SecPro Explainer: Linux Security & Hardening
Post credit: Merlyn Shelley
Linux systems have a large module of components that are deliberately designed to provide extreme capabilities. This also means that there could be many loose ends that have to be taken care of in the aspect of security. Remember when the system gets more and more complex, then the security measures would also get increasingly complex!
Generally, we call them the “Surface” and if the surface is complex then it is susceptible to more attacks. And the uniqueness of these complex surfaces is that the components would have their own allowances of security. And if a component is compromised to an attack, then it would allow the intruder to go deep into the system.
Before implementing the hardening measures, we need to scan and audit the systems for scrutinizing open vulnerabilities that are prone to attacks. So, let’s hop into how to perform scanning and auditing operations across complex Linux systems.
Auditing Vulnerabilities across Linux Systems
Vulnerabilities occur mostly when the coding standards are not met during the software development stages such as weak configs of applications and if the bug in the code is not resolved properly. Moreover, we cannot always say the system is 100% secure even if we have scrutinized all the programming errands. Only when using the system, we tend to know which part of the source code must be improved and what are the components that are weak in terms of security. So, we need to scan and audit systems regularly to check for new emerging
Conducting Linux Security Audit with Lynis
One of the battle-tested tools for performing security audits on systems that are running on Linux is Lynis. It is free, open-source, and found to be flexible that can be used for different purposes like security auditing, compliance testing (for example PCI, HIPPA, SOx), pentesting, vulnerability detection, and system hardening.
This tool runs with almost no dependencies, it performs extensive scanning customized to every operating system. For instance, if you are using Apache it starts with regular tests related to Apache and if it finds any specifics based on SSL/TLS it runs additional tests tailored to the system security needs.
You can download Lynis from https://cisofy.com/
The best part of using Lynis is you don’t need to install any other additional tools to run the audit. It can be used across any Unix/Unix-like/Linux operating system including macOS. You just will use the common shell script to extract the archive file and run Lynis:
tar xzvf lynis-2.7.5.tar.gz
cd lynis
sudo ./lynis -h
To perform the scanning operation, you need to execute the following command:
sudo lynis audit system
You will get a detailed section on the output about the vulnerable points found across your systems.
You will view a similar screen like this after running your security audit on Lynis that gives you insights on the hardening measures and the errands in your system configurations.

Lynis also comes with an enterprise version that consists of scanning for compliances and so on. You can find their pricing option here.
Now let’s move on to reducing these vulnerabilities.
How to Mitigate Vulnerabilities in Linux Systems?
We have now discovered the vulnerabilities found in our system, so let’s look at ways to reduce or prevent them from posing a greater threat to our entire infrastructure.
Filtering Traffic with a Firewall
While hardening your Linux servers network traffic must be your priority when you’re using cloud infrastructures. You should always filter the unwanted traffic that is coming into your systems.
Ingress filtering is the method of restricting the incoming traffic. That is when there is a suspicious request posing to be from your local network but actually arising from the external internet, then you need to filter all such kinds of traffic. That way you can avoid spoofing attacks.
Egress filtering is about limiting your outgoing traffic. For this, you need to be so sure about the network protocols that are used in your infrastructure. The most commonly used protocols are:
-
HTTP and HTTPS to retrieve updates (port 80/443, TCP, sometimes UDP)
-
DNS traffic to resolve names and IP addresses (port 53, UDP and TCP)
-
Time synchronization (port 123, UDP)
-
Outgoing email (port 25, TCP)
Filtering outgoing traffic greatly helps you in preventing the attacker from downloading malware into your system.
Using Localhost interface is helpful when using network-based services that should not be publicly available. This command “ip addr show lo” will assist you in showing the details of the interface you are using.
Limiting the Installations
One of the best ways to secure your system is not to install tools or software that you don’t use frequently. This is sometimes also called “apply minimal installation.” Here you can also remove the unwanted users in your system as well. This is otherwise called restricting the users based on their roles and usage, ie., role-based access control or removing users when they don’t belong to your system anymore.
Conducting Code Audit
A code audit is to check whether you have used any undeclared variables or unexpected logic while developing your software systems. You can apply Linting or use Lint Tools to check on the source code for any unexpected errors.
Regularly Updating Installed Software
Of course, it is wise to periodically update all the software packages that you have installed in your systems. More importantly, when there is a security update that pops up in your software notification, do it immediately. That way you could seal off the vulnerable points in your systems.
Automating OS security Updates
Configure your systems to upgrade your OS automatically. That way you won’t miss any security update that is coming along with the improvement of your operating systems.
Deleting Unused Software Modules
If you are no longer using a software tool, then delete it for now. If you keep them unnoticed then it would turn out to be a vulnerability that would later cause severe damage to internal components.
Regular Data Backup
One of the major risks of attacks is compromising sensitive data. Always back up all your data regularly to avoid such instances.
Perform regular Audits and Update the Security Patch
And finally, is performing regular security audits and updating the security patch if any. This way you’re adding another shield of protection to your systems.
Now that we have seen ways to mitigate the vulnerable points across Linux systems. We shall look into the quick fixes that are established for the most common issues.
Fixing the most common vulnerabilities and exposure (CVEs)
The effect of vulnerability is basically determined by these factors, such as existence,
The most common vulnerabilities across Linux Kernel are
-
DoS – Denial of Service – CVE-2019-11477
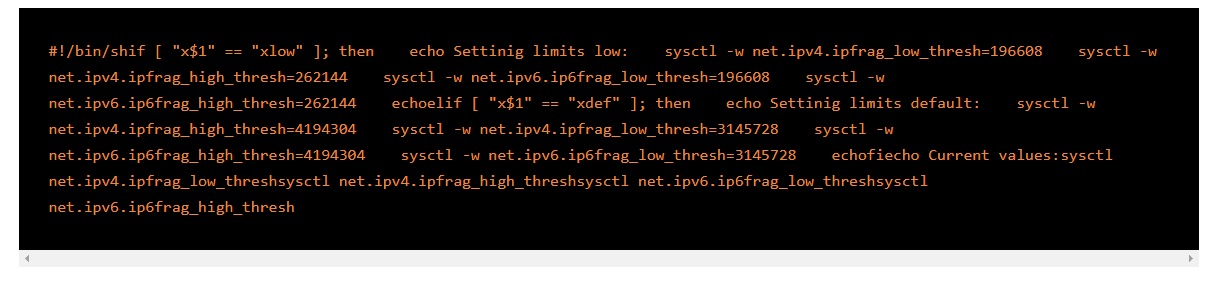
This is called TCP selective acknowledgment (SACK) which is caused by an integer overflow when Linux processing subsystems of the networks. Here the buffer data segment is fragmented and when the Kernel tries to merge them into one, it will lead to the overflow of variables. This is a major vulnerability that could allow malicious SACK requests from intruders that leads to denial of service. To resolve such an attack, you could use the following commands to firewall your network,
-
Memory Corruption – CVE-2017-18017
It is caused due to the failure of Linux Kernels to handle exceptions. This is posing the threat of denial of service, in which hackers would execute the attack remotely. The following code snippet can be used to mitigate such vulnerabilities.

-
SegmentSmack – CVE-2018-5390
This occurs when Kernel handles the crafted TCP packets differently. Hackers would use this flaw remotely to trigger costly calls by sending modified packets through the active TCP sessions. This will lead to a CPU saturation and insufficient bandwidth to support the incoming traffic which therefore again turns to denial of service. The following commands can be used to mitigate such attacks.
That’s about the quick fixes on most common vulnerabilities. Now we shall investigate the list of tips and tricks you can follow while performing Linux security hardening.
Checklist for Hardening your Linux Systems
-
Audit system services with systemctl and network services with netstat
Linux systems with systemd have systemctl
sudo systemctl -t service –state=active
And netstat helps you keep track of all the network services that are running across your system.
netstat -lp -A inet
This way you would know the real time status of all your system and network services.
-
All data communication across the Linux Servers must be encrypted
Whatever data you are exchanging with other devices, do always encrypt them. Tools such as GnuPG, OpenVPN, allow you to encrypt all your data and communication in transit.
-
Restrict the usage of FTP, Telnet, and Rlogin/Rsh services
You can implement OpenSSH, SFTP, or FTPS to add an extra layer of encryption on FTP.
-
Utilize Linux Security Extensions
Use security patches that come alongside the Linux kernel to keep the systems updated. This will rule out any misconfigured programs or compromised programs.
-
Utilize Mandatory Access Control (MAC) such as SELinux
This mandatory access control guards the system against malicious applications that could cause damage to the system. Here you can find the user guide install SELINUX.
-
Enable Strict password protection with GRUB2(Grand Unified Boot Loader) configuration
When your laptop is stolen and you don’t encrypt your hardware, there are chances the thief might boot the laptop in emergency mode to retrieve its stored data. In Linux, the GRUB feature restricts people from editing Kernel and allows only permitted users to access the booting functionalities.
-
Do not allow root login
Always use sudo command to allow other users to login into the system. It has an additional tracking and auditing functionality that protects the system from malicious activities. Never allow root login facility.
-
Enable physical hardware security across the server
You need to configure the BIOS or UEFI chips for booting instruction once the system is powered on. Do not allow booting from external hard drives such as DVDs and CDs as this increases the chances of vulnerabilities. BIOS/UEFI is the most secure way of booting your system and all the production box configurations must be locked in respective Internet Data Centers (IDC).
-
Remove unwanted Linux services
Disable all the unwanted services and unnecessary services that are running in the background (daemon). Use the following command to stop services at boot time,
# systemctl disable service
# systemctl disable httpd.
-
Enable listen function on all open ports
$ ss –tulpn, executing this command will list all the open ports and associate programs in your network.
-
Do configure firewalls based on Iptables and TCPWrappers
You can avoid a lot of denial of services (DoS) attacks by just configuring Iptables and TCPWrapper firewalls.
-
Enable Disk Quotas
Always segregate and organize the operating system files from the user files. This may sound simple but, in many cases, this helps in a better way of securing the systems. Create separate partitions for FTP and Apache server roots and add noexec, nodev, nosuid
-
Go for a centralized authentication service like OpenLDAP
To avoid forgotten accounts and expired credentials always use a centralized authentication system for client-server configuration. This will help in synchronizing the data between servers and clients. Instead of NIS service, you can implement OpenLDAP to execute the user auth.
-
Kerberos
It is effective in blocking unwanted user activities such as gathering passwords. This is a trusted third-party
-
Use Logwatch/Log checks to
monitor suspicious activities
You need to monitor all your network activities by enabling logwatch/logcheck. This will indicate any suspicious activity around your network. This will also send you a detailed report about the hacker attempt if any.
-
Utilize auditd for system accounting
Auditd is designed to record every system activity across the disk. It helps in knowing the details of the event like who has performed this activity, when, and whether it is successful or failed. Learn more about installing and enabling auditd.
-
Utilize Network Intrusion Detection System
Before setting up the system in a live production environment, do always install a network intrusion detection system (NIDS) like AIDE or rkhunter
-
Disable USB/Firewire/ThunderBolt
devices
You need to disable the open ports as they are more vulnerable to attacks even remotely.
-
Use external storage such as opensource NAS servers for data backup
Always back up data and we have many open-source network-attached storage facilities to make a copy of your sensitive data.
-
Abiding with Security Standards such as HIPAA
Last but not least, always adhere to security standards. This will help you to stay on top of cybersecurity measures.
Wrap Up
We hope this quick explainer gives you a better understanding of









