LockBit 3.0: A Deeper Look
After last week’s whistle stop tour on how LockBit 3.0 has changed to infect and lock up systems in a new way, we’re now going to take a look at the specific tactics, processes, and procedures that the malware uses to infiltrate the machines of unwitting victims. Thanks to research from @petrovic082, another sample was analyzed on VirusTotal – this time, including plenty of information about the adopted PowerShell from BlackMatter, the injection DLL, and the obfuscation used to defend the script.
The Processes
Three different processes run when LockBit has infected a system:
- Powershell.exe (A PowerShell executable runs)
- CMSTPLUA (see em es tee pee el yoo ay runs and launches multiple subprocesses that start to encrypt files and upload the ransom background image)
- printfilterpipelinesvc.exe (An executable called print filter pipeline es vee see launches a OneNote document which
In combination, these launch and lock down the system in a grand total of 60 seconds. That’s pretty rapid, but it’s evident that this third iteration of LockBit has been improved to increase the amount of suffering it can dish out to an IT team. With that in mind, let’s have a look at the process in action.
Process #1: PowerShell
After initial infection, a PowerShell command – -file – is launched. Pulling the fff[.]ps1 file from the dropped .dll, the payload quickly gets to encrypting the system files.
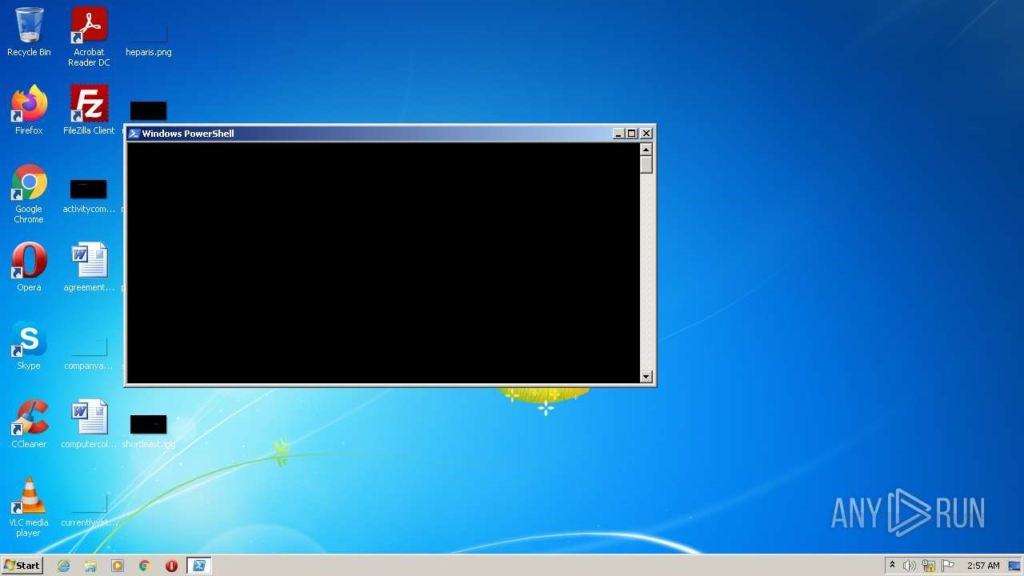
If you want a closer look at how this PowerShell script functions, here is a piece of the deobfuscated code.
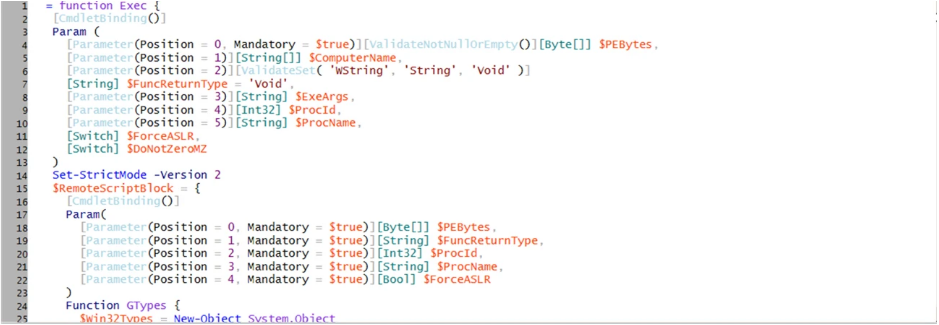
The most interesting part of a full code analysis, however, is the main function – see the picture below to see how the LockBit ransomware sets off its malicious payload:
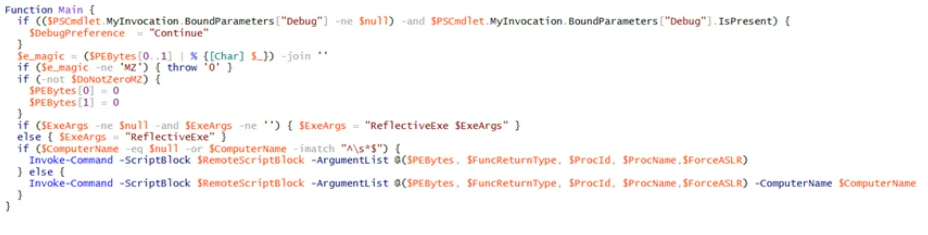
And now compare it with the main function from BlackMatter:
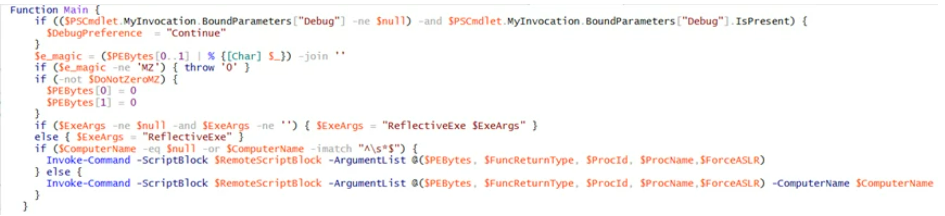
Not that different, right? Although no one can know everything about every single piece of malware out there, a comprehensive understanding of malware types and a robust security posture will help you more than you think it will.
Process #2: Encryption
As shown in the image below, a stylized B-like symbol is added in place of the existing file images and the file type is changed to stop the victim from accessing their files. As evidenced in @petrovic082’s breakdown, this process is practically instantaneous – when the PowerShell command runs, a standard system will be locked down easily.
Process #3: Ransom
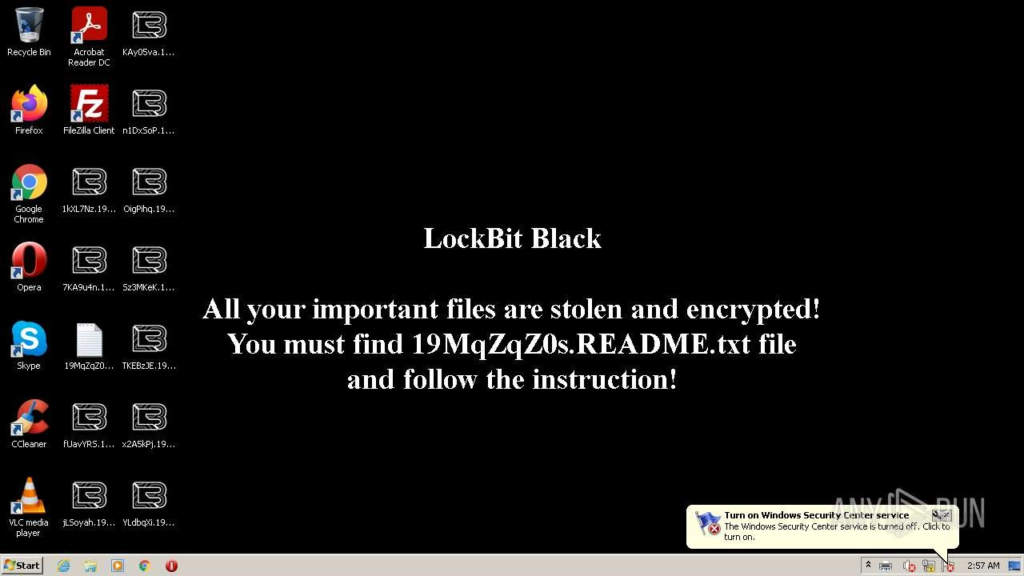
What would ransomware be without a ransom note? After the files are encrypted, LockBit 3.0 launches the ominous black screen and directs the victim to the installed ransom note (19MqZqZ0s.README[.]txt).

How do I protect my organization?
It’s never enough just to know what is at the gates – you have to know how to battle it. Thankfully, some standard best practices are effective in stopping LockBit 3.0 from locking down your systems and stopping the bad guys get away with it.
- Employ an effective backing up system which allows you access to all key files in the case of a ransomware attack. Example protocols could include the 3-2-1 rule.
- Improve your defenses against social engineering attacks, such as using software to filter outside emails entering the organization. As this malware has been shown to use email-based phishing attacks to spread, locking down emails is the easiest way to improve defenses.
- Patch, patch, patch, update, update, update – as always, keep your systems and anti-malware / anti-virus up to date to stop the ransomware onto your systems. Find the indicators of compromise below to strengthen your defenses before it’s too late!
Indicators of Compromise
As always, staying ahead of the game is key to surviving adversarial developments. That’s why we’re providing the following IoCs to help you spot LockBit 3.0 before it becomes a problem for you and your team.
SHA-256
80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce
a56b41a6023f828cccaaef470874571d169fdb8f683a75edd430fbd31a2c3f6e
d61af007f6c792b8fb6c677143b7d0e2533394e28c50737588e40da475c040ee
506f3b12853375a1fbbf85c82ddf13341cf941c5acd4a39a51d6addf145a7a51
c597c75c6b6b283e3b5c8caeee095d60902e7396536444b59513677a94667ff8
917e115cc403e29b4388e0d175cbfac3e7e40ca1742299fbdb353847db2de7c2
Detection names
Ransom.Win32.LOCKBIT.YXCGD
Ransom.Win32.LOCKBIT.YXCGFT
Ransom.Win32.LOCKBIT.YXCGD
Ransom.Win32.LOCKBIT.YXCGKT
Ransom.PS1.LOCKBIT.YXCGTT
Ransom.Win32.LOCKBIT.YXCGT








