?
Kerberos is an authentication protocol used to verify the identity of the user. It acts like a trusted medium to connect multiple sources by verifying the authentication. It uses secret-key cryptography mechanism for this process.
Kerberos is a network level authentication process used in major Microsoft Operating systems implemented in process of authenticating services like SMTP, AD etc. It’s an alternative service to SSH and POP.
How does Kerberos Authentication works?
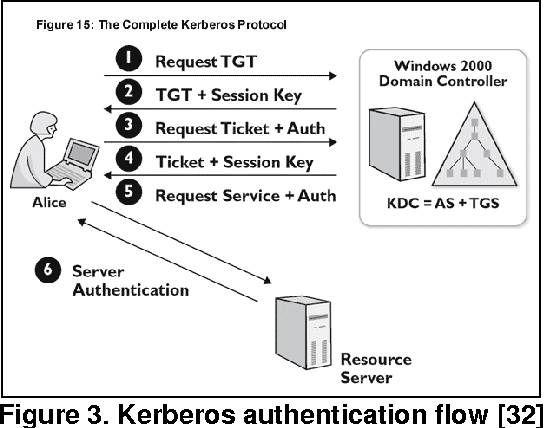
Kerberos Authentication is similar to TLS handshake in one way or the other. Workflow consists of Client, Server and KDC.
This is how the process of Kerberos workflow work
Here are the principal entities involved in the typical Kerberos workflow:
- Client: Client is host or the user trying to access a service
- Server: Server refers to application service or gateway hosting the service
- Key Distribution Center (KDC): In a Kerberos environment, the authentication server logically separated into three parts: A database (db), the Authentication Server (AS), and the Ticket Granting Server (TGS). These three parts, in turn, exist in a single server called the Key Distribution Center
- Ticket Granting Server (TGS): The TGS is an application server that issues service tickets as a service.
- Authentication Server (AS): The AS manages the client authentication. If the authentication is successful , the AS issues the client a ticket called TGT (Ticket Granting Ticket).
When a user enters the password and sends the request:
- The user asks for a access request from AS. Once the request receives to KDC, KDC verifies the client’s credentials.
- The AS checks their database for the client and TGS’s availability. If the AS finds matches both values, it generates a client/user secret key, used to create a session key (SK1) encrypted by the client/user secret key.
- The AS then generates a TGT containing the client ID, client network address, timestamp, lifetime, and Session Key. The TGS secret key then encrypts the ticket.
- The KDC creates a ticket for the file server using the client ticket. The TGS then uses the TGS secret key to decrypt the TGT received from the client and extracts the SK1.
- The TGS decrypts the authenticator and checks to see if it matches the client ID and client network address.
- Then the KDC generates a service session key (SK2) that is shared between the client and the target server.
- Finally, the KDC creates a service ticket that includes the client id, client network address, timestamp, and SK2.The client uses the file ticket to authenticate.
- The target server receives the relevant tickets and SK. The server uses SK2 to decrypt the authenticator and validate the source details.
Bruteforcing Kerberos Pre-Auth using Kerbrute
Kerberos is a tool used to bruteforce and enumerate Active Directory accounts through Kerberos Pre-Authentication. Its an opensource tool used with CLI.
Bruteforcing Kerberos pre-auth is pretty easy and convenient because it doest not throw the default windows failed login attempt “ An account failed to log on” , event ID 4625.
Usage of Kerberos:
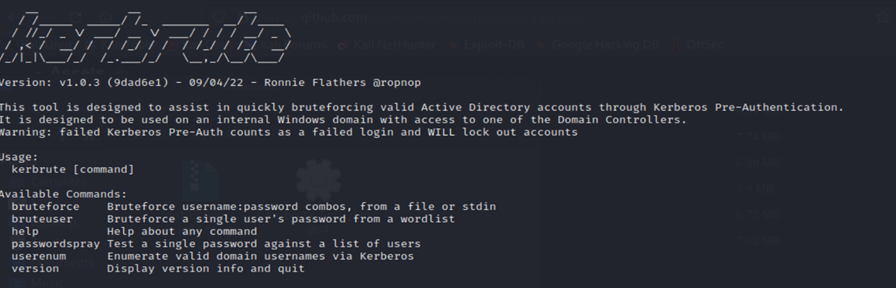
Kerbrute has four main commands:
- bruteuser – Bruteforce a single user’s password from a wordlist
- bruteforce – Read username:password combos from a file or stdin and test them
- passwordspray – Test a single password against a list of users
- userenum – Enumerate valid domain usernames via Kerberos
Let’s understand use of each command.
- Brute User:
Bruteforcing account using username. Usage of this command is only recommended for no lockout policy.
This will generate both event IDs
- 4768 – A Kerberos authentication ticket (TGT) was requested.
- 4771 – Kerberos pre-authentication failed
- Brute Force:
This mode is a traditional Brute foce method from a file with Kerberos PreAuthentication. This will generate both event IDs
- 4768 – A Kerberos authentication ticket (TGT) was requested
- 4771 – Kerberos pre-authentication failed
- Password Spray:
With passwordspray, Kerbrute will perform a brute force attack against a list of domain users
This will generate both event IDs
- 4768 – A Kerberos authentication ticket (TGT) was requested
- 4771 – Kerberos pre-authentication failed
- User Enumeration:
To enumerate usernames, Kerbrute sends TGT requests with no pre-authentication. If the KDC responds with a PRINCIPAL UNKNOWN error, the username does not exist. However, if the KDC prompts for pre-authentication, we know the username exists and we move on.
This does not cause any login failures so it will not lock out any accounts. This generates a Windows event ID 4768 if Kerberos logging is enabled.
Why preventing Kerberos is important
- Having access to kerberos means having control to manage existing sessions, create new sessions.
- If you have local admin or domain admin access in Active Directory, you have ability to create new session tickets with tickets without expiry.
- Kerberos database have usernames, hashes details which can be used for bruteforcing at later stage.








