In the vast landscape of cyber threats, one name keeps cropping up: Kimsuky. This APT has been involved in an ongoing cyber campaign that has targeted South Korean think tanks, government organizations, and human rights activists. They use a highly sophisticated reconnaissance toolkit to gather valuable information and exploit vulnerabilities. But the most important questions for cybersecurity pros: who are they? How do they operate? Should I be worried? Let’s find out.
What is Kimsuky?
Kimsuky, also known as Black Banshee or Thallium, is a suspected state-sponsored advanced persistent threat (APT) group in North Korea, home to some of the world’s most advanced threat actors. They primarily focus on cyber espionage activities and have a particular interest in targeting entities associated with South Korea. The group is notorious for its tailored attacks and advanced techniques, which are constantly evolving to evade detection and maintain persistence.
Who is Kimsky targeting?
Kimsuky’s primary targets include South Korean think tanks, government organizations, and human rights activists. These entities possess valuable intellectual property, sensitive government information, and insights into political affairs, making them attractive targets for cyber espionage. By compromising these targets, Kimsuky aims to gain a strategic advantage, obtain confidential data, or gather intelligence to support its objectives.
How does Kimsuky operate?
As we can expect from a nation-state attacker, Kimsuky has sophisticated and multifaceted approach. But, unlike many groups, we don’t find quite as much variety as we’d expect. Here are a few “calling card” signs for the Kimsuky threat group:
- One of the key tactics employed by Kimsuky is a tailored spear-phishing campaign. The threat actors craft highly convincing emails that appear to be from trusted sources, such as colleagues or known organizations. These emails are personalized and designed to deceive the recipients into opening malicious attachments or clicking on malicious links.
- Once inside the target’s system, Kimsuky leverages known software vulnerabilities to gain further access and establish persistence. The group maintains an arsenal of zero-day exploits and carefully selects the vulnerabilities they exploit to evade detection. They actively monitor and exploit weaknesses in popular software, including Microsoft Office, Adobe Flash Player, and Internet Explorer, to compromise systems and maintain a foothold.
- Central to Kimsuky’s cyber campaign is their sophisticated reconnaissance toolkit. This toolkit allows the threat actors to gather critical information about their targets, such as email credentials, sensitive documents, and network architecture. The toolkit comprises various components, including keyloggers, screen capture tools, and network reconnaissance utilities. These tools enable Kimsuky to conduct extensive surveillance, reconnaissance, and information gathering within the compromised systems.
What tactics and techniques have Kimsuky used?
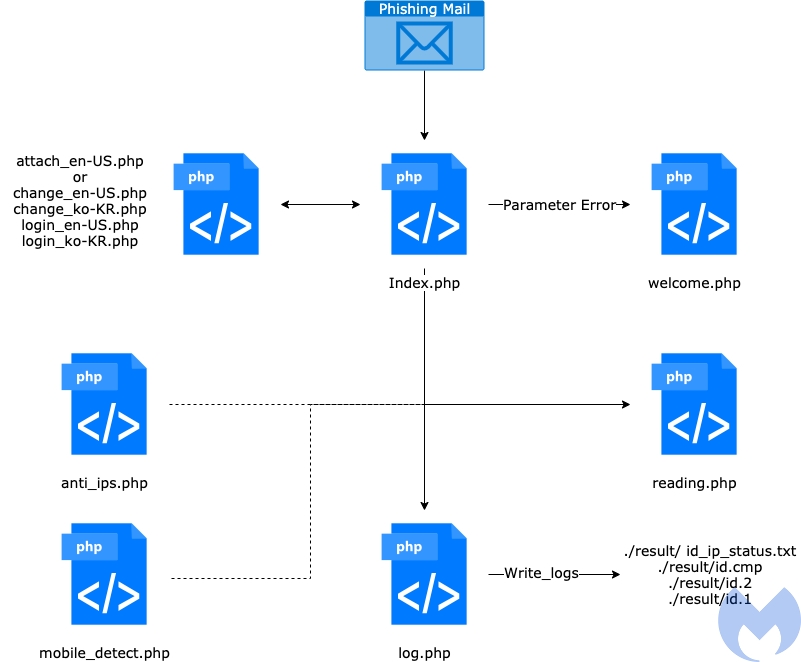
Kimsuky constantly adapts and refines its tactics and techniques to stay ahead of security measures. They employ anti-analysis techniques to hinder detection by security tools and implement multi-stage malware delivery mechanisms to ensure persistence. The group also leverages social engineering techniques to manipulate victims and lure them into interacting with malicious content. By continuously evolving their methods, Kimsuky poses an ongoing threat to targeted entities.
Here is a list of MITRE ATT&CK codes for understanding the Kimsuky approach:
- Spear-Phishing Campaigns (T1566.001): Kimsuky utilizes tailored spear-phishing emails to target their victims. By crafting convincing emails that appear to be from trusted sources, they lure individuals into opening malicious attachments or clicking on malicious links.
- Exploitation of Software Vulnerabilities (T1203): Once the initial access is gained, Kimsuky leverages known software vulnerabilities to exploit systems and establish persistence.
- Credential Theft (T1555): Kimsuky employs various methods to steal credentials from compromised systems. This can include keylogging, where they capture keystrokes to gather usernames and passwords.
- Execution (TA0002): Kimsuky is also known for using BabyShark malware and PowerShell or the Windows Command Shell for Execution.
- Screen Capture (T1113): As part of their reconnaissance activities, Kimsuky employs screen capture tools to capture screenshots of targeted systems.
- Network Reconnaissance (T1018): Kimsuky conducts network reconnaissance to gather information about the compromised network, including network architecture, available services, and potential avenues for lateral movement.
- Anti-Analysis Techniques (T1497): To evade detection, Kimsuky employs anti-analysis techniques that hinder the efforts of security researchers and tools to understand their malware and activities.
- Social Engineering (T1484): Kimsuky leverages social engineering techniques to manipulate victims and increase the success rate of their phishing campaigns.
How do I deal with Kimsuky?
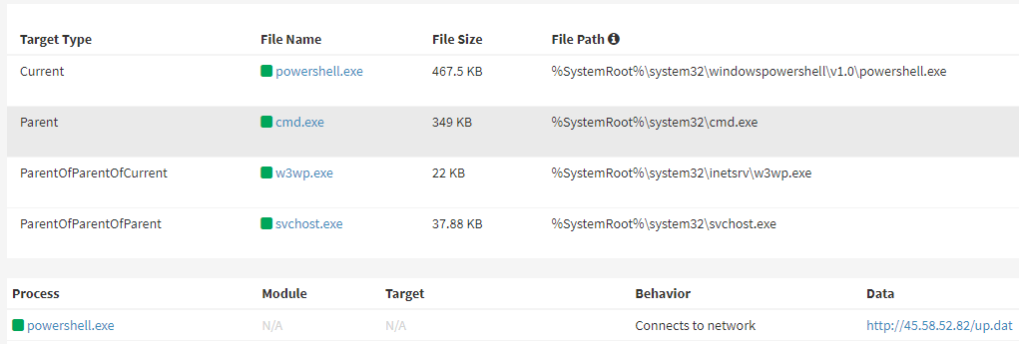
Given the persistent and evolving nature of the Kimsuky campaign, organizations must implement robust security measures to protect themselves. This includes regular patching and updating of software to mitigate known vulnerabilities. Security awareness training can help educate employees about the dangers of phishing attacks and teach them to identify suspicious emails. Implementing multi-factor authentication and network segmentation can add additional layers of security. Furthermore, deploying advanced threat detection and response solutions can help identify and mitigate potential intrusions promptly.
To effectively mitigate the Kimsuky threat and similar APT campaigns, organizations must prioritize robust cybersecurity measures. This includes implementing proactive security practices such as regular software patching and updates to address known vulnerabilities. By keeping systems up to date, organizations can significantly reduce the attack surface and minimize the risk of exploitation.
Additionally, educating employees about the risks associated with phishing attacks and implementing comprehensive security awareness training is crucial. Employees should be trained to recognize and report suspicious emails or other potentially malicious activities. By fostering a security-conscious culture, organizations can empower their workforce to become the first line of defense against cyber threats.
Implementing multi-factor authentication (MFA) can add an extra layer of protection to critical systems and accounts. By requiring multiple factors for authentication, such as passwords, biometrics, or hardware tokens, organizations can significantly enhance their security posture and reduce the risk of unauthorized access.
Network segmentation is another effective strategy to mitigate the impact of a potential breach. By dividing networks into distinct segments and applying strict access controls, organizations can limit lateral movement within their infrastructure. This approach helps contain and isolate potential compromises, preventing an attacker from accessing sensitive data or critical systems.








