Post Credit: Ricoh Danielson
Ransomware is rapidly becoming a favoured mode of attack by hackers due to the ease with which it can be deployed. The most popular form of ransomware is Blackcat, a service that allows anyone to take control of web-based systems and demand cryptocurrency ransom in exchange for providing back control.
In this post we will learn some techniques that defenders can deploy to protect against an attacker deploying Blackcat on their network.
How to defend against ransomware such as Black Cat?
The more we move forward into 2022, the more we become aware of not only how to conduct risk mitigation, but also how to conduct cyber ransomware mitigation and the in-depth understanding of it. In light of new cyber ransomware, we need not only to have a defensive proactive plan but also to ensure that we understand our adversaries’ technical capabilities. Let’s discuss more on the extraction part moving forward.
We can see the below expects of ransomware as a service.
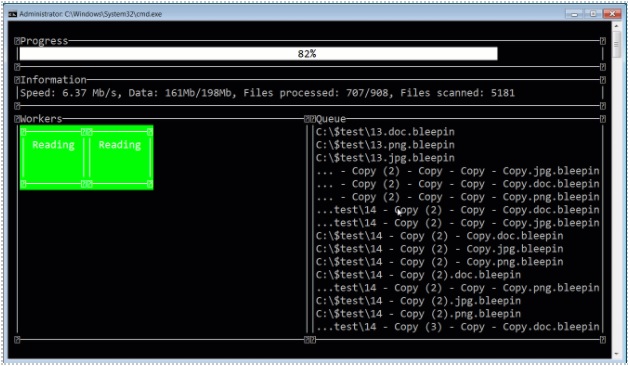
Example of extraction
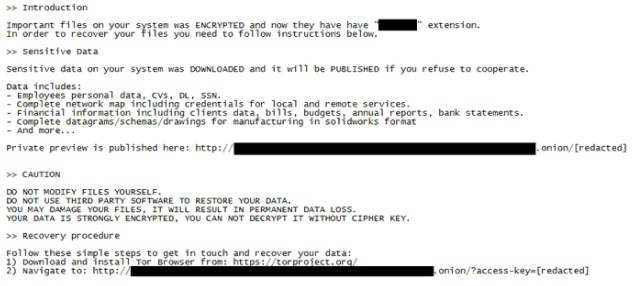
Example of Ransomware letter below
Technical Requirements to conduct Live Box digital Forensics
The investigative techniques used during a digital forensic investigation can be very different from traditional investigations that rely mostly on witness statements and other direct evidence. Technological advances have greatly expanded the available means of collecting data, but also raise legal questions about the admissibility of evidence collected in the field. The collection of digital evidence, particularly live digital evidence using a process called “live box forensics,” involves many issues that are not commonly addressed by the established rules for document and object preservation. The purpose of this article is to help investigators to understand the potential risks involved in capturing live digital evidence. Also, this post will summarize several potential risks and suggest ways to mitigate them by identifying and implementing legal requirements as well as best practices.
The exploitation of the public keys are a common factors is which the threat actor leverages keys that are not just up to par when it comes to security. Most specifically VMware ESXi virtual machines are targeted along with the snaphots.
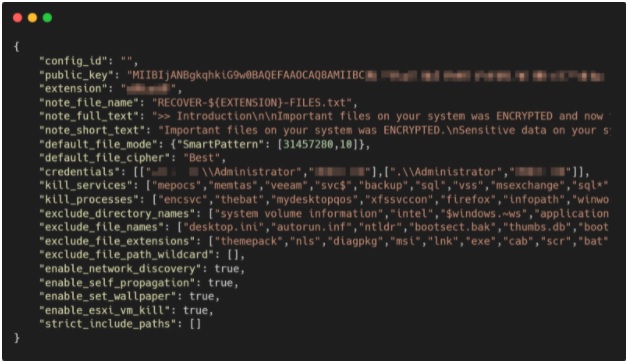
Something to note is that the location of %SYSTEM32%DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} is where most of the common directory. CVE-2016-0099 is also used to get back the login bypass.
Another area to look into is the reg edit in which provides great information of the parameters within the reg edit directory reg add HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters /v MaxMpxCt /d 65535 /t REG_DWORD /f.
Understanding these data points, IOCs, and items of interest can be achieved via a few different means. Either EDR and some short of end points can yield these high amounts of data. If we are going to do this via manually, we can see in the above expects that extraction the path ways is a vital process in which will help the cyber security professional.
Why are we choosing manual process over tools might be a good idea and vis versa
The manual process of finding the IOC we would have to dive deep into a few areas. Let’s look at local path in which are of interest. %USERPROFILE%DesktopRECOVER-<ENCRYPTED_FILE_EXTENSION>-FILES.txt.png. Determining the VMWARE ESXI behavior is another process to ensure we are capturing the abnormal behavior that is indicative of these threat actors. If we are window basing this discovery then the process of understand the DLL level along with process ID. %SYSTEM32%DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}
In this location can determine the process ID that can lead us to where other artifacts may reside. Some of these artifacts can also yield hashes that can validate these threat actors.
Windows Hashes
- 0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479
- 13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31
- 15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed
Linux hashes
- 3a08e3bfec2db5dbece359ac9662e65361a8625a0122e68b56cd5ef3aedf8ce1
- 5121f08cf8614a65d7a86c2f462c0694c132e2877a7f54ab7fcefd7ee5235a42
- 9802a1e8fb425ac3a7c0a7fca5a17cfcb7f3f5f0962deb29e3982f0bece95e26
Now that we have used a manual process to conduct extraction of the vital this will be a matter of correlation of the known and unknown methods of attaching. Understand what processes were exploited, along with how these where the threat actors might be heading based on the other following processes. As the threat actors move forward, they usually follow a set of attack approaches.
Accessing Live box forensic for Black Cat Ransomware
As we are doing forensics on the devices, the above flow of the threat can capture great IOCs and other items for the investigation. When we are doing live box forensics following the process of the incident response framework. By this point we would have isolated the device we need to pinhole the communication to ensure there is a contract two-way talk back to the endpoint. This will ensure that we are there is no forward and or material movement from the threat actor. Containment is key during handling this type of ransomware. A critical part of the incident response.
Analyzing findings and data element of a live digital an active IR or hunt
Now that we have the data, IOCs, and other items of interest we need to analyize the data. We are going to be looking for the “leave behinds” .
It is possible that some things leave clues for us, such as this statement. As we can see that the threat actor used encryption tools, more than likely used the already installed tools such as but not limited to Microsoft encryption.
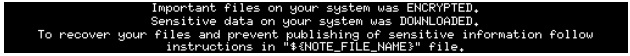
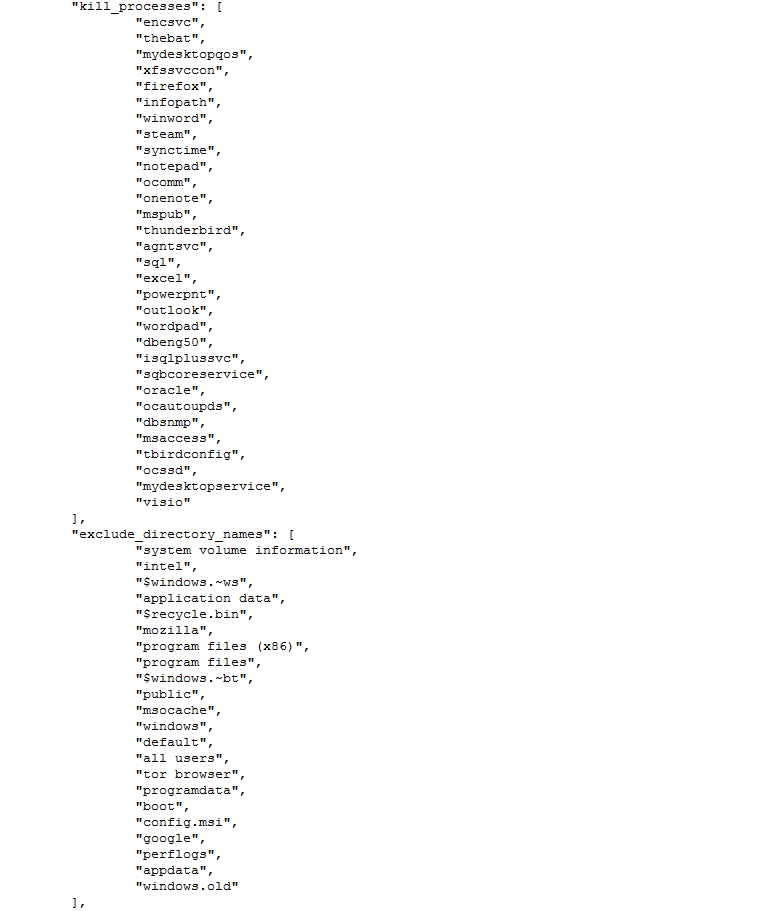
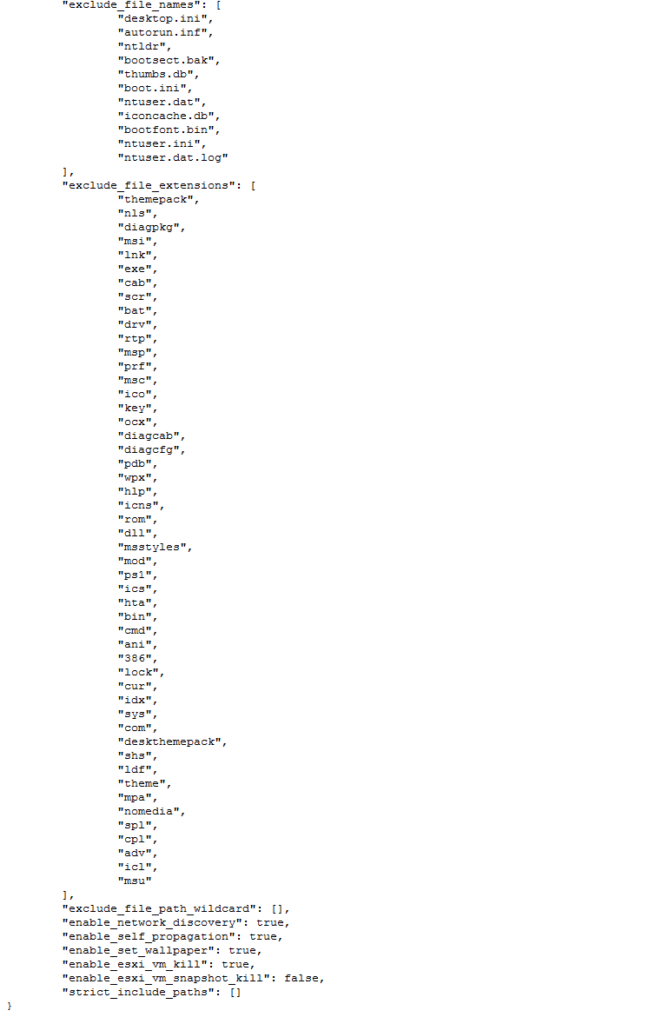
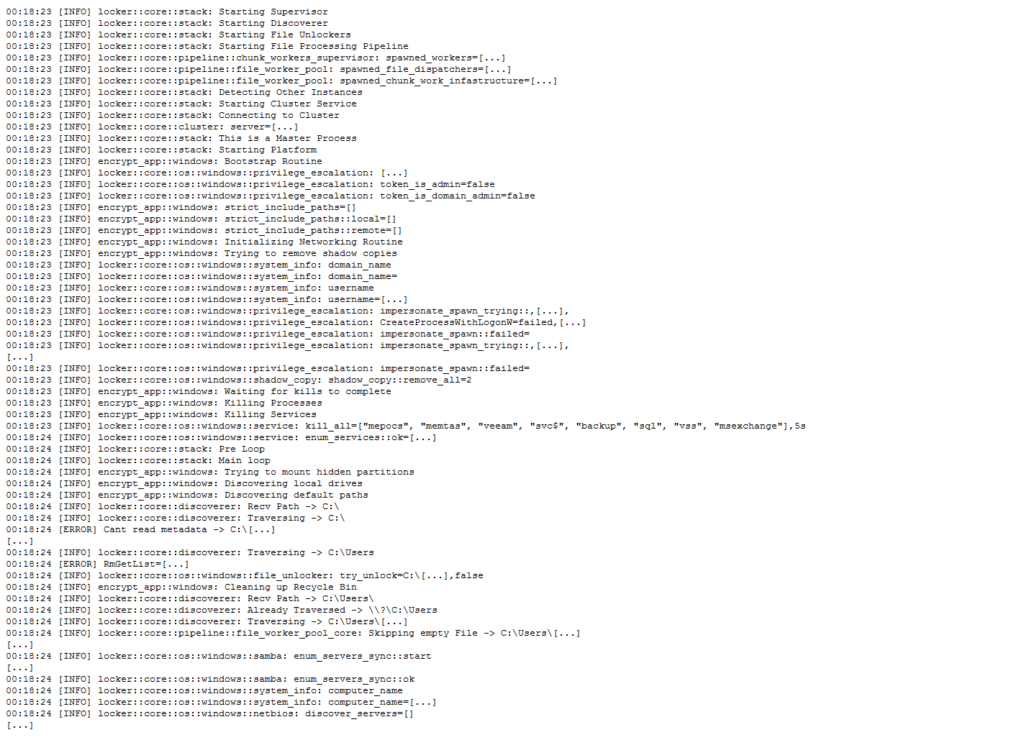
If we follow the process, there is a lot of “kill” actions that take place during the execution of the assembly execution. In analyzing these assembly lines, we also gain a better understanding of the components of the different applications that are also being considered as a part of the compromise stages of the attachment.
Summary
Remember, IR is a very important tool for threat analysis. It allows you to capture data at the cyber level which makes it particularly valuable during real-time analysis, or during analysis of a “live box” and the subsequent analysis that can lead to actual attribution.
Understanding the data elements, as we close this one out, is important, but understanding where the threat actors are headed next and what has been expelled is even more critical. It is important to consider what processes, exes, and other vulnerabilities can be exploited as we perform further discovery on the assembly. The critical points must be broken down in order for us to convey these to cyber security lawyers and other executives.








